Release Notes
Supported versions
This page provides release notes for supported versions of Wayfinder.
For information on Wayfinder release cadence and support lifecycle, see:
Install Wayfinder
You can install Wayfinder via the provided Terraform Modules.
Wayfinder is free to use for 30 days (you will only incur cloud provider hosting costs). After this period, the trial licence will expire and your testing period ends. Please get in touch at hello@appvia.io to request a trial extension or commercial licence.
Release v2.10.1
Wayfinder 2.10 introduces improvements to the management of EKS node pools, allowing a wider diversity of image types to be used as supported by AWS.
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.10.1/wayfinder.sha256sums
Improvements:
- [WFP-4992, WFP-4928] ✨ Support AWS launch templates (for IMDSv2 required and instance tagging)
- [WFP-5069, WFP-5103, WFP-5118, WFP-4993] ✨ Allow EKS nodepool updates and update EKS AMI image types. Also view nodepool links
- [WFP-5020] ✨ Filter images based on EC2 instance type
- [WFP-4994] ✨ Allow default security group on AWS to be disabled
- [WFP-4993] ✨ AWS SSM permissions granted for nodes so that remote SSM management works
- [WFP-5065] ✨ Add AWS fields to peering rules form
- [WFP-5157] ✨ Update default clusterplans to use launch templates
- [WFP-5231] ✨ Set IMDS hop limit to 2 in our default EKS plans to allow AWS load balancer controller to work
- [WFP-5209] ✨ Make spot pricing information work on AWS
- [WFP-5531] ✨ Deny privilege escalation to mysql, redis in Helm chart
- [WFP-5843] ✨ Migrate external-dns package to official Kubernetes sigs repository, remediate bitnami deprecation
- [WFP-5124] ✨ UI - Add 'Disable default security group' to AWS cluster network settings form
- [WFP-5087] ✨ UI - Add wordwrap to detail display on conditions on WFResourceStatus detail modal
- [WFP-5042] ✨ UI - Show message if no stages available on cluster form if no cloud access configured
- [WFP-5555] ✨ CLI - Ensure 'wf apply' outputs something during the pre-apply dry-run, as that can take a while
Bug Fixes
- [WFP-5838] 🐛 Handle the containing resource group or resource not being found for an Azure role definition delete
- [WFP-5406, WFP-5434] 🐛 Remove Azure role assignments when we've finished with them
- [WFP-5575] 🐛 Fix error when immediately deleting Azure cluster after creation
- [FIX] 🐛 Don't fail cluster reconciliation if no peering found
- [WFP-5374] 🐛 Fix error in GCP workload identities (and improve lookup)
- [WFP-5192] 🐛 Handle use of multiple instance types when using a launch template
- [WFP-5134] 🐛 Correct semver validation to allow pre-release to contain . and show base version in UI on versioned forms
- [WFP-4611] 🐛 Add longer configurable read timeout to kube proxy, 1hr by default
- [DEFAULTS] 🐛 Exclude helm-controller from flux policy
- [WFP-4991] 🐛 Allow packages with only manifests to reconcile correctly
- [WFP-4992] 🐛 Ensure legacy NodePoolUpdates are ignored in new update logic
- [WFP-5111] 🐛 Allow validation of tfvars template using number/bool inputs
- [WFP-5023] 🐛 Prevent tfvars template from being repopulated on empty
- [WFP-5528] 🐛 UI - Don't add the login page to the redirect path if already on login page
- [WFP-5539] 🐛 UI - Prevent admin workspace being included in all worskapces list once and for all
- [WFP-5202] 🐛 UI - use keys and values for fields on a secret
- [WFP-5186] 🐛 UI - Don't use naked tags on cluster plan version list
- [WFP-5117] 🐛 UI - Show not found message if app does not exist
- [WFP-5061] 🐛 UI - Switching from admin cloud access to provisioning should not prevent you from completing the form
- [WFP-4951] 🐛 UI - Plan version in list should not link to edit when plan is in use
- [WFP-5094] 🐛 UI - Nodepools appear to duplicate due to React duplicate keys
- [WFP-5018] 🐛 UI - Remove validation check for workspace name (spec.summary) field
- [WFP-5106/5104/5115] 🐛 UI - Number type shouldn't prevent modal from saving / default values should look like the right type
- [WFP-5063] 🐛 UI - Correct namespace count for multi-tenant clusters in workspace they are shared with
- [WFP-5098] 🐛 UI - Show correct tag on cluster plan card info depending on if user is using existing network or not
- [WFP-3245] 🐛 CLI - Fix
wf patchreporting success for invalid paths
Release v2.9.8
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.9.8/wayfinder.sha256sums
Bug Fixes
- [WFP-5183] 🐛 Fix platform secret action menu
- [WFP-5182] 🐛 Validate the name of platform secrets in the UI properly
- [WFP-5167] 🐛 Do not allow empty manifest templates in packages
- [WFP-5168] 🐛 Display cluster form errors before selecting plans or nodepools
- [WFP-5254] 🐛 Fix the panic when the AKS service IP address is NOT populated
- [WFP-5187] 🐛 Update Azure role assignments SDK to resolve Azure SDK API bug
- [WFP-5229] 🐛 UI - Fix status link on cluster node tab
Release v2.9.6
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.9.6/wayfinder.sha256sums
Improvements:
- ✨ Update default packages to use external repos and latest versions
- [WFP-5041] ✨ Surface AWS account limit errors as
ActionRequiredwarnings on cluster - ✨ Minor tweaks to cluster package condition reporting, cluster updates operator
- [WFP-5000, WFP-5001, WFP-5035] ✨ Enhance cluster deletion reporting
- [WFP-5048] ✨ Support annotating the Deployment in app container components
- [WFP-4985/4984] ✨ Support lists of strings and choices for cloud resource plans
- [WFP-4897, WFP-5012, WFP-5036] ✨ PackageReleases now managed by Cluster controller from ClusterPlan
- [WFP-5034] ✨ Reconcile clusters at v2beta2 instead of v2beta1 to avoid edge case complexity (addresses WFP-5001, WFP-5000)
- [WFP-4966] ✨ UI - Richer in progress status for cluster create, update and delete
- [WFP-4920] ✨ UI - Refresh Workspace list on going to the page
- [WFP-5037] ✨ UI - Link status tag to status tab on cluster plan version infoview
- [WFP-5011] ✨ UI - Prevent user from continuing to summary when editing a cluster that violates a provisioning policy
- [WFP-4950] ✨ UI - Add access environment button to app env page
- [WFP-4888] ✨ UI - Show total NS count for all workspaces on MT cluster in OWNING workspace
- ✨ UI - Remove ugly scrollbars in left hand navigation
- [WFP-5014] ✨ UI - Allow custom logo to be specified in Helm
- [WFP-5006] ✨ UI - Add warning when specifying an EKS network size of less than /22
- ✨ UI - Improve 'Manage' menu button display
- [WFP-4847] ✨ UI - Cluster plan + versions - UX improvements
- 📖 UI - Make cluster access policy minidoc naming in-line with the form field names
- [WFP-4976] ✨ UI - Add namespaces from packages on cluster namespaces list
- [WFP-4977] ✨ UI - Don't include resource name in modal title when delete-confirming
