Create or update a cluster plan with the private link properties enabled
Overview
After configuring cloud access for Azure Private Links, your cluster plans can reference this functionality. By enabling Private Cluster and Manage private endpoint connectivity in your cluster plan, any clusters provisioned with this plan will take advantage of Azure Private Links.
You can follow the standard steps for creating a cluster plan. If you're new to this process, refer to the Create Cluster Plan section for an overview.
This section details the specific steps required to ensure that your cluster plan uses Azure Private Links.
Configuring a cluster plan to use Azure Private Links
When configuring your cluster plan to use Azure Private Links, you'll need to ensure the 'Enable private cluster' and the 'Manage private endpoint connectivity' settings are enabled in the Networking section of your plan.
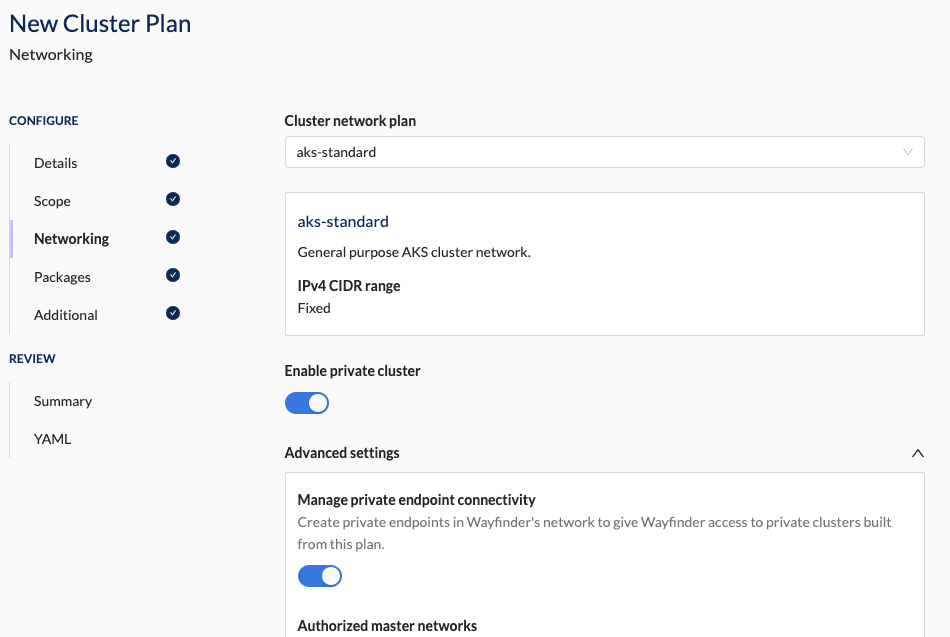
Enable Private Cluster
Enabling this option restricts access to the cluster's nodes to only be accessible from within a private network. This means that the nodes won't have public IP addresses and can only be reached through private IP addresses.
Enable Manage private endpoint connectivity
Enabling this option allows Wayfinder to automatically create and manage the necessary networking components for each AKS cluster. Specifically, Wayfinder will:
- Create Local Private Endpoints:
Wayfinder sets up private endpoints within your network that connect directly to the remote AKS Kubernetes API, ensuring secure communication between your resources and the AKS API. - Set Up Required Local DNS Zones:
Wayfinder configures local DNS zones in each region where your clusters are deployed. These zones are used for resolving the private endpoints' addresses within your network. - Configure DNS Zone Records:
Wayfinder creates DNS records that map the private endpoints to the remote AKS Kubernetes API. This ensures that all communication between your services and the AKS API remains within your private network.
YAML
These configurations will be reflected in the YAML as follows:
spec:
cluster:
enablePrivateCluster: true
providerDetails:
aks:
privateEndpointLinkManagement: true