Troubleshooting
Wayfinder's web interface offers easy access to logs, enabling you to troubleshoot both Wayfinder and the pods/containers within the Kubernetes clusters that Wayfinder manages.
Troubleshooting tools
You have access to three types of troubleshooting tools in Wayfinder:
- Logs: View the log files for the containers within a specific pod
- Shell: Get inside a running container by accessing its shell
- YAML: View the specified pod's manifest (YAML)
Logs
Log properties
The properties below are available to you when you're in the Logs view.
| Field | Description |
|---|---|
| Component | The component which is producing the logs. Available to administrators when viewing logs of Wayfinder's instance Option(s): - Controllers: Wayfinder's control plane which interacts with your cloud infrastructure - API: Wayfinder's API which the CLI and web interface interact with - Webhooks: Wayfinder's validation and mutation handlers which check if new and updated resources are valid - Portal: Events from Wayfinder's web interface - KubeProxy: Wayfinder's proxy for user access to managed Kubernetes clusters - All: View all logs |
| Container | The container you wish to view the logs of. Available when viewing logs at the cluster level Option(s): - [Various]: All the containers specified in the pod specification will be available to choose from, so the values will depend on what you are running. |
| Follow | When checked, you will see real-time updates to the log you're viewing. Uncheck to pause updates. |
| Tail | Number of lines to show from tail end of log |
| Filter | Text to filter on e.g, 'error' will show all lines in the log containing the word 'error' |
| Refresh | Get the latest set of logs |
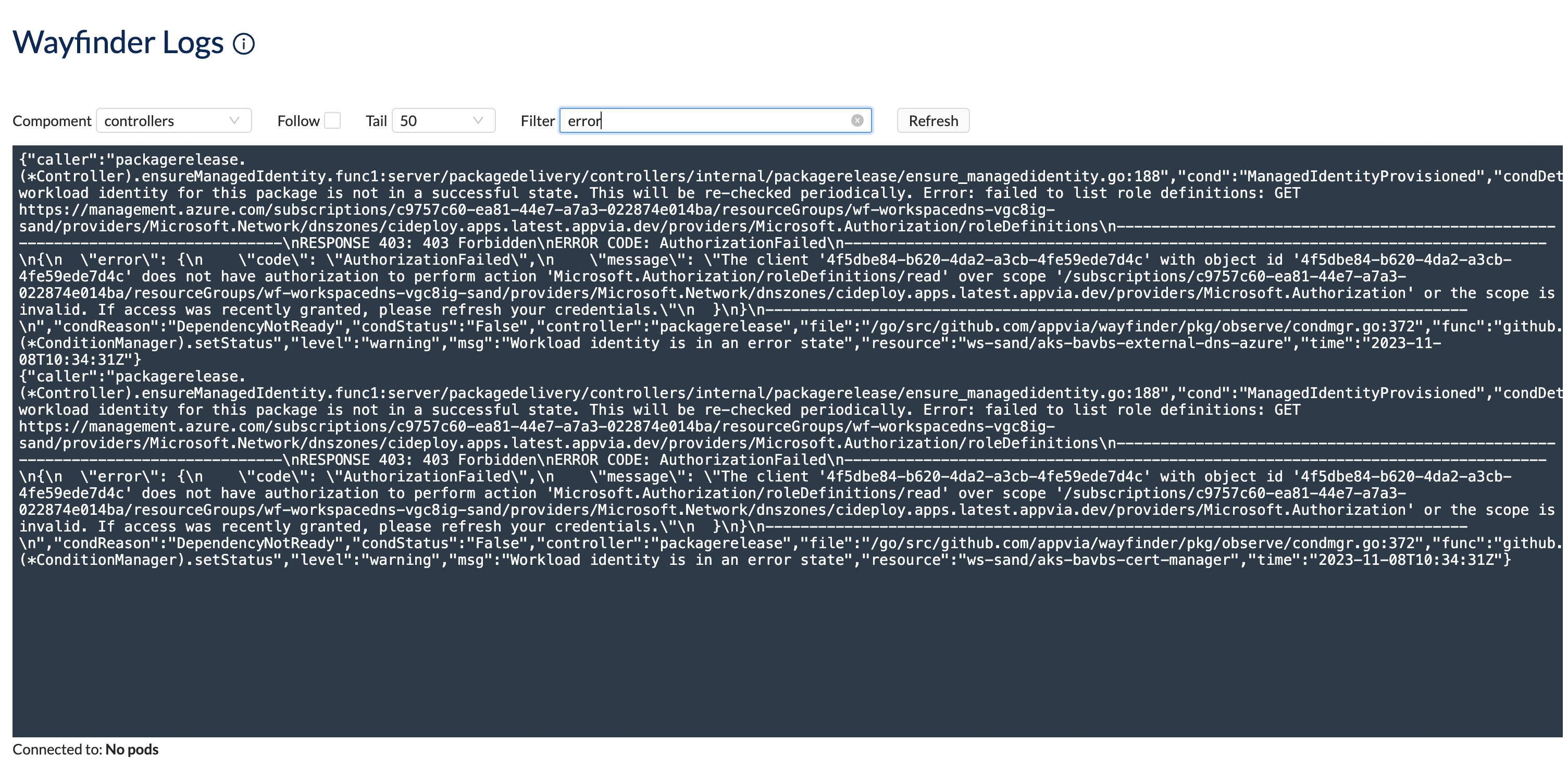
Logs to troubleshoot Wayfinder's instance
Wayfinder's administrators can perform these steps.
