Wayfinder is hosted in AWS
This article covers granting Wayfinder access to an Azure Subscription (target subscription) when Wayfinder is installed in AWS (home account), and you're using Wayfinder's credentials for authentication.
Jump to the Quick Start section for steps on how to create a new Azure Cloud Access.
Overview
Workflow
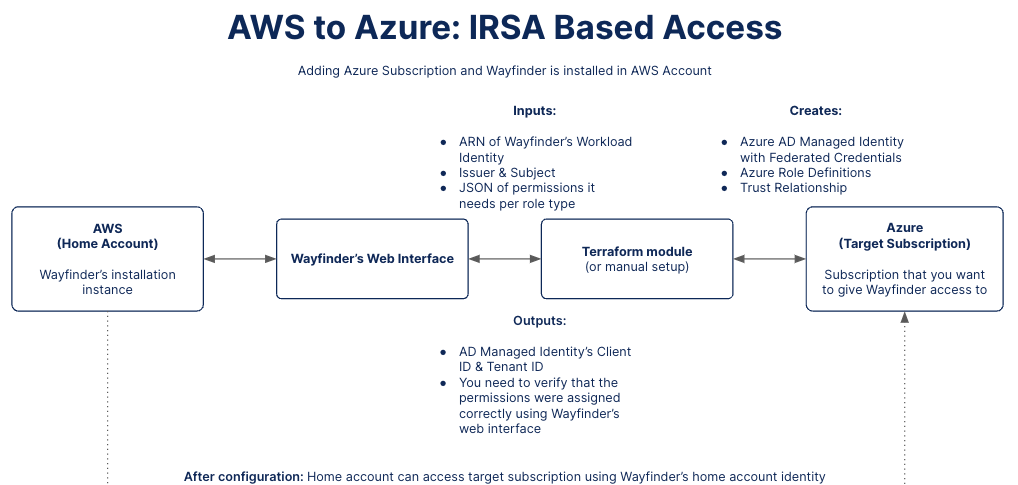
Wayfinder's web interface provides you with the ARN value of Wayfinder's Workload Identity and an outline of the permissions Wayfinder need to manage cloud resources in the target account.
Use Wayfinder's terraform module to create the necessary Azure AD Managed Identity with Federated Credentials, Azure Role Definitions and Trust Relationship in the target subscription. Wayfinder's ARN is needed to create the trust relationship between the home account and target subscription. The permissions are needed to create the Azure Role Definitions. See a full list of Wayfinder's terraform module input values. You can also do this configuration manually.
Wayfinder's terraform module returns the Client ID of the Azure AD Managed Identity with federated credentials, that were created in the target subscription. This Client ID needs to pasted in the respective fields in Wayfinder's web interface or the relevant CRD fields (Kind:CloudAccessConfig) if you're using Wayfinder's CLI.
After you apply the cloud access configuration, either using Wayfinder's web interface or CLI, then Wayfinder will be able to use its own credentials to connect to the target subscription.
Home Account Details
Wayfinder's Workload Identity is the ARN of the AWS IRSA Role which trusts Wayfinder's Kubernetes Service Account. If you installed Wayfinder using Wayfinder's install terraform module, this will have been created for you during the install. If not, you need to provide the ARN value of Wayfinder's Workload Identity as a value to the Helm chart on installation.
You use this ARN value when you configure a trust relationship between the home account and the target account.
Use Wayfinder's web interface to locate Wayfinder's Workload Identity or look it up manually in AWS.
Target Subscription Details
You need to provide Wayfinder with the Client ID of the Azure AD Managed Identity with federated credentials in the target subscription.
The Azure AD Managed Identity with federated credentials in the target subscription needs to be correctly configured with the Azure Role Definitions containing the permissions Wayfinder need and a Trust Relationship to outline the trust between Wayfinder's workload identity (home account) and the Azure AD Managed Identity (target subscription).
Use Wayfinder's terraform module to configure the Azure AD Managed Identity with federated credentials on your behalf or create it manually in Azure. Wayfinder's web interface displays the input values for the terraform module on the sidebar when you reach the Step 4 - Permissions section. CLI users can use the wf describe cloudaccess --cloud-identity CLOUDIDENTITY-NAME --to-cloud TARGET-CLOUD --for-type ACCESS-TYPE --for-stage STAGE-NAME --for-workspace WORKSPACE-KEY -o tfvars command.
CLI Quick Reference
| Instruction | CLI Command |
|---|---|
| Create a workspace (only if Access Type is Kubernetes Cluster Provisioning) | wf create workspace WORKSPACE-KEY -s SUMMARY |
| Create a stage (only if Access Type is Kubernetes Cluster Provisioning) | wf create stage STAGE-NAME -d DESCRIPTION |
| View Cloud Access Configurations | wf get cloudaccessconfig -c CLOUD -w WORKSPACE-KEY |
| Output the Cloud Access Configuration to console | wf get cloudaccessconfig CONFIG-NAME -o yaml |
| Output the Cloud Access Configuration to file | wf get cloudaccessconfig CONFIG-NAME > ./PATH/TO/FILE.yaml |
| Apply the Cloud Access Configuration from file | wf apply cloudaccessconfig -f ./PATH/TO/FILE.yaml |
| View Cloud Permissions | wf get cloudpermissions |
| View the Permissions of the specified Cloud Permission | wf describe cloudpermissions PERMISSION-NAME -c CLOUD -o JSON |
| View input values for Wayfinder's terraform module | wf describe cloudaccess --cloud-identity CLOUDIDENTITY-NAME --to-cloud TARGET-CLOUD --for-type ACCESS-TYPE --for-stage STAGE-NAME --for-workspace WORKSPACE-KEY -o tfvars |
| View cloud identities | wf get cloudidentities |
| Output the details of the cloud identity to console | wf get cloudidentities NAME-OF-IDENTITY -o yaml |
| Create a cloud identity for Wayfinder's workload identity (You only have to do this once) | wf create cloudidentity CLOUDIDENTITY-NAME --for-workload-identity |
| [ADVANCED USERS] Create a Cloud Access Configuration | wf create cloudaccessconfig [flags] |
Considerations
For each subscription that you want to connect, you need to:
- Decide what type of cloud access you need.
- Decide the scope of the cloud subscription (workspace and stage).
Note that some access types are designated as 'administrative' for configurations that are outside the scope of any particular workspace or stage and are intended for Wayfinder administrators. - Decide what type of authentication method you want to use. This article outlines using Wayfinder's credentials (Azure AD Identity Based Access).
- Give Wayfinder cloud permissions to access cloud resources and perform relevant tasks. At this point you should have already run Wayfinder's terraform module to create the needed configuration and permissions in the target subscription (or have done this configuration manually). You need to verify that the permissions are assigned correctly by using Wayfinder's web interface.
Quick Start: Add a new Azure Cloud Access
CLI Steps
The easiest way to create a new Azure cloud access configuration is to edit an existing one.
- Copy one of the cloud access configuration (yaml) examples or output the yaml of an existing Cloud Access Configuration to file.
- Review the permissions that Wayfinder needs.
- Use Wayfinder's terraform module to configure the target subscription (or do the configuration manually).
- Apply the yaml of the Cloud Access Configuration that you've edited.
Wayfinder's Web Interface Steps
- Select Admin, then navigate to Cloud > Access.
- Select Microsoft Azure.
- Click the Add Azure cloud access button
- You are presented with the Add Azure cloud access page. There are four main sections to complete.
