Specify Additional GCP Settings
< packages | cluster plan creation workflow


Overview
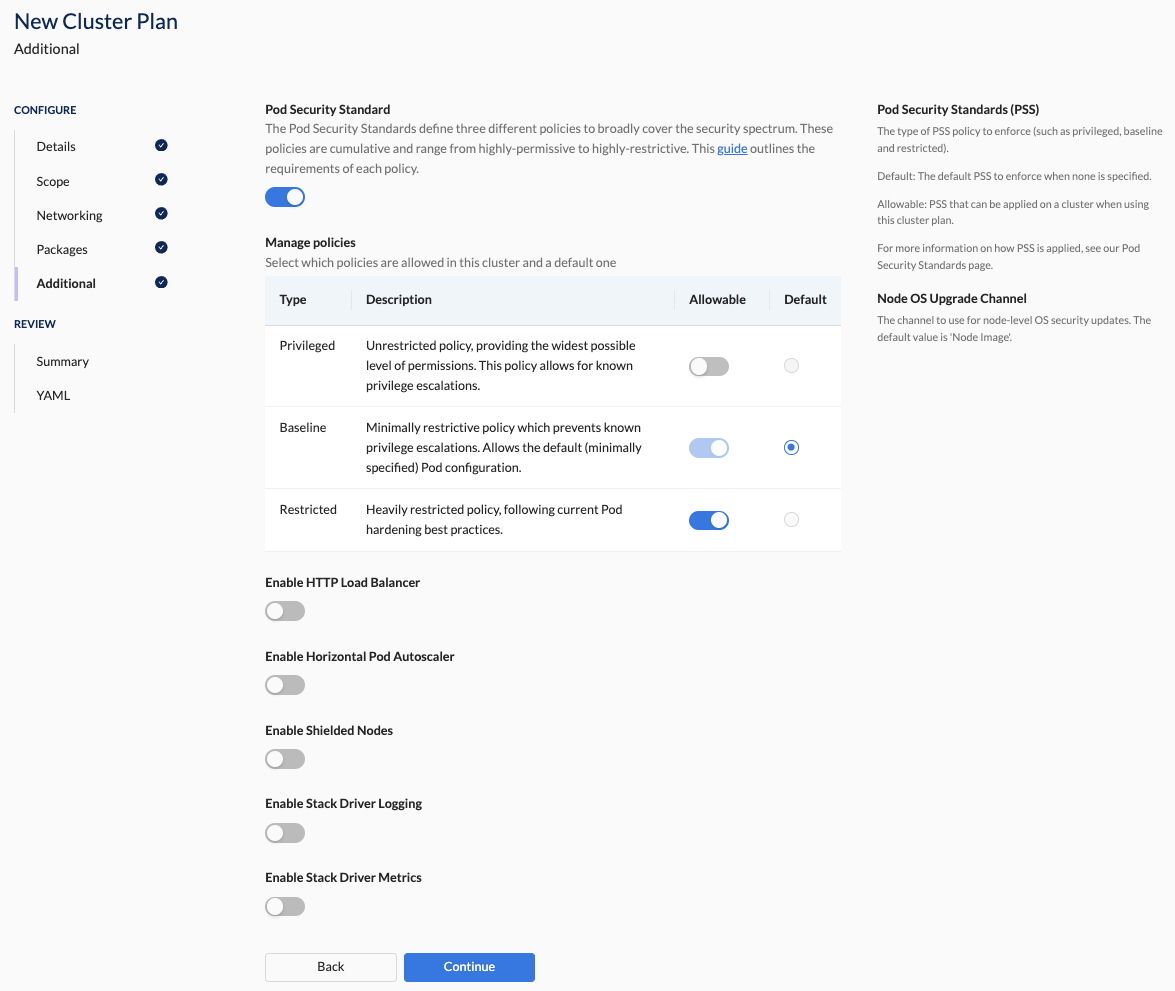
In this section, you specify the Pod Security Standards (PSS) to enforce, along with any optional GCP-specific settings.
Pod Security Standards (PSS):
This setting enforces security policies for Kubernetes clusters. You define default and allowable standards for flexibility and compliance.
GCP-specific settings:
- Enable HTTP Load Balancer: Automatically provision load balancers for ingress resources, simplifying external access management and ensuring efficient traffic distribution.
- Enable Horizontal Pod Autoscaler: Automate scaling of Kubernetes workloads based on CPU, memory consumption, or custom metrics, ensuring optimal resource utilization and responsiveness to workload changes.
- Enable Shielded Nodes: Harden GKE nodes against rootkits and bootkits by enabling Shielded Nodes, providing enhanced security and protection against various cyber threats.
- Enable Stack Driver Logging: Centralize real-time logging and monitoring across GCP services and resources, facilitating proactive troubleshooting, compliance auditing, and performance optimization.
- Enable Stack Driver Metrics: Monitor and visualize performance metrics in real-time, gaining insights into resource utilization, service health, and operational efficiency across GCP environments.
📚 For more details on key points, refer to the overview section.
📚 Explore the properties section for additional information on each UI property.
CLI Instructions
Create a new cluster plan
Follow the instructions in the details section.
Web Interface Instructions
Steps
- Fill in the scope details as outlined in the properties section.
- Click Continue to proceed
Screenshot(s)

Properties
| Field | Description |
|---|---|
| Enable Pod Security Standards | Choose if you want to allow privileged, baseline and restricted policies. You must select one of those policies to be the default. |
| Enable HTTP Load Balancer | Indicates if the cluster should be configured with the GKE ingress controller. Option(s): - Enabled: GKE will auto-discover your ingress resources and provision load balancer on your behalf. Not required if another ingress controller package is used. - Disabled: HTTP Load Balancer is disabled. |
| Enable Horizontal Pod Autoscaler | Options(s): - Enabled: Allow the number of Pods to be changed dynamically e.g. in response to the workload's CPU or memory consumption. - Disabled: Horizontal Pod Autoscaler is disabled. For more information, see GCP's documentation. |
| Enable Shielded Nodes | Option(s): - Enabled: Provides extra protection against a variety of attacks. - Disabled: Shielded Nodes are disabled. For more information, see GCP's documentation. |
| Enable Stack Driver Logging | Option(s): - Enabled: Kubernetes components logs will be sent to the GCP cloud logging solution. - Disabled: Stack Driver Logging is disabled. For more information, see GCP's documentation. |
| Enable Stack Driver Metrics | Option(s): - Enabled: Metrics data produced by the Kubernetes components are forwarded to to GCP in the Kubernetes native resource model (the default for all new clusters). - Disabled: Stack Driver Metrics are disabled. |