Use these logs when troubleshooting Wayfinder's instance.
Within Wayfinder's web interface:
- Navigate to Admin and then select Troubleshooting
- You are presented with Wayfinder's logs
- Update the properties to view and manipulate the log's contents
Logs

Logs with filter
Logs to troubleshoot Pods/Containers
Any user who has an access policy permitting the use of a role which gives them access to the pod (such as 'namespace.view' or 'namespace.troubleshooting') can perform these steps.
Use these logs when troubleshooting pods/containers within a cluster that Wayfinder manages.
You can get to these logs in Wayfinder's web interface from:
- Admin > Kubernetes > Clusters > Namespace > Pods
View all steps
Within Wayfinder's web interface:
- Navigate to Admin and then select Kubernetes > Clusters
- Select a Namespace and then select the Pods tab
- If needed, click on the Get Access button
- Select an appropriate Role for the access you need (e.g., cluster.admin)
- Specify the Duration of how long you need access using that role
- Click the Request Access button
- You are presented with the logs for the type of container within the specified pod
- Update the properties to view and manipulate the log's contents
- Workspaces > Applications > Environment > Component > Pods
View all steps
Within Wayfinder's web interface:
- Navigate to Workspaces and then select the name of your workspace
- Select Applications and then select the name of your application
- Select the name of your Environment
- Select your component's name on the Components tab
- Select the relevant pod name on the Pods tab
- If needed, click on the Get Access button
- Select an appropriate Role for the access you need (e.g., cluster.admin)