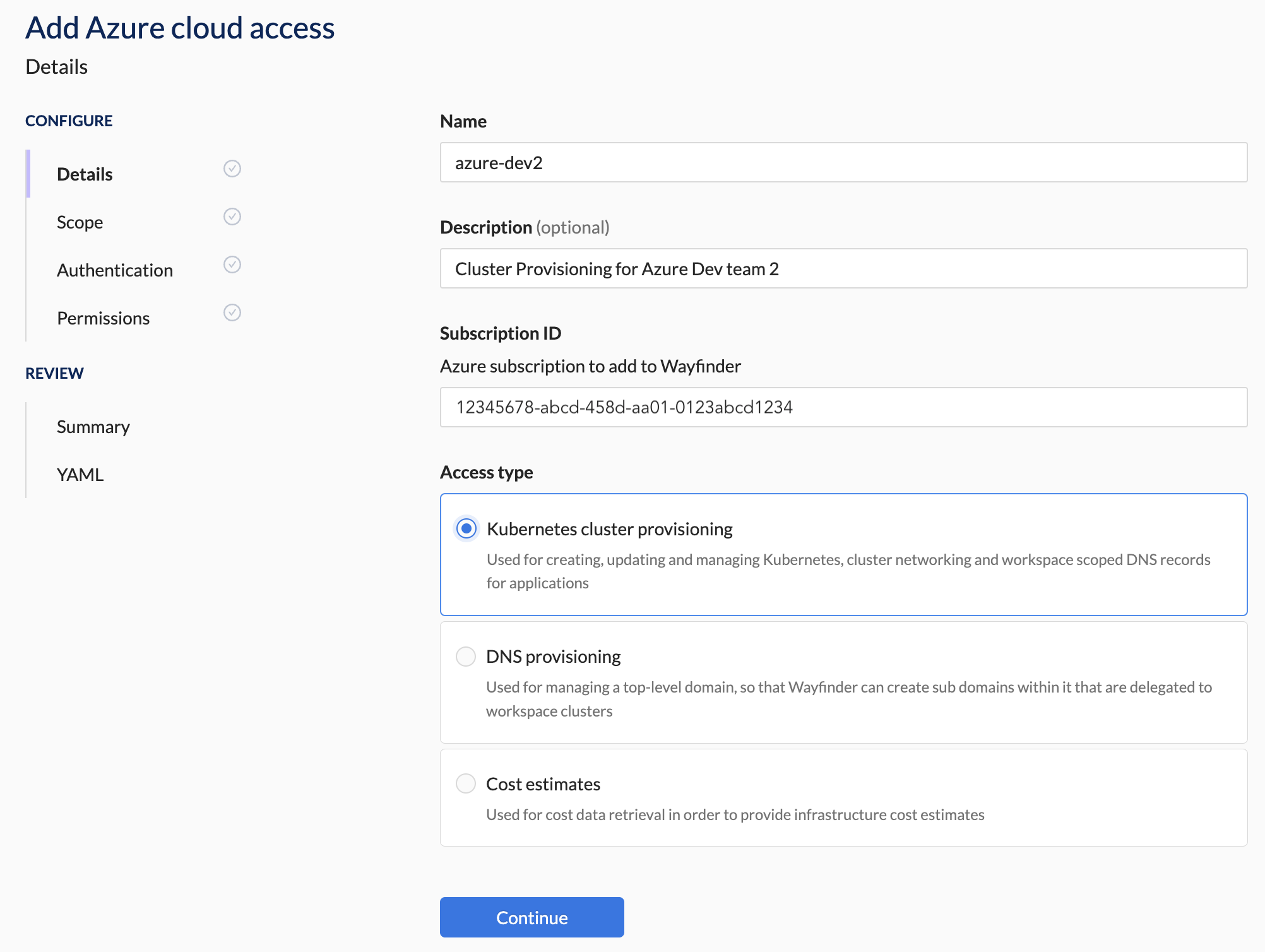
1. Details Section Steps
- Enter the Details for the new cloud access.
- Enter the Azure Subscription ID for the Azure subscription that you want to give Wayfinder access to.
- Select the Access Type that this cloud access connection is for, Kubernetes Cluster Provisioning
Example
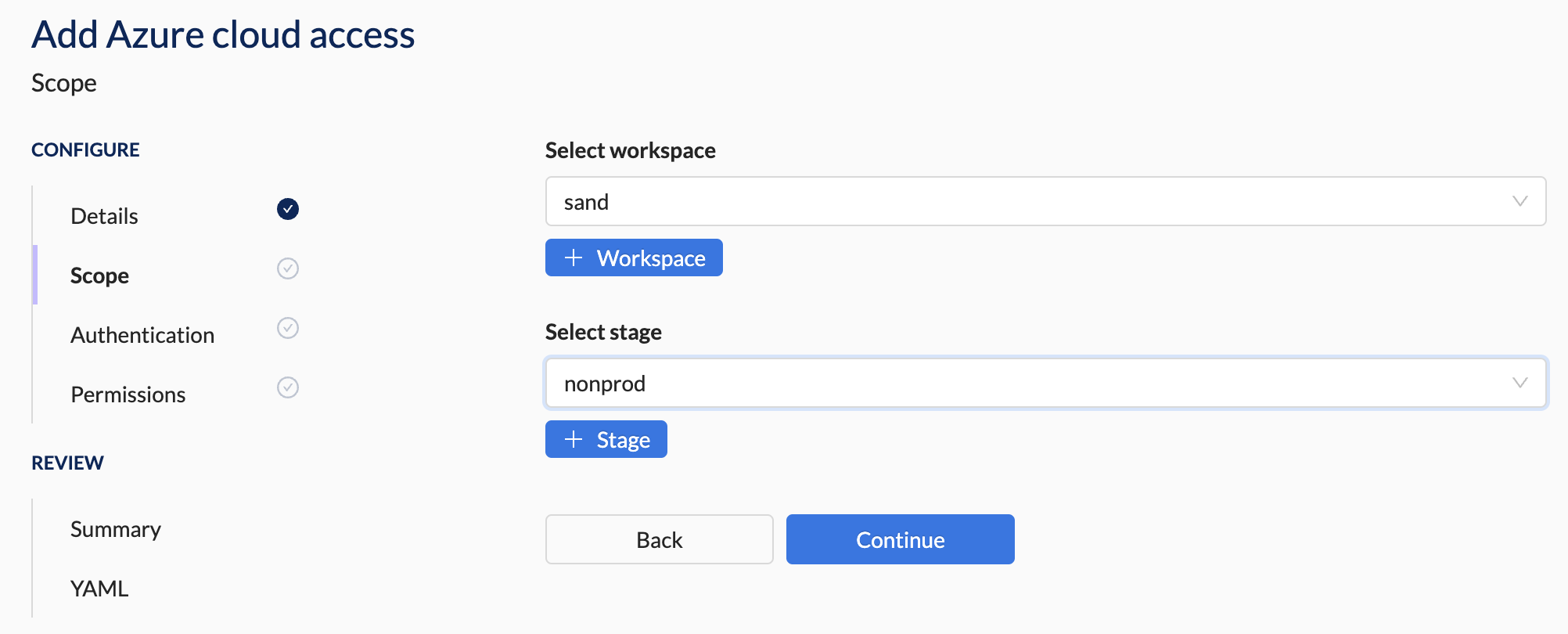
2. Scope Section Steps
- Select a workspace from the drop-down list or create a new workspace.
- Select a stage from the drop-down list or create a new stage.
The Access Type determines if the Scope section is editable or skipped. If skipped then the Scope is designated as 'Platform'.