- [WFP-4967] ✨ CLI/UI - Filter roles in
wf access clusterand UI 'Request cluster access' to those user has access to - [WFP-5040] ✨ CLI/API - Ensure CLI version is always up to date with the major.minor of Wayfinder API
- [WFP-5021] ✨ CLI - resource going to ActionRequired status on
--wait-for-readynow stops immediately inwf apply - [WFP-4617] ✨ CLI - Improve output of
wf create cluster, showing progress and status of provisioning - ✨ CLI - Show plan versions 'most-recent-first' in
wf create cluster - [WFP-4979] ✨ CLI - Show kind when prune/delete fails in
wf apply
Bug Fixes
- [WFP-5064] 🐛 Fix issue with certain configurations of peering rule transit associations
- [WFP-5016] 🐛 Ensure publishState annotation set consistently when cluster plan published
- [WFP-4988] 🐛 Fix issues caused by orphaning TGW connections in AWS peering on premature teardown
- [WFP-4926] 🐛 Allow updates to EKS CloudWatch log settings
- [WFP-4998] 🐛 Set default API version for Cloud Resource Plan to v2beta2 to ensure prune works correctly
- [WFP-4968] 🐛 Do not create app envs on deleting clusters
- [WFP-4977] 🐛/✨ Prevent deletion of cloud resource plans when referenced
- [WFP-4972] 🐛 Fix cloud resource plan input default values at v2beta2
- [WFP-5033] 🐛 UI - DNS zone Action Required status not surfacing/linking to appropriate place
- [WFP-5052] 🐛 UI - Validate cluster plan version (if applicable) on cluster form compute step
- [WFP-5054] 🐛 UI - Cluster status - ensure optional conditions don't render anything
- [WFP-5056] 🐛 UI - Don't error if CRD not registered when viewing namespace resources (e.g. certificates on cluster without cert-manager)
- [WFP-5045] 🐛 UI - Ensure Application List calls workspaced app component endpoint (fixes issue with non-workspace-owners listing app components)
- [WFP-4999] 🐛 UI - Add Additional Instance Types field for spot EKS node pools on cluster and compute template forms
- [WFP-5010] 🐛 UI - Fix component links in Application table
- [WFP-4986] 🐛 UI - Handle cluster plan selection/cancellation correctly in cluster form
- [WFP-4948] 🐛 UI - Avoid count showing NaN for stages
- [WFP-4978] 🐛 UI - Fix duplicate outputs on cloud resource plan status
- [WFP-4578] 🐛 UI - Handle ownership of workspace CRD when setting owners
- [WFP-4970] 🐛 UI - Fix unreadable cluster status text in dark mode
- [WFP-4969] 🐛 UI - Ensure all code blocks have correct overflow applied in WFResourceStatus modal
- [WPF-5062] 🐛 CLI - Update
wf create clusterto follow correct v2beta2 Cluster conditions - [WFP-4980] 🐛 CLI - Fix
wf gettable output formatting issue - [WFP-5007] 🐛 CLI - Correct the help text for
wf validate clusterplanflags - [WFP-4932] 🐛 CLI - Fix issue causing cluster build watches to fail in certain scenarios
Release v2.9.1
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.9.1/wayfinder.sha256sums
Wayfinder 2.9 introduces four major new features - templated Cloud Resource Plans, 'Follow-Published' Cluster Plan version management, UI Policy management, and Azure AKS Private Endpoint connectivity - along with our usual selection of enhancements, fixes and improvements.
Templated & versioned Cloud Resource Plans
With our new generation of Cloud Resource Plans, you can now use our standard templating to configure the tfvars used to apply your Terraform and choose your own inputs for app teams to provide on consumption.
This gives you full control over the configuration applied to the module, and allows you to choose simple inputs that app teams provide on consumption and flexibly map those through to whatever complex configuration the Terraform module needs.
This makes it possible to support a much wider range of existing modules and gives far more flexibility in how you choose to configure them.
Our new Cloud Resource Plan management form interactively pulls the details of your selected Terraform module, producing an example tfvars template and showing you the module's readme and outputs, making configuring new Terraform modules significantly simpler.
Cloud Resource Plans are also now versioned, allowing you to produce and test new versions of the plan without affecting existing deployed resources.
- [WFP-4657] ✨ Backend - Add v2beta2 CloudResourcePlan CRD supporting tfvars template
- Add SecretRef to CloudResourcePlan v2beta2
- [WFP-4663] ✨ Backend - Support versioned cloud resource plans with templates in app component manifest rendering
- [WFP-4660 / WFP-4802] ✨ Add CloudResourcePlan resource TF vars template validation
- [WFP-4884] ✨ Dummy-render the TFVars template on a CloudResourcePlan before HCL validation to allow validation of the templated variables
- [WFP-4662] ✨ Add API to get Terraform module versions and provide module metadata + skeleton tfVars
- [WFP-4662] ✨ Improvements to Terraform repo API
- [WFP-4878] 🚮 Remove legacy Terranetes API component to determine Terraform module metadata - replaced by the above
- [WFP-4865] ✨ Update Terranetes to v0.7.20 in our default plans, with support for tfVars
- [WFP-4665] ✨ UI - New cloud resource plan form + table list + infoview
- [WFP-4858] ✨ UI - Update cloud resource links
- [WFP-4873] ✨ UI - Support v2beta2 Cloud Resource Plans in app Cloud Resource Component form
- [WFP-4878] ✨ CLI - Add
--wait-for-removetowf deploy - [WFP-4922] ✨ Support all terraform outputs when constructing cloud resource components
- [WFP-4658] ✨ Add default tags to Cloud Resource app component templating context
'Follow Published' Cluster Plan version management for clusters
This enhancement to Cluster Plan versioning (introduced in 2.8) simplifies the rollout of new plan versions by allowing clusters to be specified as simply 'Follow Published', rather than choosing a specific plan version.
From the platform side, plan versions now have a simple 'Draft-Published-Deprecated' life cycle, and only versions in 'Published' state will be offered to app teams when building clusters.
When a cluster is built with 'Follow Published', Wayfinder will automatically select the latest published version of the plan as the initial version.
Upgrades are also simplified - when you are happy with a new version of your plan, moving it from 'Draft' to 'Published' makes the update available to all 'Follow Published' clusters using that plan.
Your app teams then just make a single click, CLI command (wf update cluster) or API call to accept the
upgrade at a time of their choosing. They can preview the upgrade with an easy-to-understand diff from
the current version, allowing them to understand exactly what is being changed on their cluster.
A future release will allow updates to be automatically applied to 'Follow Published' clusters, according to your own rollout strategy.