- Specify the Duration of how long you need access using that role
- Click the Request Access button
- You are presented with the logs for the type of container within the specified pod
- Update the properties to view and manipulate the log's contents
- Workspaces > Clusters > Cluster > Namespace > Pods
View all steps
Within Wayfinder's web interface:
- Navigate to Workspaces and then select the name of your workspace
- Select Clusters and then select the name of your cluster
- Select the name of your Namespace
- Select the relevant pod name on the Pods tab
- If needed, click on the Get Access button
- Select an appropriate Role for the access you need (e.g., cluster.admin)
- Specify the Duration of how long you need access using that role
- Click the Request Access button
- You are presented with the logs for the type of container within the specified pod
- Update the properties to view and manipulate the log's contents
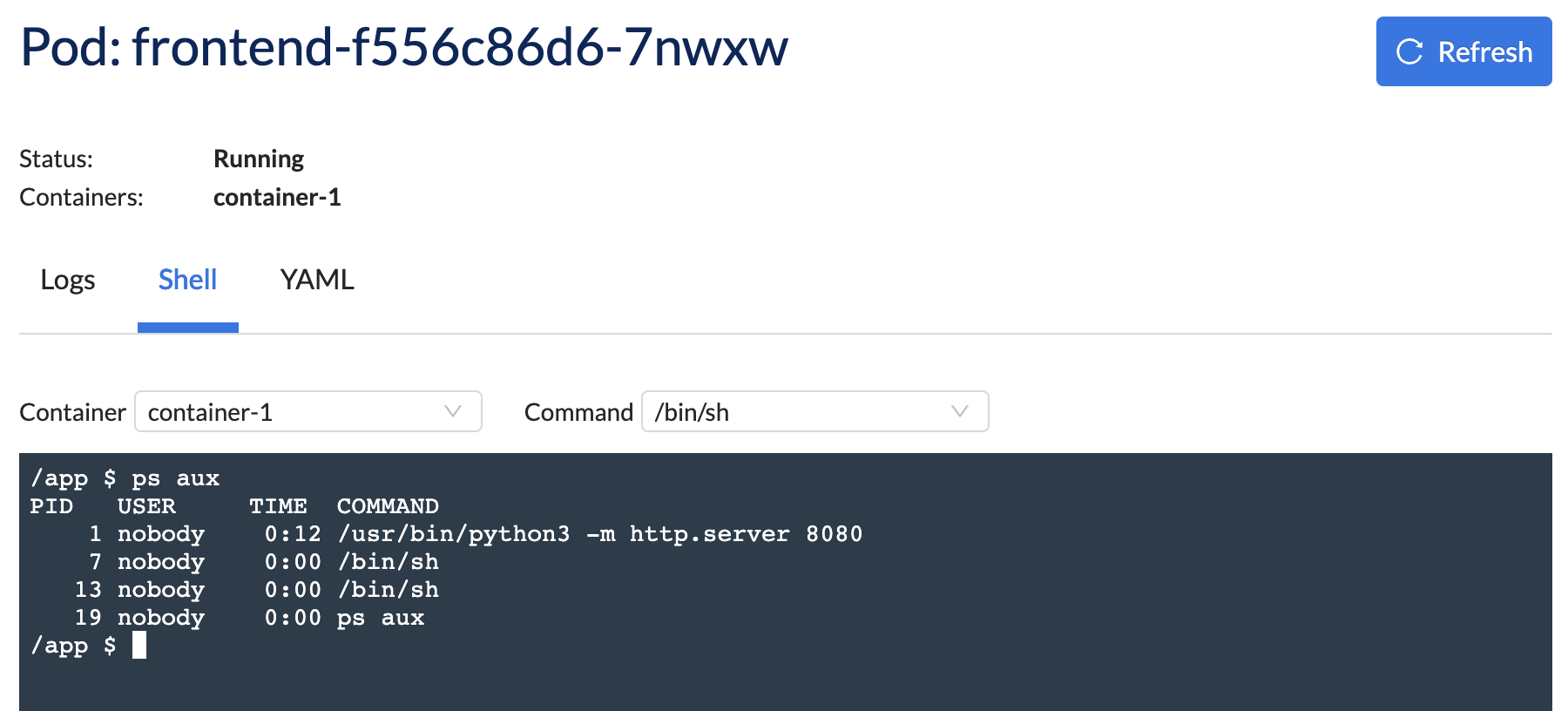
Shell
Any user who has an access policy permitting the use of a role which gives them access to pod exec (such as 'namespace.troubleshooting') can perform these steps.
The shell is accessible in the same location as the respective log files. Simply click on the Shell tab.
YAML
Any user who has an access policy permitting the use of a role which gives them read access to the pod (such as 'namespace.view' or 'namespace.troubleshooting') can perform these steps.
The YAML is accessible in the same location as the respective log files. Simply click on the YAML tab.

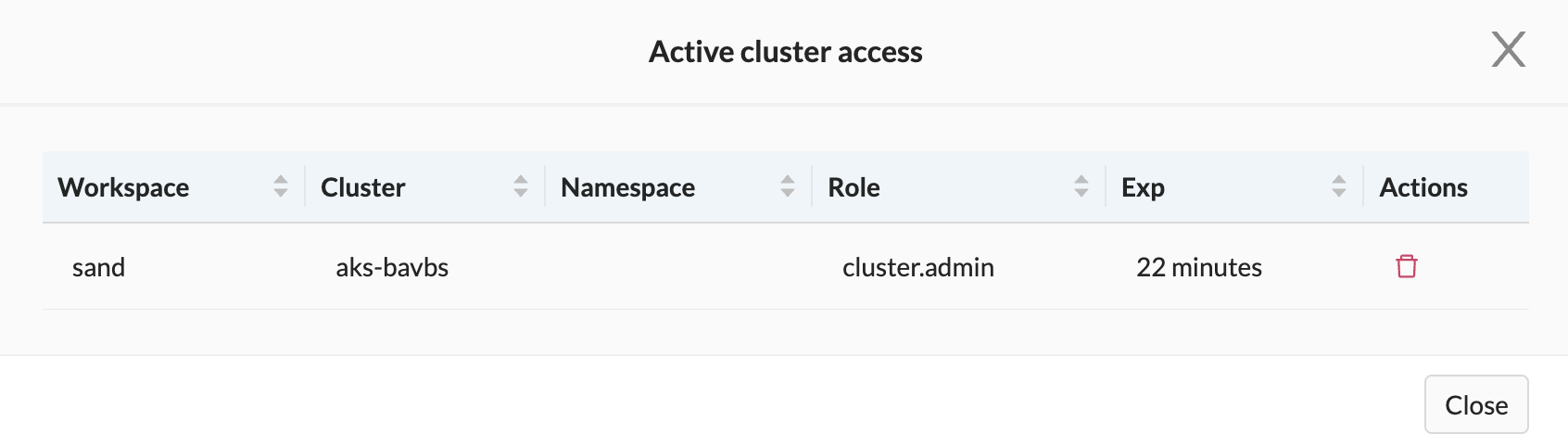
Sessions
You can manage sessions by clicking on the Kube icon in the top right-hand of the screen and remove sessions as needed.