Example
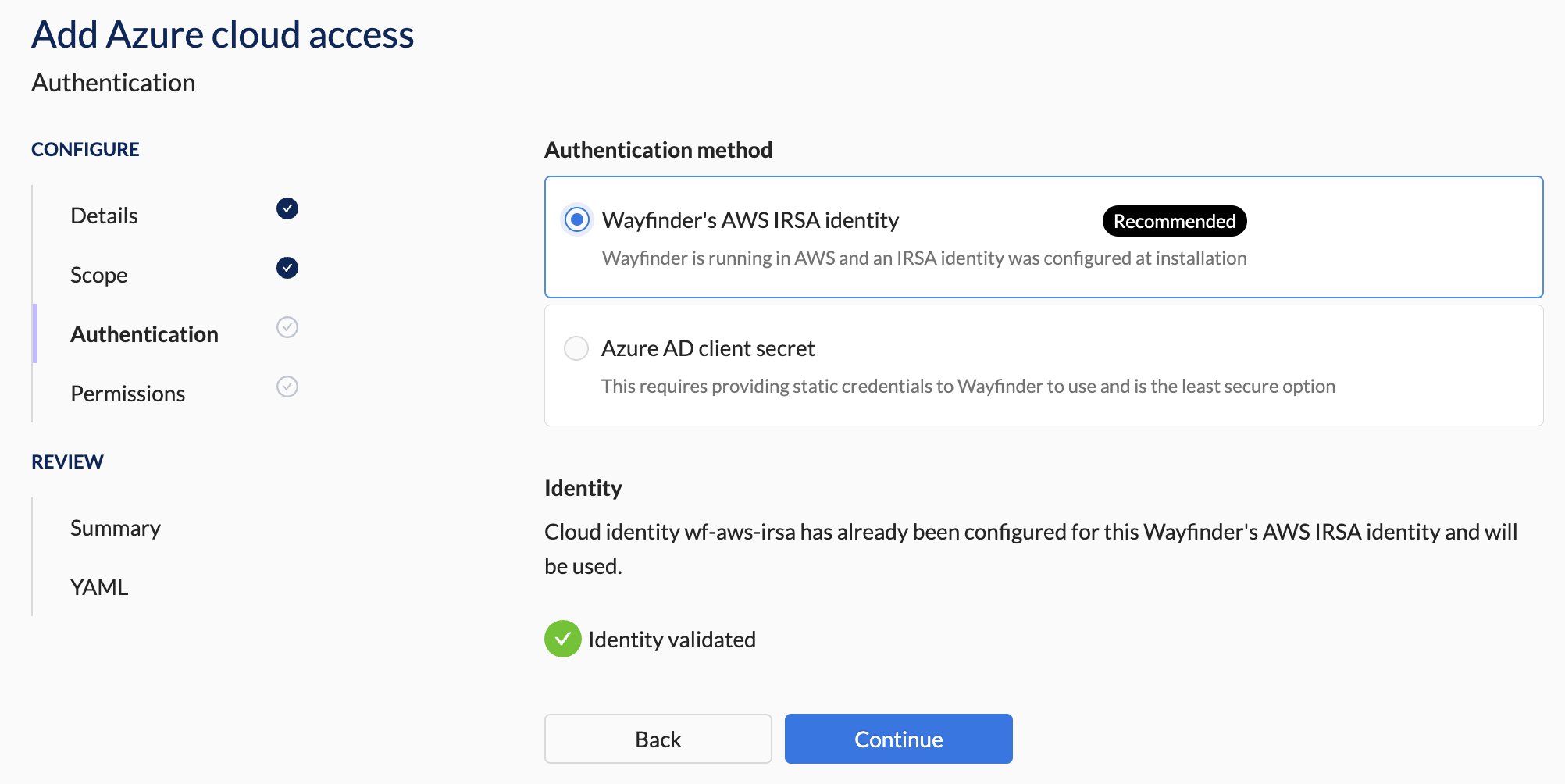
3. Authentication Section Steps
- Select Wayfinder's AWS IRSA Identity as the Authentication Method.
Example
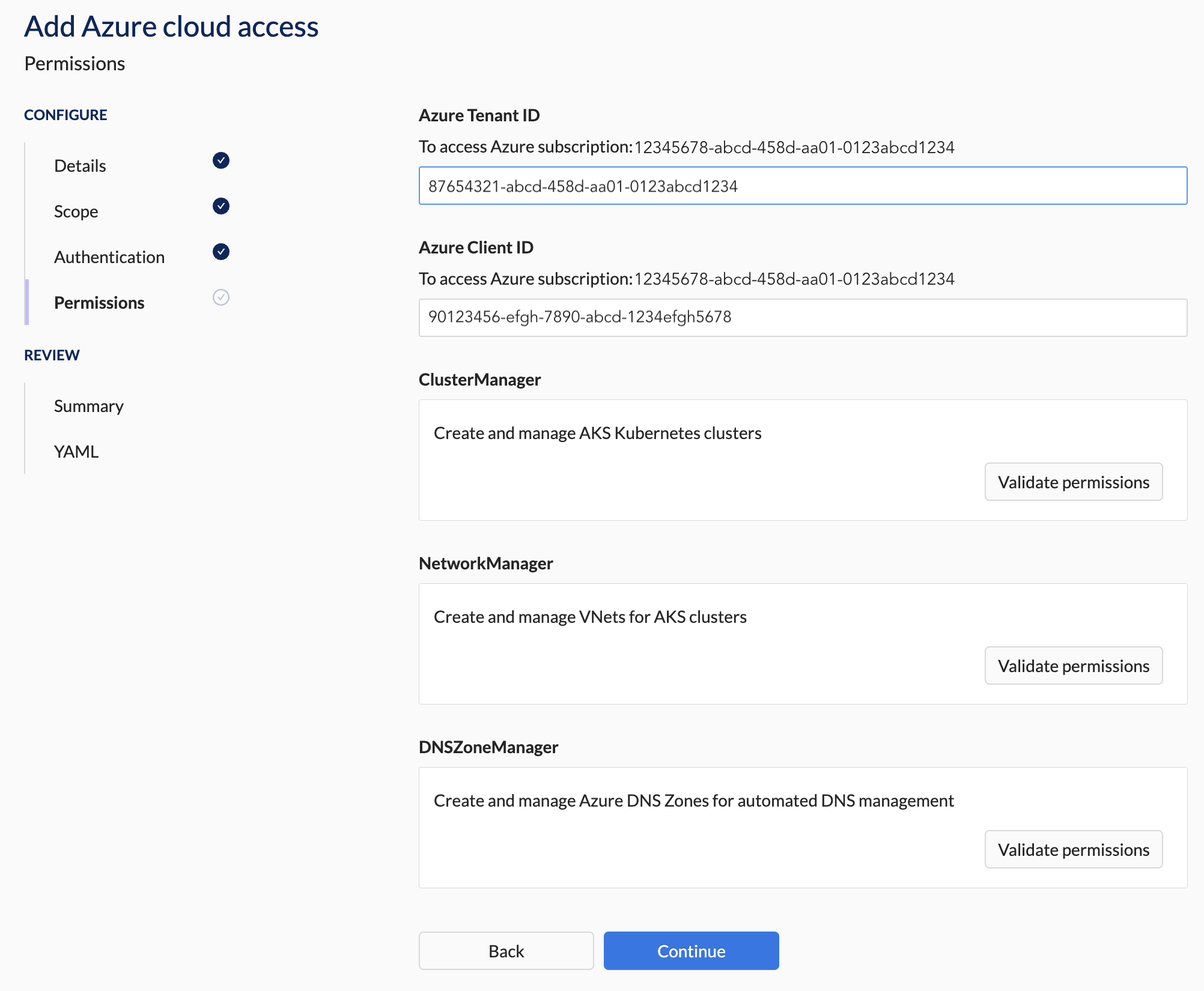
4. Permission Section Steps
You need to either run Wayfinder's terraform module to set up the needed cloud configuration in the target subscription or manually do the configuration. The right-hand panel will provide the needed input values for Wayfinder's terraform module. For more information see the Workflow section.Example of what you'll see on the right-hand panel as input values for Wayfinder's terraform module
resource_suffix = "-app1-nonprod"
enable_cluster_manager = true
enable_dns_zone_manager = true
enable_network_manager = true
enable_cloud_info = false
from_aws = true
from_azure = false
wayfinder_identity_aws_role_arn = "arn:aws:iam::812345678901:role/wf-cloudidentity-aws"
wayfinder_identity_aws_issuer = "https://oidc.eks.eu-west-2.amazonaws.com/id/ABCDF8D2EF45CE1A6FD96E2781310123"
wayfinder_identity_aws_subject = "system:serviceaccount:wayfinder:wayfinder-admin"Example of Wayfinder's terraform module output values
Outputs:
wayfinder_cloudaccess = {
"managed_identity_client_id" = "90123456-efgh-7890-abcd-1234efgh5678"
"managed_identity_tenant_id" = "b87654321-abcd-458d-aa01-0123abcd1234"
}
- Enter the Azure Tenant ID of the target account
- Enter the Azure Client ID of the target account
- Select the ClusterManager's Validate permissions button.