- [WFP-4777] ✨ Update Cluster v2beta2 CRD to have followPublished and related statuses
- [WFP-4745] ✨ Introduce published/unpublished annotation to cluster plan versions
- [WFP-4778] ✨ Add followPublished logic to
Clustermutation and validation webhooks - [WFP-4764] ✨ Add operator to annotate followPublished clusters when new plan version available
- [WFP-4763] ✨ Support plan version from annotation when following published
- [WFP-4952] ✨ Watch for annotation changes on clusters so we reconcile on update of plan version annotation
- [WFP-4768] ✨ Add followPublished logic to UpdateCluster API and CLI
- [WFP-4933] ✨ Refactor get next/latest published
ClusterPlanversion
- [WFP-4933] ✨ Refactor get next/latest published
- [WFP-4779] ✨ Use 'Creating' and 'Updating' statuses on Cluster when cluster is being created or its plan version is being updated
- [WFP-4762] ✨ UI - Show diff between cluster plan versions on upgrade
- [WFP-4876] ✨ UI - Amend cluster build form to use 'followPublished' by default
- [WFP-4766] ✨ UI - Support 'Update cluster' action
UI - Policy functionality
You can now view and manage all of your provisioning policies, cluster policies and cluster access policies through the UI.
- [WFP-4499] ✨ UI - Provisioning Policy table and InfoView
- [WFP-4498] ✨ UI - Provisioning Policy form
- [WFP-4801] ✨ Add API to return applicable provisioning policy for cloud/stage/workspace/resource
- [WFP-4776] ✨ UI - Limit cluster form by applicable provisioning policy
- [WFP-4695, WFP-4696] ✨ UI - Align Cluster Access Policy form and table to new form style
- [WFP-4694, WFP-4679] ✨ UI - Cluster Policy form + infoview
Azure AKS private endpoints for private clusters (incl. cross-tenant)
With this beta feature, if you run Wayfinder in Azure, it is now possible to provision private AKS clusters without establishing network connectivity between Wayfinder and the cluster's API, via Wayfinder's new capability to manage private link access to the cluster directly in its own subnet.
This also allows cross-tenant management of private clusters.
- [WFP-4574] ✨ Support Azure Private Link automation to Wayfinder's management network
- [WFP-4600] ✨ Update UI wording for Azure private endpoints
- [WFP-4599] ✨ Add necessary permissions for Azure private links
- [WFP-4740] ✨ UI - Support Azure cross tenant identities in Cloud Access Config form
Improvements and minor new features:
- ✨ Default plans updated - Kubernetes 1.30 and all packages updated to their latest supported versions
- [WFP-4880] ✨ Allow --force to override plan name when editing cluster and allow non-admins to use --force on their own resources
- [WFP-4712] ✨ Introduce Dynamic DNS operator for simpler DNS child zone management
- [WFP-4534] ✨ Add Globaldnszone v2beta3 api and handlers
- [WFP-4721] ✨ Allow platform access tokens to be used as bearer tokens for direct API access
- [WFP-4383] ✨ Use new consistent tagging strategy for all GCP resources created by wayfinder
- [WFP-4929] ✨ UI - Add stage and cluster columns to app environment table
- [WFP-4561] ✨ UI - Introduce consistent resource actions, handle owned/read-only resources on delete, improve minidoc rendering, improve handling of loading states
- [WFP-4264 follow-up] ✨/🐛 Stage and WFResourceAction tweaks
- [WFP-4734] ✨ UI - Create new Cluster form - only show cloud account picker if there's more than one
- [WFP-4826] ✨ UI - Form scope section: use dropdown with autocomplete instead of list of checkboxes for workspace selection
- [WFP-4561] ✨ UI - Improve handling of resources owned by a CI process in all standard forms
- [WFP-4561] ✨ UI - Allow force-overriding CI process ownership in all standard forms
- [WFP-4794] ✨ UI - Support scroll for long-formatted details in status 'details' modal
- [WFP-4707] ✨ UI - Add Child Zones tab to DNS zone infoview
- [WFP-4549] ✨ UI - Auto-increment version on cluster plans and packages on new version
- [WFP-4732] ✨ UI - New node pool modal form fixes and improvements
- [WFP-4804] ✨ CLI - Show rendered template values on
wf validate package - [WFP-4615] ✨ CLI - Introduce
wf validate clusterplan- [WFP-4613] ✨ Add controller to reconcile
ClusterPlanValidationto create clusters to validate plan - [WFP-4614] ✨ Support cluster upgrades in cluster plan validation
- [WFP-4617] ✨ CLI - Enhance
wf validate clusterplanoutput to follow build and package deployment
- [WFP-4613] ✨ Add controller to reconcile
Bug Fixes
- [WFP-4799] 🐛 Fix a null pointer exception when deleting clusters with an unexpecte…
- [WFP-4924] 🐛 Handle nil autoscaling configuration in cluster conversion
- [WFP-4890] 🐛 Only validate network plan capacity on cluster create (not update), allow --force to override
- [WFP-3176] 🐛 Remove stale clusters from package routing status, ensure we consider namespaces when checking cluster package releases
- [WFP-3225] 🐛 Package values: Ensure keys removed from valuesTemplate are removed from the underlying HelmRelease
- [WFP-4844] 🐛 Handle object modified error gracefully in cluster update subresource
- [WFP-4848] 🐛 Remove last vestiges of label 'appvia.io/managed' as a tag on AWS peering
- [WFP-4846, WFP-4728] 🐛 Cluster network cloud resource name mismatched with cluster cloud resource name
- [WFP-4808] 🐛 EKS KMS - Handle case where >1 KMS key is in disabled state
- [WFP-4754] 🐛 Convert labels between v2beta1 and v2beta2 cluster plans
- [WFP-4652] 🐛 Ensure RoleBinding name ends with an alphanumeric character.