Troubleshooting Scenarios
The following sections describe various troubleshooting steps. Unless otherwise noted, any user can perform these steps.
Your access to Wayfinder's troubleshooting tools is determined by both your user type and the assigned access policy.
- Wayfinder's instance logs: Administrators only
- Pod / container logs: Any user who has an access policy permitting the use of a role which gives them access to the pod (such as 'namespace.view' or 'namespace.troubleshooting')
- Pod / container shell: Any user who has an access policy permitting the use of a role which gives them access to pod exec (such as 'namespace.troubleshooting')
- Pod / container yaml: Any user who has an access policy permitting the use of a role which gives them read access to the pod (such as 'namespace.troubleshooting')
Installing Wayfinder
[Wayfinder administrator]
Google Cloud authentication error
If you encounter the following during an installation on GCP:
◉ Verifying you have correct permissions to Google Cloud
✔ Successfully verified permissions to Google Cloud API
Error: unable to create cluster provider - Get "https://cloudresourcemanager.googleapis.com/v1/projects?alt=json&prettyPrint=false": oauth2: cannot fetch token: 400 Bad Request
Response: {
"error": "invalid_grant",
"error_description": "Bad Request"
}
Ensure you have logged in using $ gcloud auth application-default login. This ensures the credentials created via the web flow are stored in
Application Default Credentials (ADC) and facilitates using the CLI to use the SDK with those stored
credentials.
Certificates and cert-manager
If you are not using the installation options --api-tls-private-key-pem and --ui-tls-private-key-pem, Wayfinder installs and uses cert-manager to provision certificates. Occasionally, cert-manager can fail while requesting a certificate from LetsEncrypt and falls into an exponential backoff:
◉ Waiting for Cert Manager to successfully retrieve a certificate for API
Error: operation has been cancelled
OR
◉ Waiting for Cert Manager to successfully retrieve a certificate for UI
Error: operation has been cancelled
If you encounter this issue:
-
Check the status of the
certificateresource in thewayfindernamespace:kubectl -n wayfinder get certificate -
Try deleting the certificate request, and then re-run the non-interactive install:
kubectl -n wayfinder delete certificate NAMEwf install --non-interactive
You can access the management cluster to perform the above via:
# Google Cloud
# Name: is the name of the management cluster we gave in the install
# Region: is the region we created the management cluster in
$ gcloud container clusters get-credentials NAME --zone REGION
# Amazon AWS
# Name: is the name of the management cluster we gave in the install
$ aws eks update-kubeconfig --name NAME
# Azure
# Name: is the name of the management cluster we gave in the install
# Region: is the location we placed the management cluster. The resource group created following the format wf-NAME-REGION
$ az aks get-credentials --admin --name NAME --resource-group wf-NAME-REGION
Creating or accessing a cluster
No available account when creating a cluster
[Wayfinder administrator]
To see an available account when creating a cluster, check that the following are true:
- There is at least one cloud access created in Wayfinder for this cloud provider.
Access forbidden
If you see this message in the UI or CLI while accessing a cluster, any of the following may be the cause:
-
If this is a multi-tenant cluster where you are a tenant, you can administer your namespace, but you will not be able to access cluster resources.
-
Make sure you have run the command
wf accesscluster to establish an assumed role as a user on this cluster. You only have to run this once. -
Check that a live session has been successfully established for your user ID:
wf sessions
Cluster is in an error state
Check the health of your cluster by examining the detailed status of the resource:
wf get cluster –w WORKSPACE-NAME CLUSTER-NAME -o yaml
App deployment
Where do I find deployment details for my Kubernetes manifest?
See the application deployment and log file sections.
Access Tokens
Can't assign an Access Token to a namespace
Wayfinder only has visibility into the infrastructure it manages. Your namespace may exist in Kubernetes but not in Wayfinder.
If that's the case, manually create the namespace in Wayfinder to associate it with the cluster. This does not affect the existing namespace, but makes it visible to Wayfinder.
Costs
Don't see estimated cost
[Wayfinder administrator]
Estimated costs: To see estimated costs when creating clusters or cluster plans, this must be true:
- There is at least one account with Estimated costs enabled for this cloud vendor.
See cloud access.