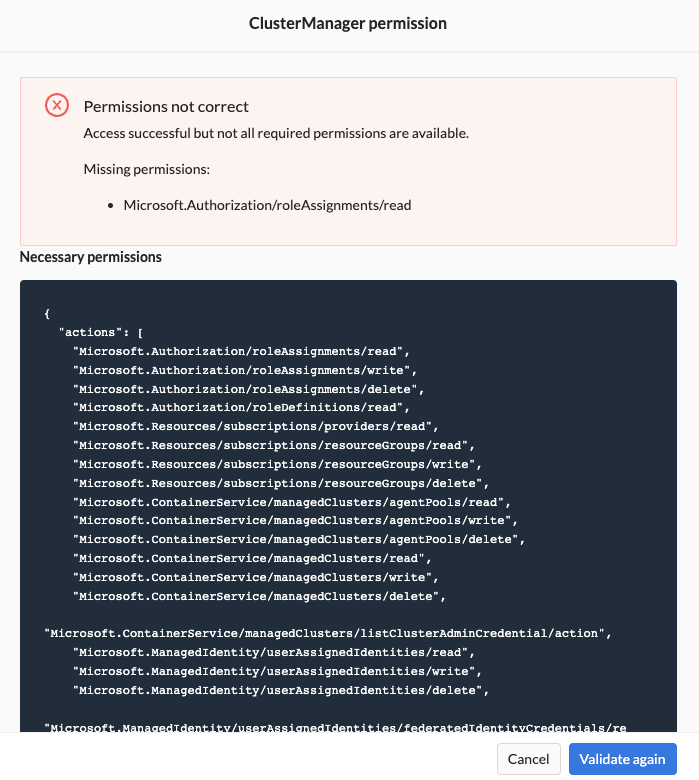
- Click the Validate button. You need to resolve all error messages before you can continue.
- Repeat the steps above for DNSZoneManager and NetworkManager (if applicable for your Access Type).
Example
Fix any errors by either running Wayfinder's terraform module or update the permissions manually.
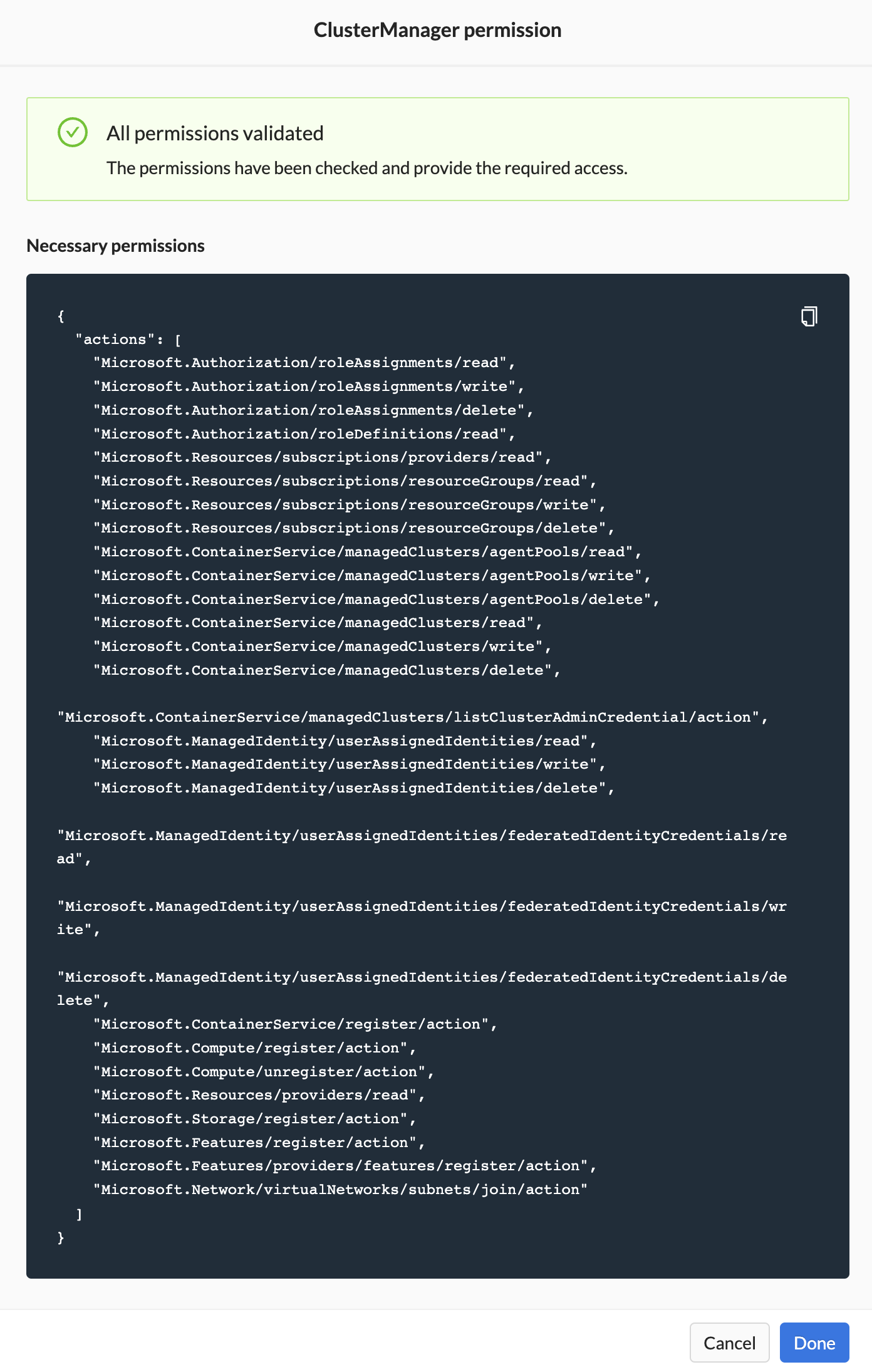
You will be able to proceed once the permissions are validated successfully.
All permissions must be validated successfully before you can proceed to the Summary section.
