Access to Wayfinder itself
There are two concepts of roles within Wayfinder, those which permit access to Wayfinder itself (Wayfinder roles and Wayfinder role bindings) and those which permit access to clusters managed by Wayfinder (cluster roles, cluster role bindings, and cluster access policies). These both use a common set of workspace groups in Wayfinder. This topic outlines access to Wayfinder itself.
Also see the following related information:
- Wayfinder's RBAC implementation is used in Wayfinder's workspaces to control access to Kubernetes clusters managed by Wayfinder.
- Access Tokens provide access for your CI/CD pipelines.
Overview
User access to Wayfinder itself can operate at two levels: platform-wide access which provides access to the management of the configuration that operates outside of any workspace (i.e. Network Plans, Cloud Access Configurations, Cluster Plans, etc.) and workspace-level access which provides access to the management of resources within a specific workspace (i.e. assigning users to a workspace and giving them the privileges to deploy their applications).
The diagram below illustrates access to Wayfinder itself (left hand side of the diagram) and access to the clusters that Wayfinder manages (RBAC) (right hand side of the diagram).
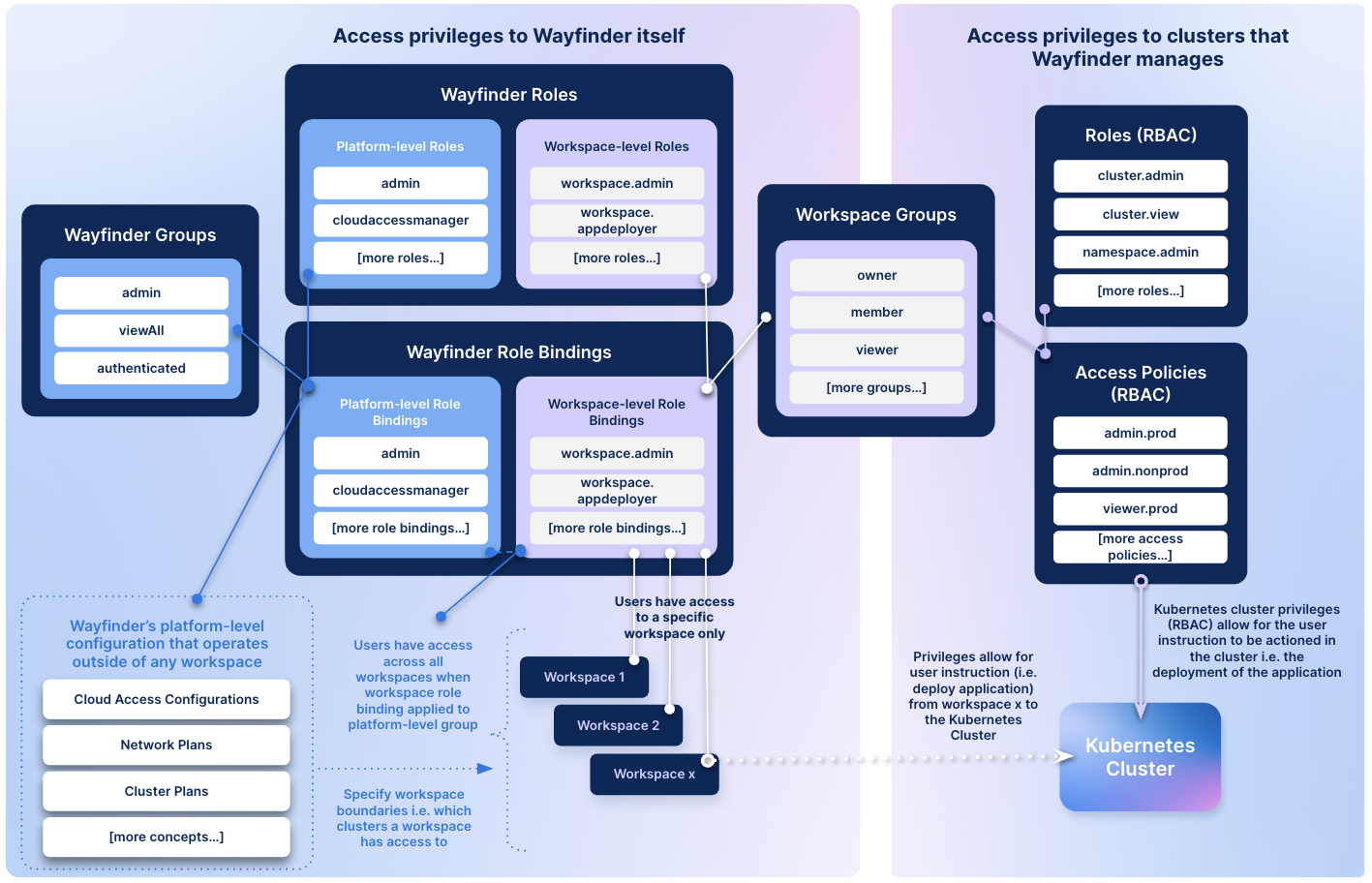
Left hand side of the diagram:
-
Wayfinder manages Wayfinder Roles and Wayfinder Role Bindings internally, therefore, as a Wayfinder administrator you only have to add users to the respective Wayfinder Groups and Workspace Groups.