- [WFP-4650] 🐛 Validate app provider against cluster provider
- 🐛 UI - Fix which endpoints are called for roles and groups on cluster access policy form
- 🐛 UI - Don't explode if there are no owners in the workspace
- [WFP-4921] 🐛 UI - Fix scoping of cloud resources by workspace in Cloud Resource app component form
- [WFP-4887] 🐛 UI - Fix a few remaining cluster plan ref issues with namespace form
- 🐛 UI - Correct cluster typo in new ClusterPlan version pop-up
- 🐛 UI - Fix hard to read form field helper text in dark mode
- [WFP-4860] 🐛 UI - Change markdown renderer to avoid weird bug and provide better control
- [WFP-4883] 🐛 UI - Fix "Add new cloud access..." link on peering rule form
- [WFP-4841] 🐛 UI - Fix Kyverno handling on Cluster Policy form/infoview
- [WFP-4638/4592/4796] 🐛 UI - Fix overview counts and details
- [WFP-4798] 🐛 UI - Fix formatting of dates on cluster details page
- [WFP-4769] 🐛 UI - Fix node pool edit immutability, improve machine type selector
- [WFP-4743] 🐛 UI - Fix validation preventing the creation of non-AKS cluster plans
- [WFP-4796/WFP-4592] 🐛 UI - Correct cluster and cloud access counts
- [WFP-4627] 🐛 UI - Fix workspace list members count
- [WFP-4827] 🐛 CLI - Ensure passwords are not echoed in textinput view
- [WFP-4781] 🐛 CLI - Add -c option to validate package to be consistent with help
- [WFP-4628] 🐛 CLI - Ensure
wf applyon existing object does not remove/overwrite 'appvia.io/createdBy' annotation
Release v2.8.8
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.8.8/wayfinder.sha256sums
Bug Fixes
- [WFP-4890] 🐛 Only validate network plan capacity on cluster create, not validate, and allow --force to override
- [WFP-3225] 🐛 Packages - Ensure keys removed from valuesTemplate are removed from the underlying HelmRelease
- [WFP-3176] 🐛 Remove stale clusters from package routing status
- [WFP-4794] 🐛 UI - Allow scrolling in status display for long formatted messages
- [WFP-4883] 🐛 UI - Fix changed 'add new cloud access' link on peering rule form
Release v2.8.7
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.8.7/wayfinder.sha256sums
Improvements
- [WFP-4880] ✨ Allow changing plan name when editing cluster with --force and allow non-admins to use --force if they have access to write the resource
Release v2.8.6
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.8.6/wayfinder.sha256sums
Bug Fixes
- [WFP-4848] 🐛 Ensure AWS peering works without deprecated 'appvia.io/managed' tag being required on routing table
- [WFP-4846, WFP-4728] 🐛 Ensure cluster network cloud resource name matches cluster cloud resource name
- [WFP-4627] 🐛 Fix workspace list members count
- [WFP-4796/WFP-4592] 🐛 Correct cluster and cloud access counts
- [WFP-4638/4592/4796] 🐛 UI/API - Fix overview counts and details
- [WFP-4827] 🐛 CLI - Ensure passwords are not echoed in textinput view
- [WFP-4799] 🐛 Fix exception when deleting clusters with invalid configuration
- [WFP-4798] 🐛 Fix formatting of dates on cluster details page
- [WFP-4781] 🐛 Adds the short -c option to validate package to be consistent with help
Release v2.8.3
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.8.3/wayfinder.sha256sums
Bug Fixes
- [WFP-4808] 🐛 EKS KMS - Handle case where >1 KMS key is in disabled state
Release v2.8.2
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.8.2/wayfinder.sha256sums
Bug Fixes
- [WFP-4769] 🐛 UI - Show immutable fields on node pools as read-only when editing existing node pools of a cluster
- [WFP-4769] 🐛 UI - Add search and fix 'self-closing' of machine type selector when preparing node pools
- [WFP-4754] 🐛 Fix conversion of cluster labels between v2beta1 and v2beta2 cluster plans
- [WFP-4650] 🐛 Ensure app provider check works if app applied out of order with appenv
- [WFP-4628] 🐛 Ensure 'createdBy' annotation preserved when amending objects via
wf apply
Release v2.8.1
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.8.1/wayfinder.sha256sums
Cluster plan versioning
In this release, Wayfinder now supports immutable versioning of Cluster Plans, allowing you to roll out changes to cluster plans across your fleet in a testable and deterministic way.
Clusters now refer to a plan and version and Wayfinder uses the details of the plan directly to build and manage the cluster. Creating a new plan version gives you a testable upgrade path for each plan, meaning you can use the exact same upgrade across all clusters on that plan, reducing bespoke per-cluster testing needs.
This release also introduces Compute Templates, which contain suggested node pool configurations that application teams can select from when self-serving clusters.
- [WFP-4396] ✨ Introduce new API version (v2beta2) for Cluster, ClusterPlan and ComputeTemplate
- [WFP-4404, WFP-4442] ✨ Reconcile clusters with versioned plans
- [WFP-4410] ✨ Allow kubeproxyaccess to clusters with versioned plans
- [WFP-4402] ✨ Enhanced validation of versioned ClusterPlans
- [WFP-4403] ✨ Enhanced validation for clusters using versioned plans:
- Non-provider-specific validation
- Providers details
- Node pools
- Networks
- Cost limits
- Deletion dependencies
- [WFP-4408] ✨ Add ComputeTemplate validation
- [WFP-4693] ✨ Enhance validation for node pool logical name on Cluster and Compute Template
- [WFP-4675] ✨ Enhance validation for quota limits on multitenancy clusters
- [WFP-0000] ✨ Drop description from individual node pools for Compute Templates and Clusters
- [WFP-4405] ✨ Add API support for cost estimates of individual node pools without a cluster
- [WFP-4486] ✨ Don't generate or use PackageUpdates for clusters using versioned plans with packages
- [WFP-4576] ✨ Remove unused GCP node pool fields (auto-upgrade, auto-repair - these are always set on GCP and the options were disregarded)
- [WFP-4531] ✨ Improve handling of nodepool update progress
- [WFP-4566] ✨ Add non-region specific instance type, GPU and Kubernetes version metadata and non-regional cost estimates using worldwide average pricing
- [WFP-4416] ✨ Add default compute templates
- [WFP-4470] ✨ Deprecate referencing cluster plans on AppEnvs
- [WFP-4410, WFP-4518] ✨ CLI - Update
wf create clusterto create clusters using versioned ClusterPlans and ComputeTemplates - [WFP-4517] ✨ CLI - Support
--compute-template-fileinwf create clusterto create using template file - [WFP-4519] ✨ CLI - Migrate to Bubbletea from PromptUI and Survey for CLI interaction and use to show compute template descriptions in
wf create cluster - [WFP-4641] ✨ CLI - Add
wf init clustercommand - [WFP-4642] ✨ CLI - Add
wf init clusterplancommand - [WFP-4513] ✨ CLI - Add
wf update clustercommand and API sub-resource - [WFP-4400, WFP-4401] ✨ UI - Implement new Cluster Plan list, Cluster Plan info page (incl. version list), Cluster Plan Version info page
- [WFP-4475] ✨ UI - Highlight legacy (unversioned) plans on cluster plan list
- [WFP-4399] ✨ UI - Implement new Cluster Plan form
- [WFP-4637, WFP-4563] ✨ UI - Only show packages appropriate for the cluster provider on cluster plan form, sort package versions descending
- [WFP-4545] ✨ UI - Handle versioned cluster plans on package tables
- [WFP-4407] ✨ UI - Add Compute Template list and infoview
- [WFP-4405] ✨ UI - Add Compute Template form
- [WFP-4557] ✨ UI - Add new Cluster table and infoviews
- [WFP-4557] ✨ UI - Add support for multi-tenant clusters to new Cluster infoview, new namespace form
- [WFP-4607] ✨ UI - Add multi-tenancy / quota-limit options to Cluster infoview
- [WFP-4605] ✨ UI - Add quota limit selector to new namespace form
- [WFP-4606] ✨ UI - Add PSS support to new namespace form
- [WFP-4409] ✨ UI - New cluster form
- New plan selection modal, filtered by scope and provider
- Allow selection of cluster plan version
- Add estimated costs to cluster form summary
- Improved compute template and cluster plan pickers
- Add common node pool form for Compute Template and Cluster forms
- Update node pool form look and feel on compute template and cluster forms
- [WFP-4455] ✨ UI - Prevent editing of pre-v2.8 clusters at v2beta2 without migration
- [WFP-4470] ✨ UI - Update create app environment form for versioned cluster plans
Provisioning policies
Along with versioned cluster plans, this release introduces a new Provisioning Policy resource allowing you to restrict self-service of clusters, replacing the 'policy' construct on older cluster plans.