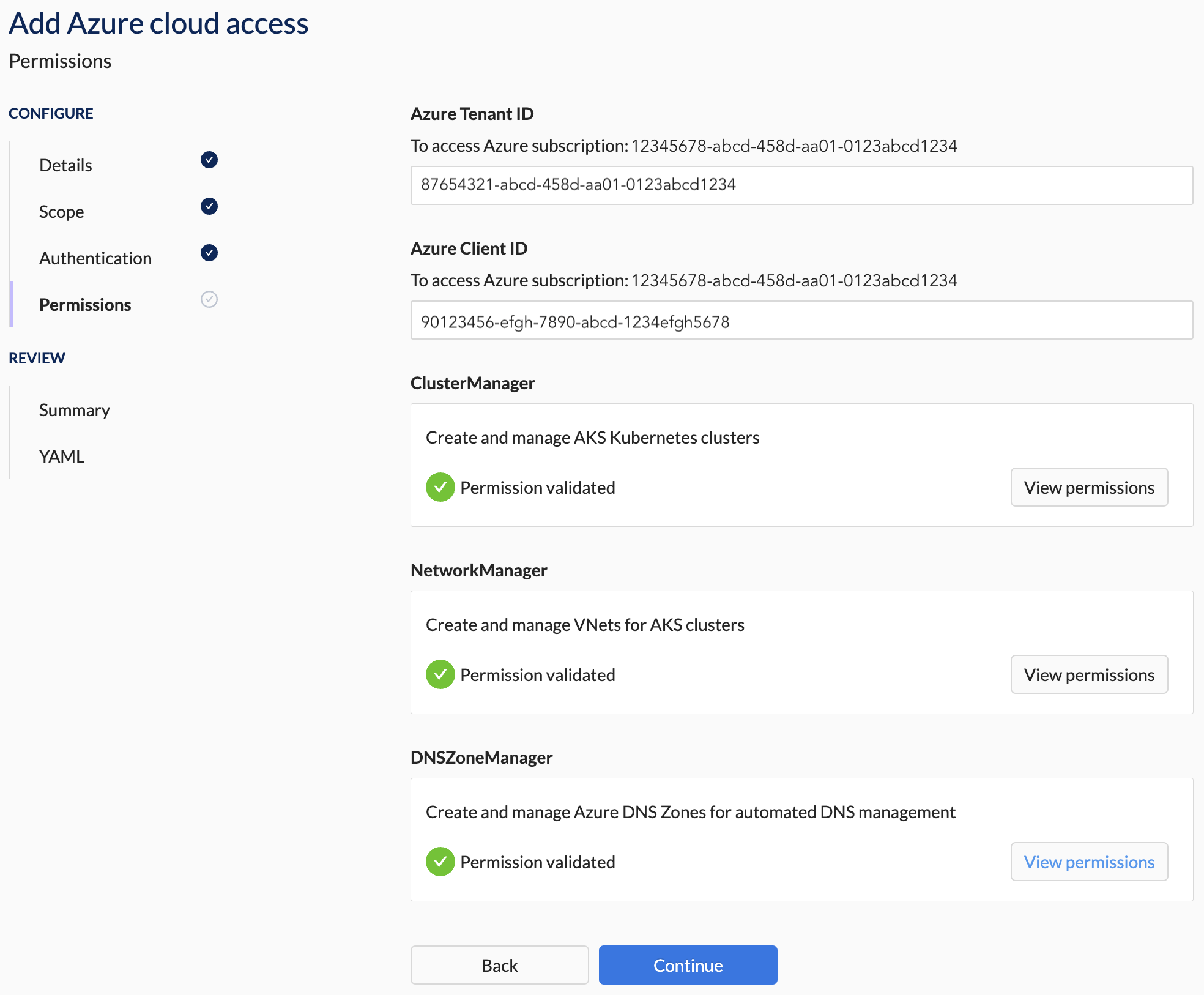
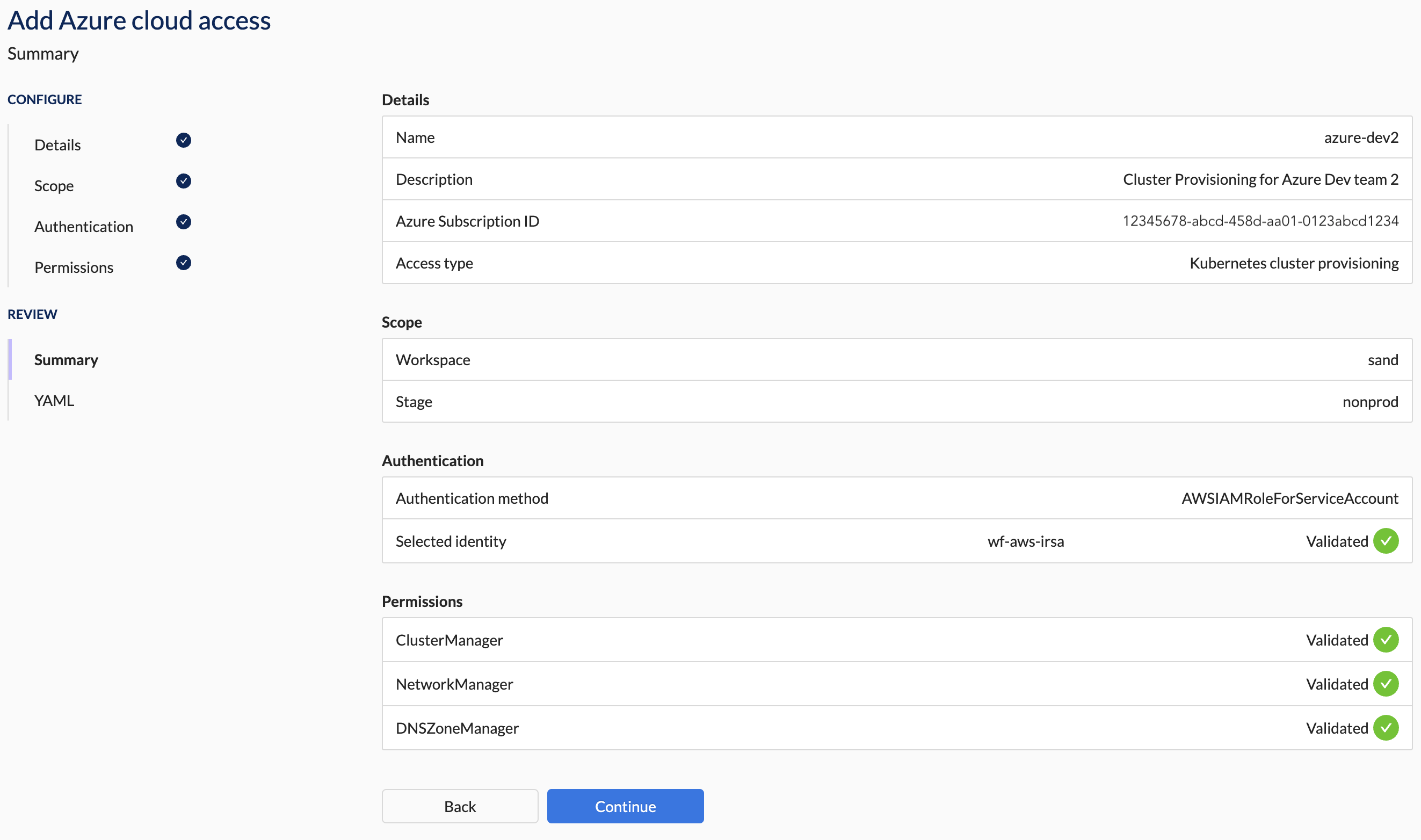
5. Summary Section Steps
- Verify that all the details are correct.
You will not be able to apply the configuration if any of the validations failed.
Example
6. YAML Section Steps
- Press the Apply button to apply the configuration.
- Alternatively, download the YAML and apply it using Wayfinder's CLI or your CI pipeline.
Azure Cloud Access Properties
The following sections outline the properties that you'll need to connect your subscription to Wayfinder. CLI users can refer to the information in this section to understand how the settings from Wayfinder's web interface correlate with the respective YAML files.
Refer to the previous section for the quick start steps on how to add a new Azure Cloud Access.
Details Section Properties
This section specifies the general properties and access type for the Azure Subscription you're adding.
| Field | Description |
|---|---|
| Name | The name of this cloud connection |
| Description | A meaningful description for this cloud connection |
| Azure Subscription ID | Specify the Azure Subscription ID that you're connecting to. |
| Access Type | The type of automation Wayfinder should provide. Option(s):
|
Each cloud account you connect is for the purpose of one of the 'Cloud Access Type' and each will have a different scope.
Scope Section Properties
When you've selected the Access Type as 'Kubernetes Cluster Provisioning', you need to set the scope to control where you want to provide the access to. This section is not visible for other Access Types.
What is the difference between a workspace and a stage?
- A workspace is where teams provision and manage applications, environments, clusters, and cloud resources.
- A stage is used to isolate and test resources at the infrastructure level such as production or development.
What is 'platform' scope?
Access types that are designated as 'platform' are for configurations that are outside the scope of any particular workspace or stage and are intended for the use by Wayfinder administrators.
| Access Type | Description | Scope |
|---|---|---|
| Kubernetes Cluster Provisioning | Used for creating, updating and managing Kubernetes, cluster networking and workspace scoped DNS records for applications. | Workspace and Stage |
| DNS Provisioning | Used for managing a top-level domain, so that Wayfinder can create sub domains within it that are delegated to workspace clusters. | Platform |
| Peering | Used for peering automation. Wayfinder can accept peering requests enabling connectivity between Wayfinder provisioned Kubernetes clusters and any external VPC network. | Platform |
| Cost Estimates | Used for cost data retrieval in order to provide infrastructure cost estimates. | Platform |
| Private Links (Azure only) | Used when Wayfinder is installed in Azure, and you need to grant it access to a private cluster within a private virtual network (VNet) | Platform |
Create a new workspace
You can create a new workspace if the existing ones don't meet your needs.
| Field | Description |
|---|---|
| Select workspace | The workspace that can use this cloud account. |
| -- New workspace (button) | Creates a new workspace. |
| --- Name | The name for the new workspace. |
| --- Description | Meaningful description for this workspace. |
| --- Key | Unique 3-5 character identifier for the new workspace. |
CLI Examples
Create a workspace
FORMAT: wf create workspace WORKSPACE-KEY -s SUMMARY
EXAMPLE:
wf create workspace sand -s "My sandbox workspace"
◉ Waiting for resource "org.appvia.io/v2beta1/workspace/sand" to provision (background with ctrl-c)
✔ Successfully provisioned the resource: "sand"
Create a new stage
You can create a new stage if the existing ones don't meet your needs.