-
Wayfinder Roles are divided into roles that permit platform-wide access and those that permit access to a specific workspace. Both use the
wf get wayfinderrolesCLI command. The workspace-level roles start withworkspace. -
Wayfinder Role Bindings are divided into role bindings that:
- Bind Wayfinder Roles (platform-level) to Wayfinder Groups (platform-level). Users in Wayfinder Groups that have workspace roles assigned to them, will have access across all workspaces and will be able to perform actions in each workspace that the role permits.
- Bind Wayfinder Roles (workspace-level) to Workspace groups. Users in workspace-level groups will only have access to the workspaces that they are added to. Also see the FAQ section on what happens when users belong to multiple workspaces.
Right hand side of the diagram:
- The same set of workspace groups that grant access to Wayfinder itself is also used in Wayfinder's RBAC implementation.
- Wayfinder's RBAC implementation is used in Wayfinder's workspaces to control access to Kubernetes clusters managed by Wayfinder.
Wayfinder groups
Use wf get wayfindergroups to view the groups that operate at the platform-level.
| Name | Description |
|---|---|
| admin | Administrators |
| viewall | Read-only viewer of all workspaces |
| authenticated | All authenticated users (implicit - all logged-in users are automatically in this group) |
Wayfinder groups are referenced in Wayfinder's web interface as having a Platform scope.
To view Platform scoped groups in Wayfinder's web interface:
- Click on Admin, and then navigate to Access Groups
- Platform scoped groups have a value of Platform in the Scope column
- Expand the accordion to view the users in each group.
- Use the Actions tab to view applicable actions such as editing members, useful CLI commands and manifest files.
Workspace groups
There is only one set of workspace groups and they are used to give user access to Wayfinder itself as well as give user access to clusters that Wayfinder manages (RBAC).
Use wf get workspacegroups to view the workspace groups that operate at the workspace-level.
Use wf get wayfindergroups -w WORKSPACE-NAME to view the workspace groups that exist within a particular workspace. Each workspace will inherit Wayfinder's default workspace
groups and Workspace owners can optionally create additional workspace groups. As a result, each workspace can have a different set of workspace groups.
To view Workspace scoped groups in Wayfinder's web interface as an Administrator:
- Click on Admin, and then navigate to Access > Groups
- Workspace scoped groups have a value of Workspace - [WORKSPACE-NAME] in the Scope column
To view Workspace scoped groups in Wayfinder's web interface as a workspace owner:
- Click on Workspaces > Your-Workspace-Name, and then navigate to Settings > Groups.
Wayfinder's default workspace groups are outlined in the table below.
| Name | Description | Scope |
|---|---|---|
| owner | Manages users, groups, access policies and roles within the workspace | Access to Wayfinder itself & access to the clusters that Wayfinder manages (RBAC) |
| member | Member of the workspace. No workspace management permissions | Access to Wayfinder itself & access to the clusters that Wayfinder manages (RBAC) |
| viewer | View only access to all clusters in workspace | Access to Wayfinder itself & access to the clusters that Wayfinder manages (RBAC) |
| editor | Super-user access to namespaces in Non-Production. View only access in Production | Access to the clusters that Wayfinder manages (RBAC) |
| secretsviewer-nonprod | Access to secrets in Non-Production, and other sensitive K8s configs | Access to the clusters that Wayfinder manages (RBAC) |
| secretsviewer-prod | Access to secrets, and other sensitive K8s configs | Access to the clusters that Wayfinder manages (RBAC) |
| troubleshooting | Access to logs and exec into running containers | Access to the clusters that Wayfinder manages (RBAC) |
You can learn how to add existing users to a Workspace Group by visiting the Adding Users topic.
Wayfinder roles
Wayfinder roles permit access to Wayfinder itself. They are either applicable at the platform-level or the workspace-level.
Use wf get wayfinderroles to view all the Wayfinder roles that are available at the platform-level as well as the workspace-level.