Limits can be configured for the maximum estimated costs for a cluster, along with what regions, instance types, number of nodes and the number of clusters can be provisioned.
A UI to manage provisioning policies will be available in a future release.
- [WFP-4496] ✨ Add ProvisioningPolicy and evaluate in Cluster validation
Other enhancements and new features
- [WFP-4598] ✨ Add Azure cross tenant Cloud Identity support
- [WFP-4692] ✨ Allow securityContext.capabilities to be overridden for a Container within an App Component
- [WFP-4609] ✨ Allow platform access tokens to assign access roles to other access tokens if added to a Wayfinder group permitted by the access policy
- [WFP-4137] ✨ Improve validation for Cluster Network Plans on AWS
- [WFP-4381] ✨ Consistent tagging of Azure resources
- [WFP-4382] ✨ Consistent tagging of AWS resources
- [WFP-4383] ✨ Consistent tagging of GCP resources
- [WFP-4552] ✨ UI - Add infoview for DNS Zones
- [WFP-4562] ✨ UI - Add infoview for Stages
- [WFP-4231] ✨ UI - Allow usage of private GitHub repositories when searching for cloud resources
- [WFP-4567] ✨ UI - Add status tab to Cloud Access and Cloud Identity infoviews
- [WFP-4551] ✨ UI - Add infoview for Cloud Identities
- [WFP-4550] ✨ UI - Add infoview for Cloud Accesses
- [WFP-4556] ✨ UI - Add infoview for Platform Secrets
- [WFP-4479] ✨ UI - Add 'Download YAML' button to all new-style forms
- [WFP-4549] ✨ UI - Auto-increment version on cluster plans and packages on new version
- [WFP-4646] ✨ CLI - Use WAYFINDER_WORKSPACE as fallback if no explicit workspace set
- [WFP-4603] ✨ CLI - Allow
wf validate packageto work on any stage - [WFP-4494] ✨ CLI - Support exporting all versions of versioned resources with
wf export - [WFP-4526] ✨ CLI - Add help to
wf init - [WFP-4527] ✨ CLI - Update
wf init packageto always return repositoryRef and repo (if not already existing) - ✨ CLI -
wf applysmall improvements - use deterministic ordering, check versioned resources have spec.version set
Bug Fixes
- [WFP-4621] 🐛 Fix enqueued namespace for App Certs operator DNS watch
- [WFP-4582] 🐛 Cluster controller deletes ClusterNetwork explicitly ensuring peering not deleted early; add timeouts for deletion activities
- [WFP-4581] 🐛 Fix network policy generation for inter-container-component app dependencies
- [WFP-4500] 🐛 Fix issue preventing the creation of additional spot pools on Azure for existing clusters
- [WFP-4507] 🐛 Ensure legacy WorkloadIdentities owned by packages are migrated correctly
- [WFP-4593] 🐛 Add default fallback Azure region for child DNS zones if none available from parent zone options
- [WFP-4507] 🐛 Fix legacy role parameters for packages with workload IDs
- [WFP-4652] 🐛 Ensure RoleBinding name ends with an alphanumeric character
- [WFP-4650] 🐛 Validate app provider against cluster provider
- [WFP-4580] 🐛 CLI -
wf applyskips existing workspaces when applying - [WFP-4610] 🐛 CLI - Add
DefaultWorkspaceGroupto resource types - [WFP-4585] 🐛 CLI - Fix identifier column in
wf get cloudaccessconfig - [WFP-4586] 🐛 CLI - Can't delete owned
CloudAccessConfigwithwf delete cloudaccessconfig - [WFP-4509] 🐛 CLI - Support rendering packages in wf get for old package API version v2beta1
- [WFP-4438] 🐛 UI - Fix multiline YAML view of
spec.templateValueson packages - 🐛 UI - Fix wrong version being reported in toast messages on version lists
Release v2.7.4
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.7.4/wayfinder.sha256sums
Packages
This release introduces a new, fully featured way to manage and deliver super-charged Helm packages across your fleet of clusters. Maintain a single, immutable, versioned definition of your package which can apply across your estate, and reference those from cluster plans.