| Field | Description |
|---|---|
| Select stage | The stage that can use this cloud account. |
| -- New stage (button) | Creates a new stage. |
| --- Name | The name for the new stage. |
| --- Description | Meaningful description for this stage. |
CLI Examples
Create a stage
FORMAT: wf create stage STAGE-NAME -d DESCRIPTION
EXAMPLE:
~ wf create stage nonprod -d "non production stage"
✔ Successfully requested the resource "org.appvia.io/v2beta1/stage/nonprod"
✔ Successfully created the stage
Authentication Section Properties
This section specifies the properties to authenticate your Wayfinder instance with your cloud account.
| Field | Description |
|---|---|
| Authentication method | The method in which Wayfinder will authenticate itself to the account. Option(s): - Authenticating without credentials -- Allows Wayfinder to authenticate itself using its own identity instead of static credentials. --- Note: For fresh installs you need to Create a New Workload Identity (once off task) -- Option presented to you will depend on where Wayfinder's instance is installed: --- IRSA Based Access (when Wayfinder's instance is installed in AWS) --- See respective documentation for when Wayfinder is installed in Azure or GCP -- Auto-detection: Presents the ARN value of Wayfinder's Workload Identity - Credential-based Access -- Please see 'Use Azure static credentials' |
Create a new Workload Identity
Note that you only need to do this once.
You need to create a cloud identity for Wayfinder's workload identity when you have a fresh installation of Wayfinder, it is the first time that you're adding a Cloud Access and you're using credential-less authentication.
Use wf create cloudidentity CLOUDIDENTITY-NAME with the --for-workload-identity -c CLOUD flags to create the cloud identity.
wf create cloudidentity wf-aws-irsa --for-workload-identity -c aws
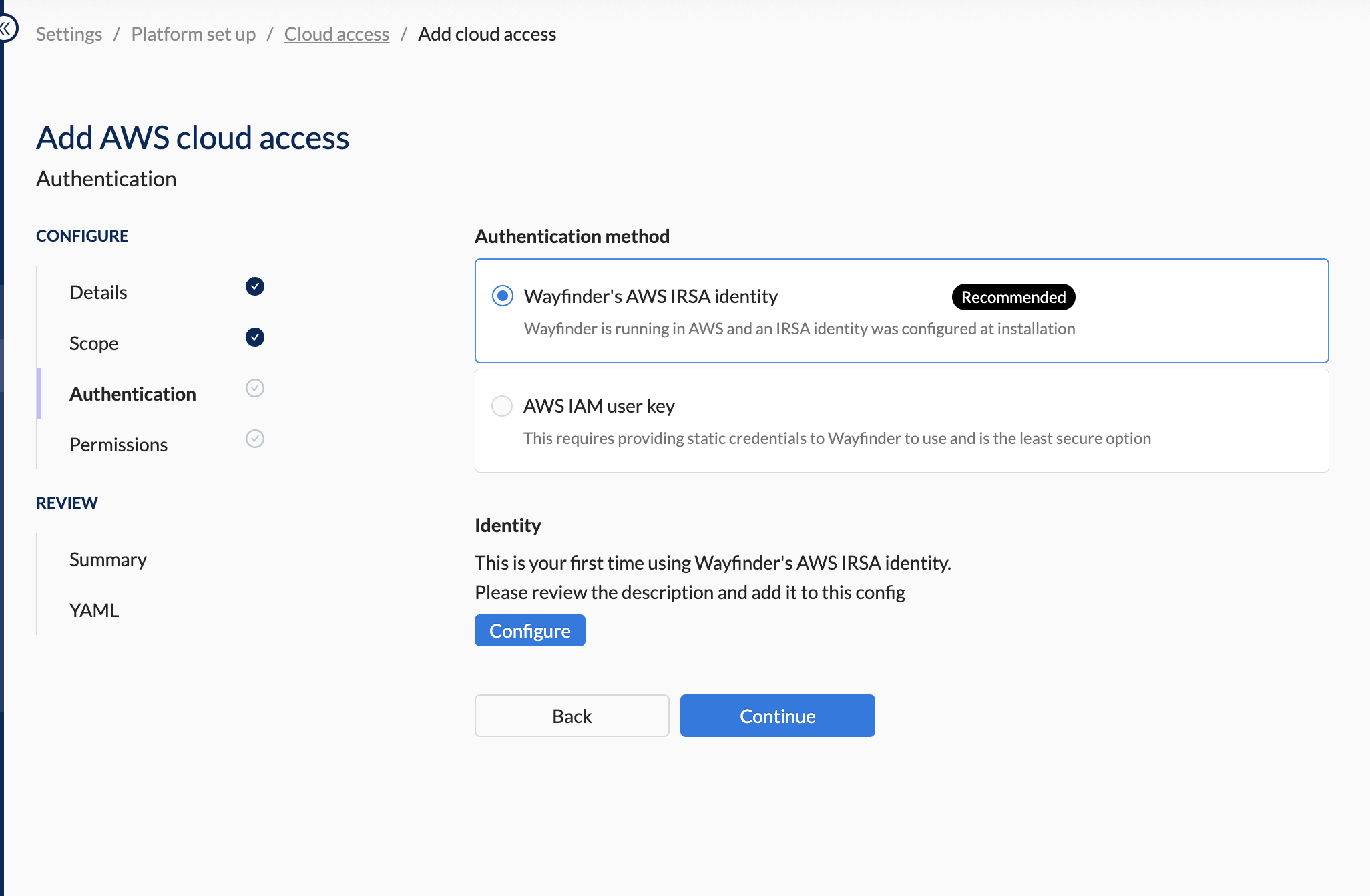
In Wayfinder's web interface:
- Create a new Cloud Access and progress to the Authentication page (see Quick Start guide for steps)
- Select Wayfinder's AWS IRSA ID as the authentication method
- Click the Configure button. Note that you will only see this button if you haven't previously created a cloud identity for Wayfinder's workload identity.