The roles below provide access to Wayfinder's platform-level configuration:
| Name | Description |
|---|---|
| admin | Full access to all platform-wide objects |
| cloudaccessmanager | Manage cloud access configuration and cloud organisations platform-wide |
| cloudresourcemanager | Manage cloud resource plans |
| clusterconfigmanager | Manage cluster configuration, plans and packages |
| dnsmanager | Manage global DNS zones |
| networkconfigmanager | Manage platform network configuration and network plans |
| useraccessmanager | Manage user access to Wayfinder itself |
| workspacecreator | Allows creation of workspaces |
Roles prefixed with 'workspace.' provide access to workspace-level resources. These are specific to a particular workspace.
| Name | Description |
|---|---|
| workspace.accessmanager | Allows management of access to a workspace and its clusters |
| workspace.accesstokenmanager | Create, update and delete workspace access tokens |
| workspace.admin | Basic access for workspace administrators to a workspace |
| workspace.appdeployer | Deploy applications via Wayfinder |
| workspace.appmanager | Create, update and delete applications and their environments |
| workspace.cloudaccessmanager | Manage cloud access configuration in a workspace |
| workspace.clusteraccess | Minimal role for all users who need access to any clusters in the workspace |
| workspace.clusterdeleter | Delete clusters and related infrastructure |
| workspace.clustermanager | Create and update (but not delete) clusters and manage namespaces |
| workspace.dnsdeleter | Delete workspace DNS zones |
| workspace.dnsmanager | Create and update (but not delete) workspace DNS zones |
| workspace.member | Basic access for all members of a workspace |
| workspace.namespacemanager | Create, update and delete namespaces in the workspace clusters |
| workspace.nonmember | Limited read-only access to a few top-level workspace resources, for non-members |
| workspace.packagemanager | Allows management of packages in a workspace |
| workspace.policymanager | Manage policy in a workspace |
| workspace.viewer | Read-only access to all objects in a workspace |
Wayfinder role bindings
The following roles are available to users in each of the groups.
- P : Privileges are at the Platform-level.
- A : Privileges apply across All workspaces.
- W : Privileges are Workspace-specific.
- Empty Cell: No privileges
| Role | Wayfinder Admin Group | Wayfinder Viewall Group | Wayfinder Authenticated Group | Workspace Owner Group | Workspace Member Group | Workspace Viewer Group |
|---|---|---|---|---|---|---|
| admin | P | |||||
| cloudaccessmanager | P | |||||
| cloudresourcemanager | P | |||||
| clusterconfigmanager | P | |||||
| dnsmanager | P | |||||
| networkconfigmanager | P | |||||
| useraccessmanager | P | |||||
| workspacecreator | A | |||||
| workspace. accessmanager | A | W | ||||
| workspace. accesstokenmanager | A | W | W | |||
| workspace.admin | A | W | ||||
| workspace. appdeployer | A | W | W | |||
| workspace. appmanager | A | W | W | |||
| workspace. cloudaccessmanager | A | W | ||||
| workspace. clusteraccess | A | W | W | |||
| workspace. clusterdeleter | A | W | ||||
| workspace. clustermanager | A | W | W | |||
| workspace.dnsdeleter | A | W | ||||
| workspace. dnsmanager | A | W | W | |||
| workspace.member | A | W | W | |||
| workspace. namespacemanager | A | W | W | |||
| workspace. nonmember | A | |||||
| workspace. packagemanager | A | W | ||||
| workspace. policymanager | A | W | ||||
| workspace.viewer | A | A | W | W | W |
FAQs
💬 What is the difference between the workspace.viewer role for a user in the Admin Group vs Workspace Owner Group?
- The workspace.viewer role for the Wayfinder Admin and the Wayfinder Viewall groups allow view access across all workspaces. In the table above, this type of access is indicated with an 'A'.
- The same workspace.viewer role for the Workspace Owner, Workspace Member and Workspace Viewer groups allow view access to a specific workspace. In the table above, this type of access is indicated with an 'W'.
This is also true for other roles in the table above where A and W are listed against the same role i.e. workspace.appdeployer.
💬 What happens when a user belongs to mutliple workspaces?
If a user belongs to more than one workspace, then that user is limited to the access that each of the groups provide, for each group that the user is a member of, and to the workspace that the group falls within. Therefore, access for that user may be same or different across workspaces.
For example:
- User1 is assigned to the
workspace member groupin workspaceCoolApps, so user1 enjoys all the privileges that has been assigned to him and which allows him to deploy applications (i.e. workspace.viewer, workspace.appdeployer, workspace.clusteraccess, workspace.member, etc.). - User1 is also assigned to the
workspace viewer groupin workspaceBizApps, so only hasworkspace.viewprivileges and will therefore not be able to deploy any applications within BizApps.
💬 What is the difference between workspace groups and Wayfinder groups?
Wayfinder's workspace groups operate at the workspace-level and could:
- Only grant access to Wayfinder's workspaces itself (via Wayfinder roles and Wayfinder rolebindings), OR
- Grant access to Wayfinder's workspaces and grant access to the Kubernetes clusters that Wayfinder manages for that workspace (via workspace roles and workspace access policies).
Wayfinder groups grant access to Wayfinder itself and could (via Wayfinder roles and Wayfinder rolebindings):
- Grant access at the platform-level to administer configurations outside of any workspace i.e. network plans, cloud access configurations, etc.
- Grant access to Wayfinders workspaces itself without any cluster access permissions. This access is managed internally by Wayfinder and is not visible within Wayfinder's web interface.