- [WFP-4046] ✨ Introduce new v2beta2 API for packages
- [WFP-4083, WF-4049] ✨ Validate helm and add deprecation warnings to legacy fields on new packages
- [WFP-4129] ✨ Validate variables used in package templates
- [WFP-4243] ✨ Validate required workload identity variables are consumed in package Helm values template
- [WFP-4023] ✨ Validate package additional manifests only define a single document per manifest
- [WFP-4119] ✨ Use new template values when reconciling packages
- [WFP-4104] ✨ Implement detailed package release status for new-style packages
- [WFP-4419] ✨ Move built-in packages to external repo (charts.wayfinder.run)
- [WFP-4195] ✨ Add packages to cluster plans, mark package label selectors deprecated
- [WFP-4377] ✨ Check packages defined on the cluster plan are deployed successfully before marking cluster as ready
- [WFP-4210] ✨ Add support for private package repositories in new packages
Package Workload Identities
Use our templating language to define the right permissions for the Helm package in the cloud account of your clusters, for example:
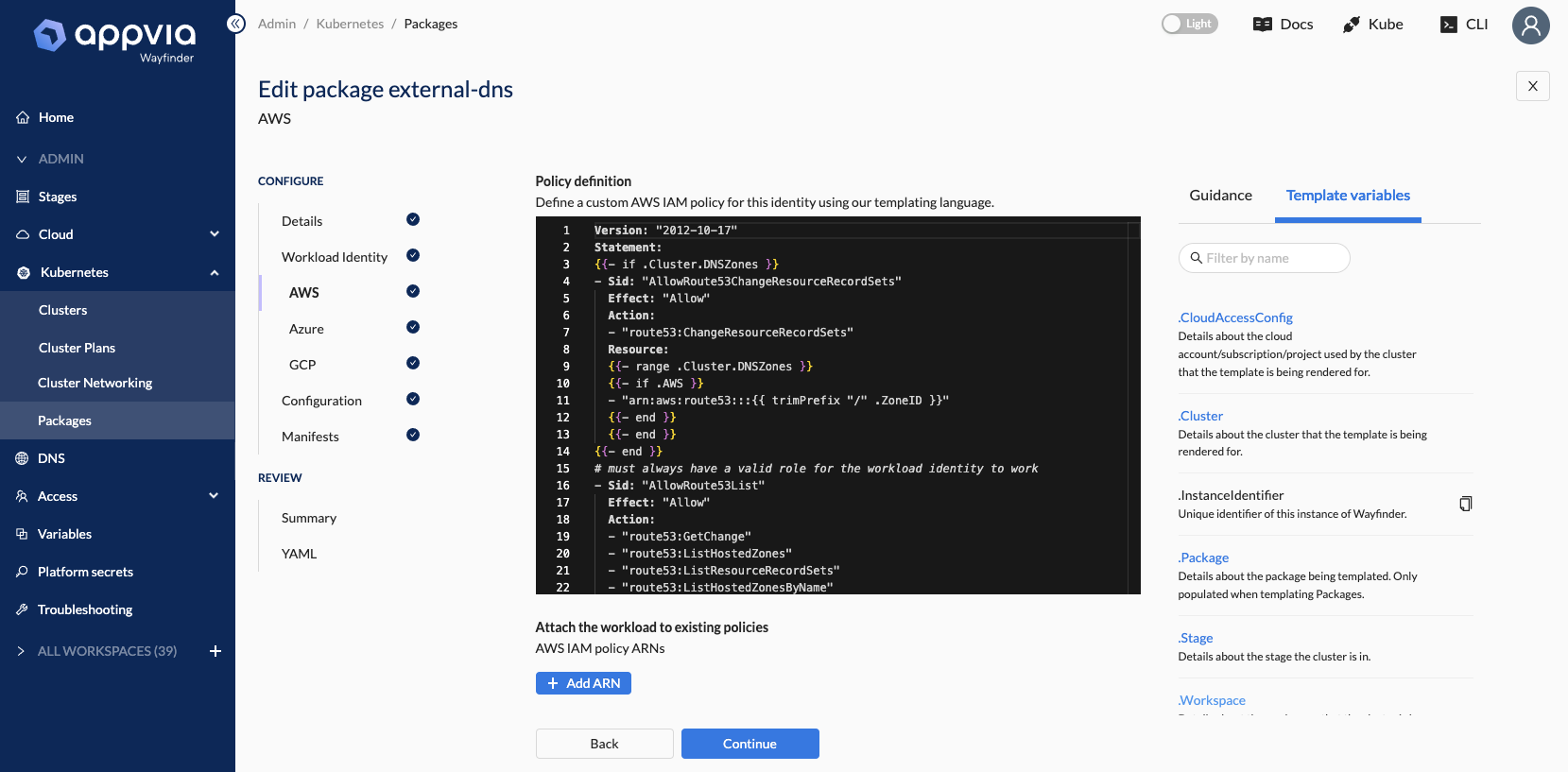
- [WFP-4236] ✨ Add new workload identity fields for new package templates
- [WFP-4310] ✨ Support GCP templated role bindings for new package workload identities
- [WFP-4237] ✨ Support AWS templated IAM policy for new package workload identities
- [WFP-4238] ✨ Support Azure templated IAM role assignments for new package workload identities
- [WFP-4328] ✨ Improve validation around workloadidentities on GCP
Package templated Helm values
Ensure the Helm values are templated correctly for every cluster:
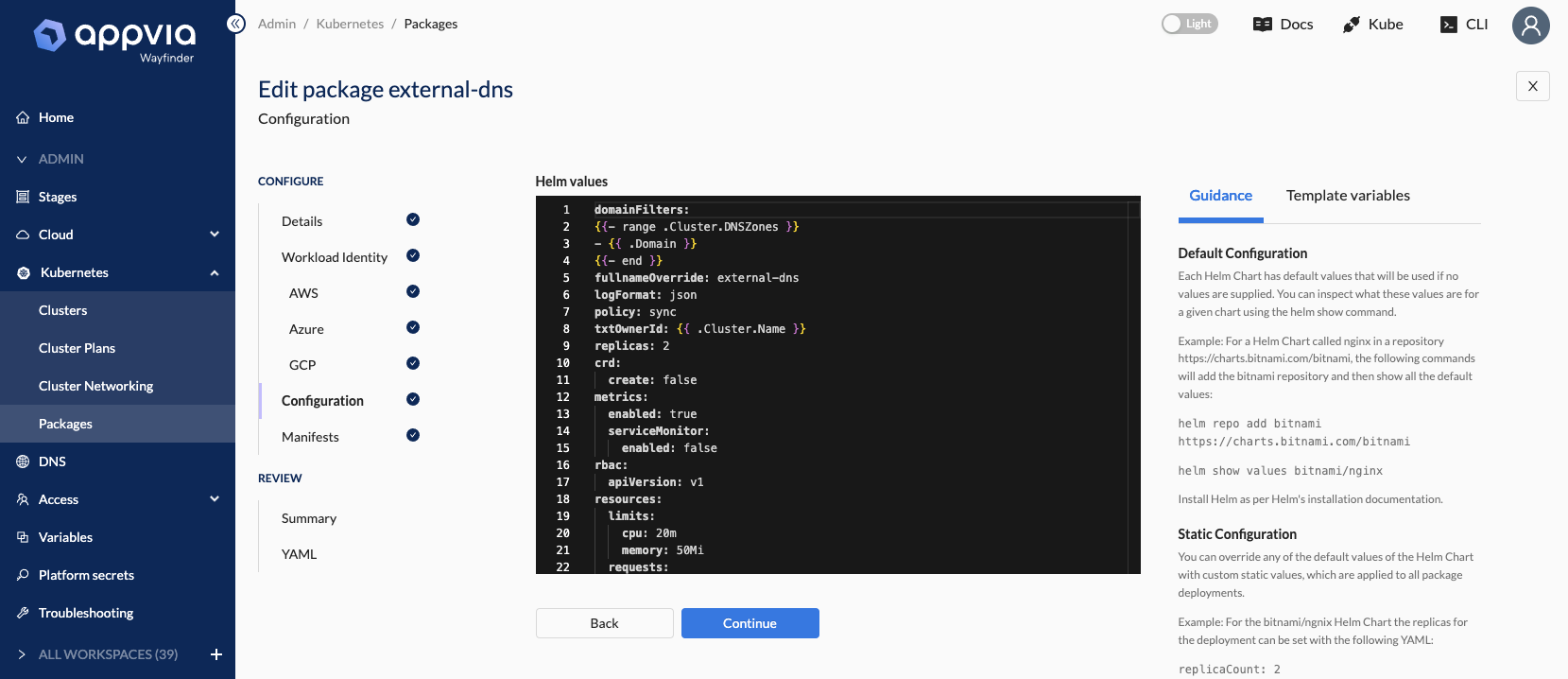
- [WFP-4047] ✨ Add templated
spec.helm.valuesTemplatefor new packages
Package additional manifest configuration
Ensure your package is ready to consume without maintaining your own additional Helm charts by layering on any additional post-install configuration of your package:
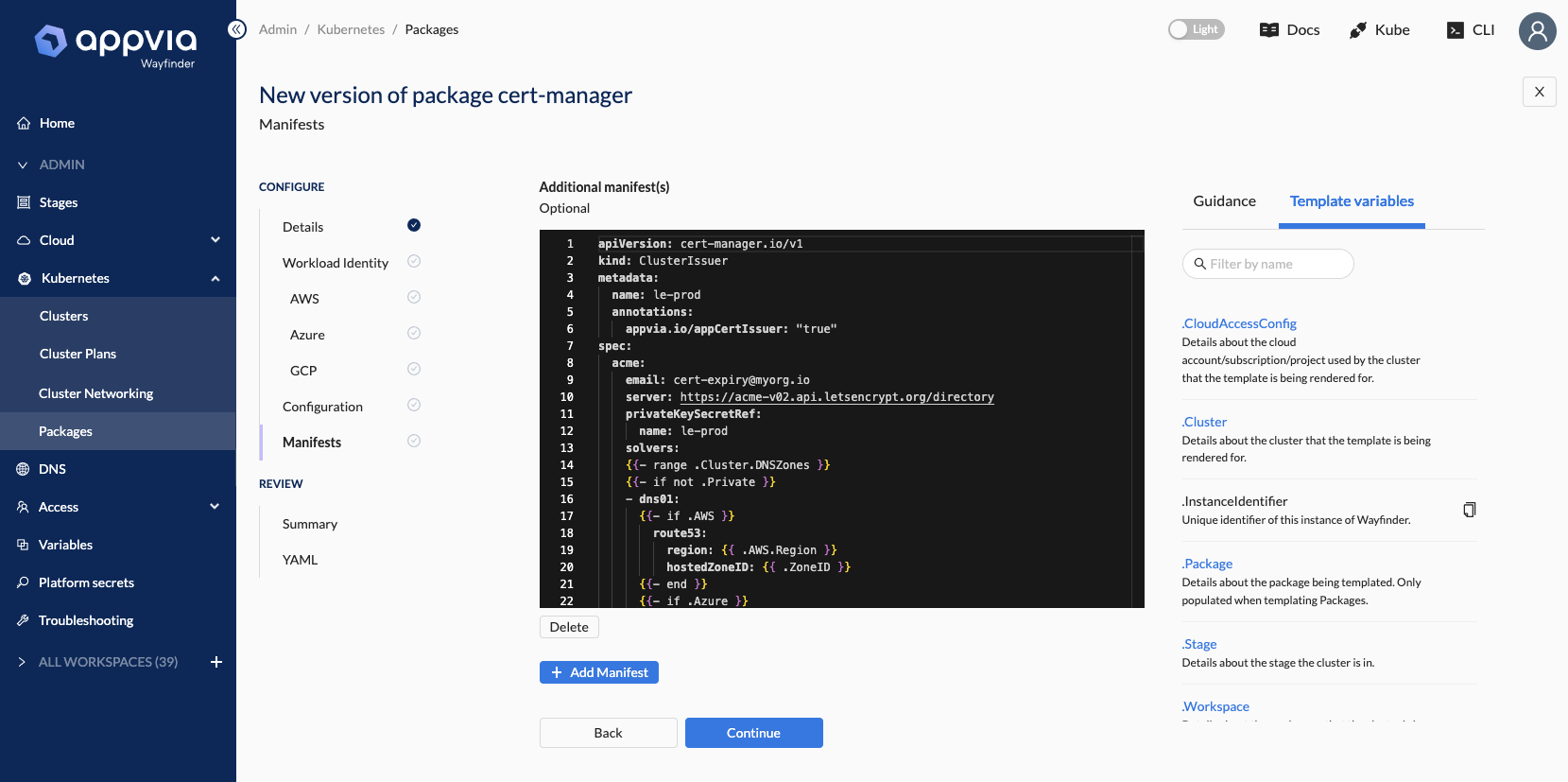
- [WFP-4023] ✨ Add templated manifests to new packages
Initialise and manage packages quickly through UI and CLI