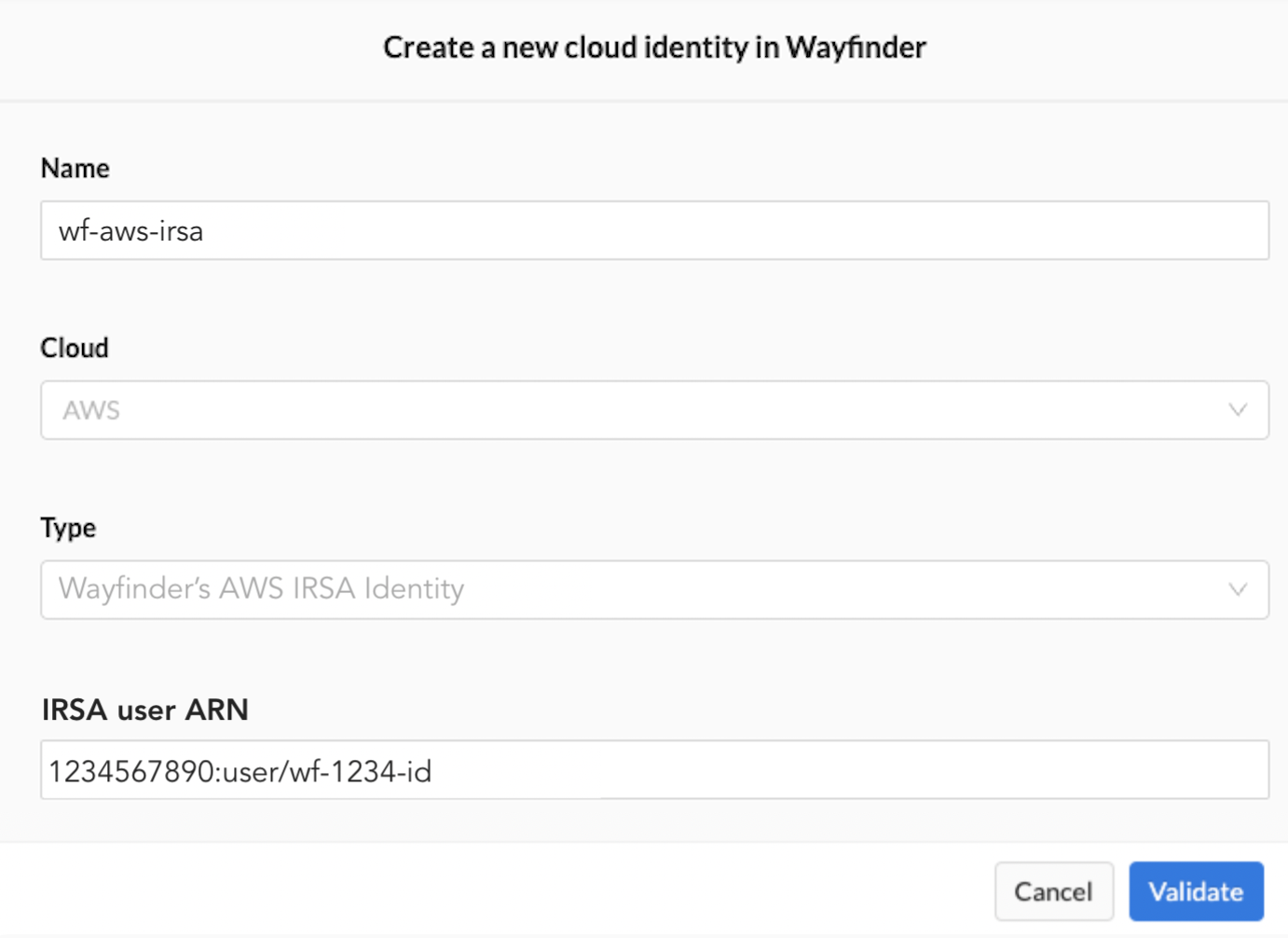
- Fill in the details as outlined in the properties table below.
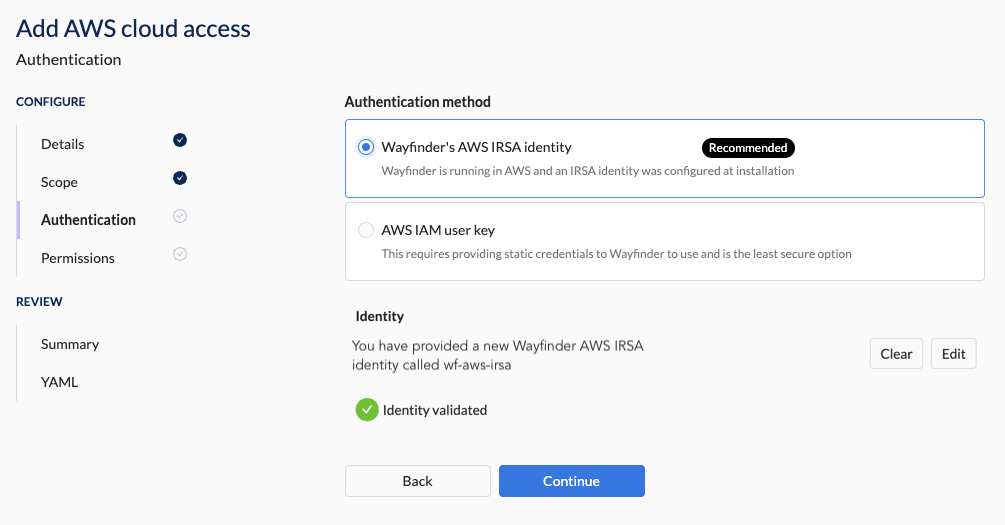
- Click on the Validate button. All validation must pass before you can continue.
- You will see a green tick mark that confirms that validate passed.
| Field | Description |
|---|---|
| -- Name | Name of the new cloud identity |
| -- Cloud | The cloud in which the identity will be created (read-only value). Value(s): - AWS |
| -- Type | The type of identity to create. Option(s): - Wayfinder's IRSA Identity (Read-only value) |
| -- IRSA user ARN | Value of the IRSA ARN of Wayfinder's Workload Identity |
| -- Validate (button) | Validates that Wayfinder can use that cloud identity |
Example
Fill in the details.
You can proceed once all the validation passed.
Permissions Section Properties
This section specifies the properties that grants the necessary permissions to Wayfinder. These permissions allow Wayfinder to create, manage and update cloud resources in the cloud account you specified in the previous section.
| Field | Description |
|---|---|
| Tenant ID | The Tenant ID of the target subscription |
| Client ID | The Client ID of the target subscription |
| Cluster manager | Permissions that create and manage EKS Kubernetes clusters. |
| - Necessary Permissions | JSON outlining the needed permissions for Cluster Manager. Use Wayfinder's terraform module to assign permissions or create it manually. |
| - Validate (button) | Verification that the needed permissions were assigned correctly. |
| DNS management | Permissions that create and manage DNS records. |
| - Permissions | JSON outlining the needed permissions to manage the DNS records on a sub domain of your global DNS entry. Use Wayfinder's terraform module to assign permissions or create it manually. |
| - Validate (button) | Verification that the needed permissions were assigned correctly. |
| Network management | Permissions that create and manage AKS clusters. |
| - Permissions | JSON outlining the needed permissions. Use Wayfinder's terraform module to assign permissions or create it manually. |
| - Validate (button) | Verification that the needed permissions were assigned correctly. |
Summary Section Properties
Wayfinder provides you with a summary of the configuration details you've entered.
You will not be able to apply the configuration if any of the validations failed.
YAML Section Properties
You will be presented with the manifest (yaml) files for the configuration details you entered.
You have the option to apply the configuration immediately by clicking the Apply button, or to download the YAML so that you can apply it later using Wayfinder's CLI or your CI system.
The following YAML files are produced:
Workspace
Only shown when you create a new workspace.
apiVersion: org.appvia.io/v2beta1
kind: Workspace
metadata:
name: sand
spec:
description: sandbox
key: sand
summary: sandbox for dev
resourceNamespace: ''
Stage
Only shown when you create a new stage.
apiVersion: org.appvia.io/v2beta1
kind: Stage
metadata:
name: nonprod
spec:
displayName: nonprod
description: non production stage for dev
Cloud Access Configuration
The type of manifest depends on the Access Type you've selected.
- Provisioning
- DNS Zone Management
- Network Peering
- Cost Estimates
apiVersion: cloudaccess.appvia.io/v2beta2
kind: CloudAccessConfig
metadata:
name: azure-dev2
spec:
cloudIdentityRef:
cloud: aws <-- Cloud Wayfinder is connecting from
name: wf-aws-irsa <-- Identity Wayfinder is connecting with
azure:
subscription: 12345678-abcd-458d-aa01-0123abcd1234 <-- The Azure Subscription ID that you're connecting to
tenantID: 87654321-abcd-458d-aa01-0123abcd1234 <-- The Azure Tenant ID that you're connecting to
type: Provisioning <-- Note the type
permissions:
- permission: ClusterManager
- permission: NetworkManager
- permission: DNSZoneManager
stage: nonprod
apiVersion: cloudaccess.appvia.io/v2beta2
kind: CloudAccessConfig
metadata:
name: azure-dev2
spec:
cloudIdentityRef:
cloud: aws <-- Cloud Wayfinder is connecting from
name: wf-aws-irsa <-- Identity Wayfinder is connecting with
azure:
subscription: 12345678-abcd-458d-aa01-0123abcd1234 <-- The Azure Subscription ID that you're connecting to
tenantID: 87654321-abcd-458d-aa01-0123abcd1234 <-- The Azure Tenant ID that you're connecting to
type: DNSZoneManagement <-- Note the type
permissions:
- permission: DNSZoneManager
stage: nonprod
apiVersion: cloudaccess.appvia.io/v2beta2
kind: CloudAccessConfig
metadata:
name: azure-dev2
spec:
cloudIdentityRef:
cloud: aws <-- Cloud Wayfinder is connecting from
name: wf-aws-irsa <-- Identity Wayfinder is connecting with
azure:
subscription: 12345678-abcd-458d-aa01-0123abcd1234 <-- The Azure Subscription ID that you're connecting to
tenantID: 87654321-abcd-458d-aa01-0123abcd1234 <-- The Azure Tenant ID that you're connecting to
type: NetworkPeering <-- Note the type
permissions:
- permission: NetworkManager
stage: nonprod
apiVersion: cloudaccess.appvia.io/v2beta2
kind: CloudAccessConfig
metadata:
name: azure-dev2
spec:
cloudIdentityRef:
cloud: aws <-- Cloud Wayfinder is connecting from
name: wf-aws-irsa <-- Identity Wayfinder is connecting with
azure:
subscription: 12345678-abcd-458d-aa01-0123abcd1234 <-- The Azure Subscription ID that you're connecting to
tenantID: 87654321-abcd-458d-aa01-0123abcd1234 <-- The Azure Tenant ID that you're connecting to
type: CostEstimates <-- Note the type
permissions:
- permission: CostInfo
stage: nonprod
View Cloud Access Configurations
Use the wf get cloudaccessconfig CLI command to view a list of cloud access configurations. Use the --cloud flag to limit the results to the specified cloud provider and the -w flag to specify the workspace.
