Overview of Creating Cluster Plans
This section covers the "Create initial version" phase of the cluster plan's lifecycle.
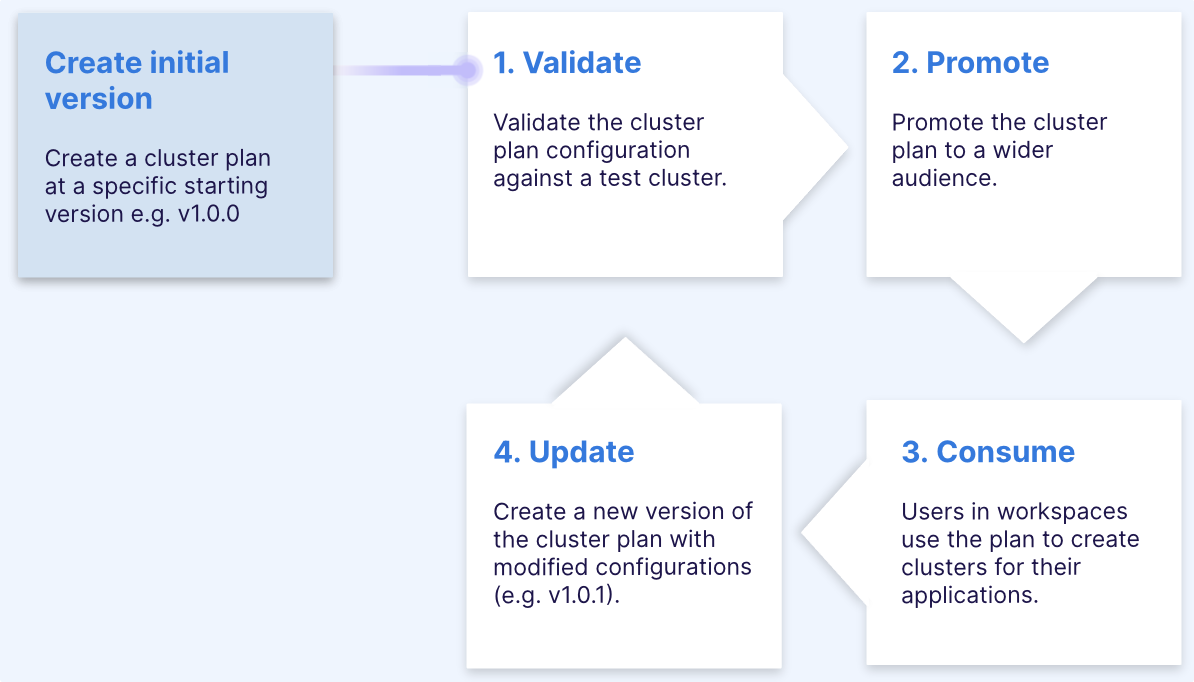
Creating a cluster plan involves several sections which you must follow in order. Key points for each section are described below:

Details
- Identification and Description: Clear and descriptive names help developers quickly identify the cluster plan's purpose and configuration details.
- Purpose and Segregation: Segregating cluster configurations based on their intended use, such as short-lived, low-budget testing clusters versus long-term, high-performance production clusters, is beneficial to developers. The Name and Description fields should document these distinctions clearly.
- Versioning: Assigning a unique semantic version to the cluster plan ensures consistency and facilitates tracking changes over time. This versioning is essential for maintaining compatibility with application environments and managing updates effectively.
- Cloud Provider Configuration: Specifying the cloud provider (e.g., AWS, Azure, GCP) and configuring the necessary settings for provisioning Kubernetes clusters ensure compatibility with the supported Kubernetes versions provided by the chosen cloud provider, avoiding compatibility issues.
- Automatic and Custom Labels: Wayfinder adds its own set of labels to clusters to identify the provider, stage, workspace and cloud region the cluster is within. These are used to target policies to a cluster. You can optionally add custom labels to allow further control over policy targeting.
Scope
Scoping cluster plans is necessary to isolate cluster configurations based on their intended use and audience within the organisation. This ensures:
- Segregation: Different types of clusters (e.g., testing vs. production) can be managed separately to meet specific operational and budgetary requirements.
- Propagation: New cluster plan versions can be tested in controlled environments before being rolled out to broader stages, ensuring stability and reliability.
- Availability: Tailored configurations can be restricted to specific workspaces, allowing teams to access resources optimised for their specific tasks, such as high-performance computing for data analytics.
Cluster Networking
A cluster network plan streamlines and automates network provisioning for clusters, ensuring consistency, efficiency, and compliance with organisational standards. This reduces errors and manual configuration efforts.
For all providers, advanced settings can be specified to enhance security, control network access, and manage APIs. These settings include specifying the IPv4 CIDR Range (Fixed/Auto-Allocated) to manage IP address flexibility, aiding in network segmentation and resource allocation efficiency. Additionally, you can configure Authorized Master Networks for direct Kubernetes API access, bypassing Wayfinder, and Authorized Networks for secure external access using Wayfinder wf access cluster and kubectl commands.
Cloud-specific settings include:
- Azure Kubernetes Service Address Range: Specify the IP range from which to assign service IPs within the cluster. Restrictions apply.
- Azure Outbound Type: Manage how outbound traffic from your Kubernetes cluster is handled. Consult Azure's egress documentation for detailed setup instructions.
- GCP Master IPv4 CIDR: Define the CIDR range reserved for Google Kubernetes Engine (GKE) control plane components to ensure secure networking and cluster management.
View configuration steps:
Packages
Including packages in cluster plans offers several benefits that enhance the functionality, consistency, and efficiency of your Kubernetes cluster provisioning:
- Consistent Bootstrapping: Adding packages to your cluster plans ensures that clusters are bootstrapped in a consistent and repeatable way. This consistency is important for maintaining reliability and predictability across environments.
- Cross-Cloud Compatibility: Wayfinder's logic can be incorporated directly into Helm configurations, enabling the use of a single Helm chart across multiple cloud providers. This ensures uniform deployment practices regardless of the cloud environment.
- Cloud-Specific Integration: Packages allow the integration of cloud-specific logic directly into the cluster plan, making it easier to tailor configurations to the unique requirements of each cloud provider.
- Standardisation: Using packages helps establish common patterns, such as applying service annotations for workload identities, which standardises configurations across different environments and teams.
Additional Configuration
Configure additional security and leverage essential cloud provider functionalities to meet organisational security standards, optimise cluster management, and ensure the protection of sensitive data and resources.
- Pod Security Standards (PSS): Enforces security policies for Kubernetes clusters, defining default and allowable standards for flexibility and compliance.
- AWS Specific Settings: Secure cluster management through Admin ARNs, enable CloudWatch logging, enforce AWS KMS secrets encryption, and manage network security with Security Group IDs.
- Azure Specific Settings: Enhance security with Node OS Upgrade Channel, automate resource authentication with User Assigned Identity, manage infrastructure in custom resource groups, and connect securely using Private Link DNS Zone VNet Links.
- GCP Specific Settings: Improve functionality with automated HTTP Load Balancer, dynamic Pod scaling via Horizontal Pod Autoscaler, enhance security with Shielded Nodes, and enable real-time monitoring and metrics visualisation with Stack Driver Logging and Metrics.
View configuration steps:
Review Configuration Summary
Review a summary of the configuration you've specified and make any amendments as needed.
Apply the YAML
View and download the YAML and then apply it using Wayfinder's CLI or via your CI system. Alternatively, you can instruct Wayfinder to apply the YAML immediately.