Use the new interactive package definition UI to create a full package definition easily, or use wf init package from the CLI to quickly skeleton out a package definition by providing a few basic values. Take the resulting definition and manage it through CI or apply directly to Wayfinder.
New package and package version tables let you quickly understand where your packages are used and link to the individual releases on each cluster.
- [WFP-4335] ✨ UI - Add form to create packages
- [WFP-4337] ✨ UI - Support definition of Workload Identity in package form
- [WFP-4338] ✨ UU - Support definition of additional manifests in package form
- [WFP-4336, WFP-4364] ✨ UI - Add package repository in-line modal and form
- [WFP-4420] ✨ UI - Add mini-docs to package and repo forms
- [WFP-4340] ✨ UI - Introduce code editor to manage templates for workload identity, helm values and additional manifests in packages
- [WFP-4449, WFP-4456] ✨ UI - Add 'New version' functionality to package form and tables, allowing creation of new versions of existing packages
- [WFP-4446, WFP-4425] ✨ UI - Ensure pre-v2.7 legacy packages cannot be edited through UI
- [WFP-4333] ✨ UI - Add new package and package version tables
- [WFP-4334] ✨ UI - Add new repository table
- [WFP-4366] ✨ UI - Add package and repository info pages
- [WFP-4365] ✨ UI - Add cluster package release info detail page
- [WFP-4196] ✨ UI - Add packages to cluster plan view/edit
- [WFP-4348] ✨ UI - Support package versions in cluster plan view/edit
- [WFP-4123] ✨ CLI - Add
wf init packageto skeleton a package definition from a repository, chart and version - [WFP-4124] ✨ CLI - Add support for private Helm repositories to
wf init package - [WFP-4242] ✨ CLI - Add support for
--enable-workload-identitytowf init package - [WFP-4373] ✨ CLI - Sort
chartandversionwhen picking interactively inwf init package
Easy validation flow to test your packages
Use wf validate package to quickly iterate on your package definitions using a test cluster before adding them to cluster plans.