wf get cloudaccessconfig --cloud azure -w dmo
NAME PROVIDER STATUS IDENTIFIER AGE
azure-dev2 azure Success Unknown 1d
azure-nonprod azure Success Unknown 19d
azure-prod azure Success Unknown 19d
wf get cloudaccessconfig azure-dev2 -o yaml
Using Wayfinder's web interface:
- Select Admin, then navigate to Cloud > Access
- Select your cloud provider, for example Microsoft Azure
- The Cloud Access lists all the Cloud Access configurations for the selected cloud provider
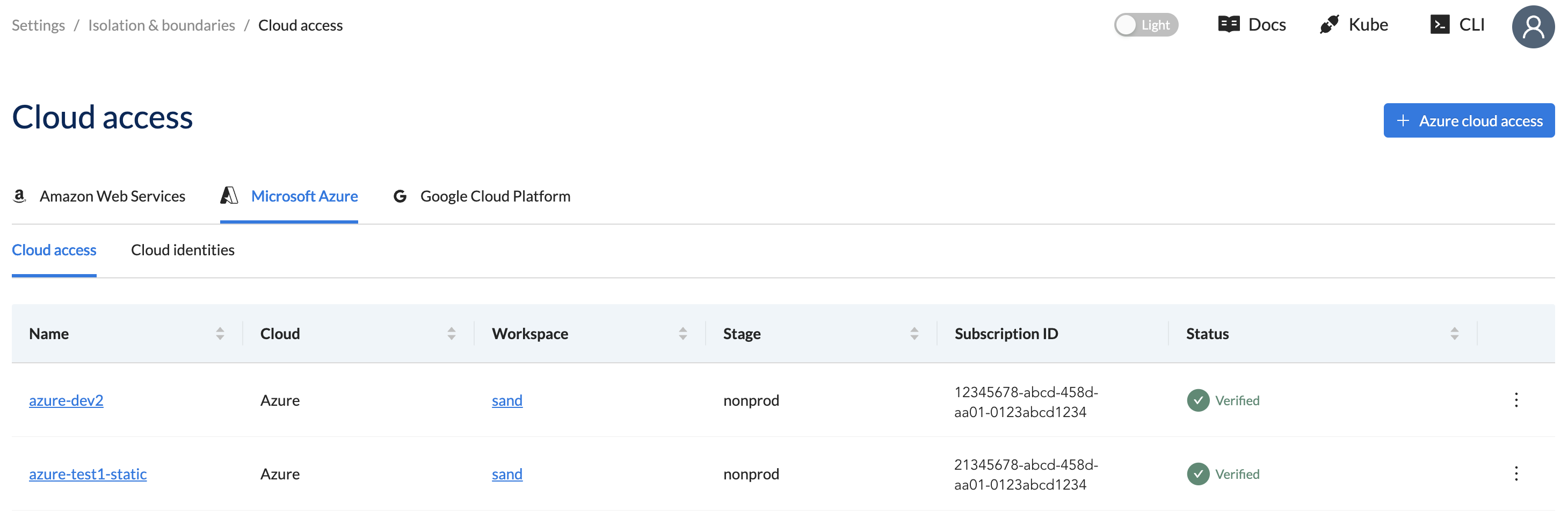
Create a Cloud Access Configuration using CLI
[ADVANCED USERS]
Use the wf create cloudaccessconfig command to create a cloud access configuration using the CLI. Follow the CLI prompts or use the --help flag for a full list of options. You need to configure the target subscription manually or use Wayfinder's terraform module.
If you need more guidance then see the quick start section.
Edit & Apply Cloud Access Configurations
Output the cloud access configuration to file using the wf get cloudaccessconfigNAME-OF-CONFIG command with the > FILENAME.yaml postfix.
wf get cloudaccessconfig azure-dev1 > ./manifests/azuredev1.yaml
Update the file as needed and use wf apply command with the -f PATH-TO-FILE.yaml flag to apply the changes.
wf apply cloudaccessconfig -f ./manifests/azuredev1.yaml
Using Wayfinder's web interface:
- Select Admin, then navigate to Cloud > Access
- Select your cloud provider, for example Microsoft Azure
- The Cloud Access lists all the Cloud Access configurations for the selected cloud provider
- Click on the name of the Cloud Access to open the form in Edit mode.
- Update as needed.
You will not be able to change the values of the fields below. If they need changing then you need to create a new cloud access configuration.
- Name
- Subscription ID
- Access Type
All validations need to pass before you can re-apply the configuration.
View Permissions
These are the permissions that Wayfinder need in the target account to create and manage cloud resources.
Use the wf get cloudpermissions CLI command to view a list of available cloud permissions.
wf get cloudpermissions
NAME WAYFINDER FUNCTIONALITY SET DESCRIPTION
ClusterManager Provisioning Used for managing cluster provisioning inside the child account
DNSZoneManager Provisioning Used for managing application DNS records on a sub domain of the Global DNS entry
NetworkManager Provisioning Used for managing network permissions inside the child account
DNSZoneManager DNSZoneManagement Used to create sub domains for workspace clusters inside of the imported top-level domain
NetworkManager NetworkPeering Accepts peering requests in an external VPC network to provide end-to-end peering automation
CloudInfo CostsEstimates Used to retrieve cost data for infrastructure cost estimation
Use the wf describe cloudpermissions CLI command to view the JSON of the specified permission.
Also see the Permisisons Section section.
wf describe cloudpermission DNSZoneManager -c azure -o json
Permission: DNSZoneManager
Description: Used for managing application DNS records on a sub domain of the Global DNS entry
Permissions:
actions:
- Microsoft.Authorization/roleAssignments/read
- Microsoft.Authorization/roleDefinitions/read
- Microsoft.Resources/subscriptions/providers/read
- Microsoft.Resources/subscriptions/resourceGroups/read
- Microsoft.Resources/subscriptions/resourceGroups/write
- Microsoft.Resources/subscriptions/resourceGroups/delete
- Microsoft.Network/dnszones/read
- Microsoft.Network/dnszones/write
- Microsoft.Network/dnszones/delete
- Microsoft.Network/dnszones/recordsets/read
- Microsoft.Network/dnszones/NS/read
- Microsoft.Network/dnszones/NS/write
- Microsoft.Network/dnszones/NS/delete
- Microsoft.Network/dnszones/TXT/read
- Microsoft.Network/dnszones/TXT/write
- Microsoft.Network/dnszones/TXT/delete
Using Wayfinder's web interface:
- Select Admin, then navigate to Cloud > Access
- Select your cloud provider, for example Microsoft Azure
- The Cloud Access lists all the Cloud Access configurations for the selected cloud provider
- Click on the name of the Cloud Access to open the form in Edit mode.
- Navigate to the Permissions section.
- Click on the Validate permissions button.
- The JSON outlining the permissions are displayed. Also see the Permisisons Section section.