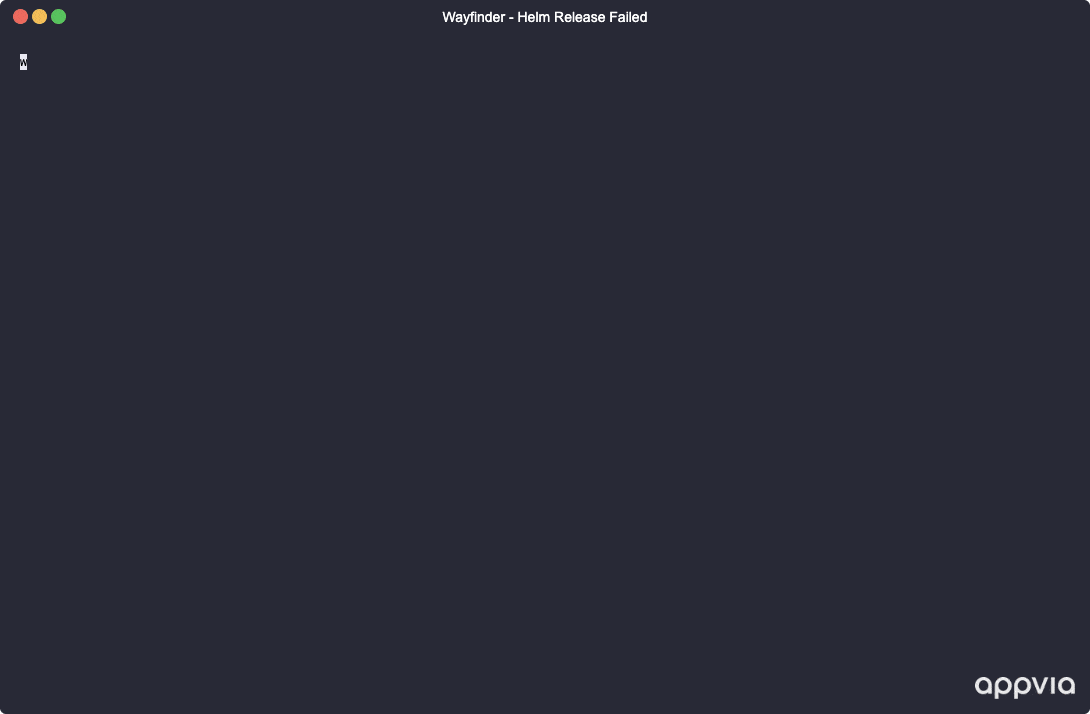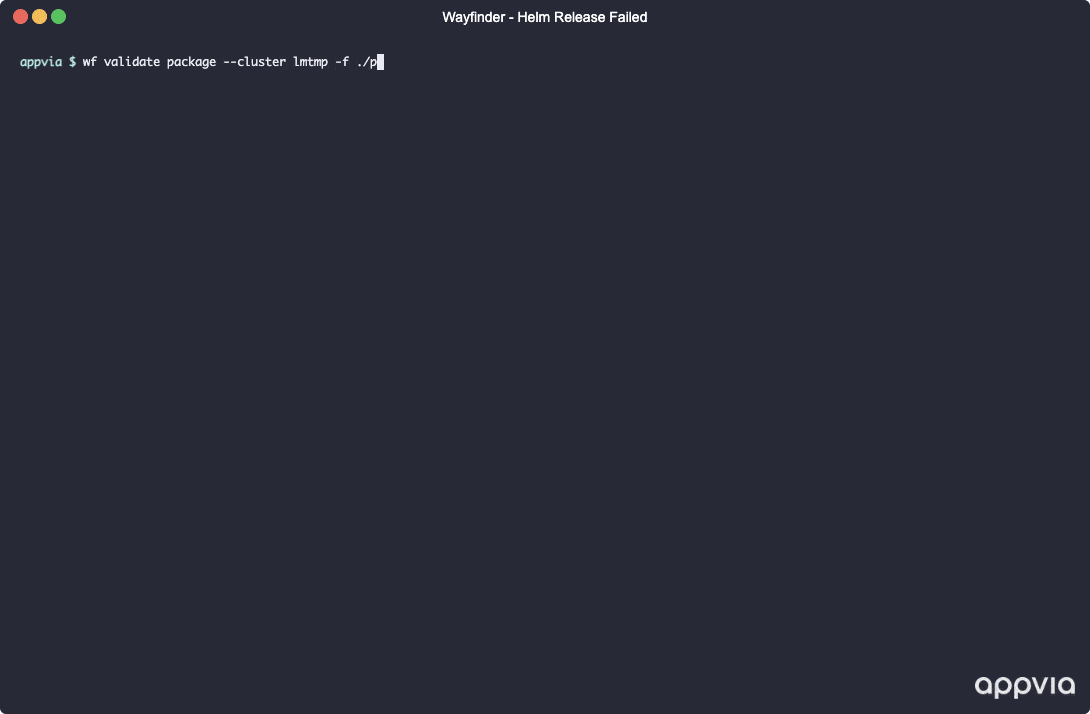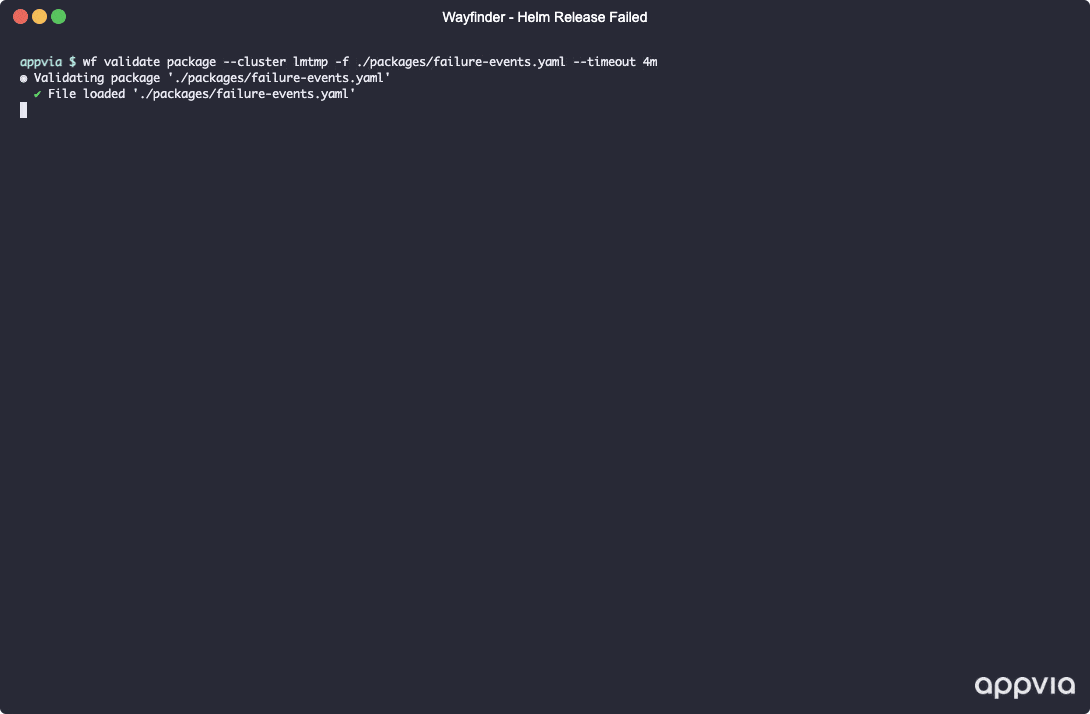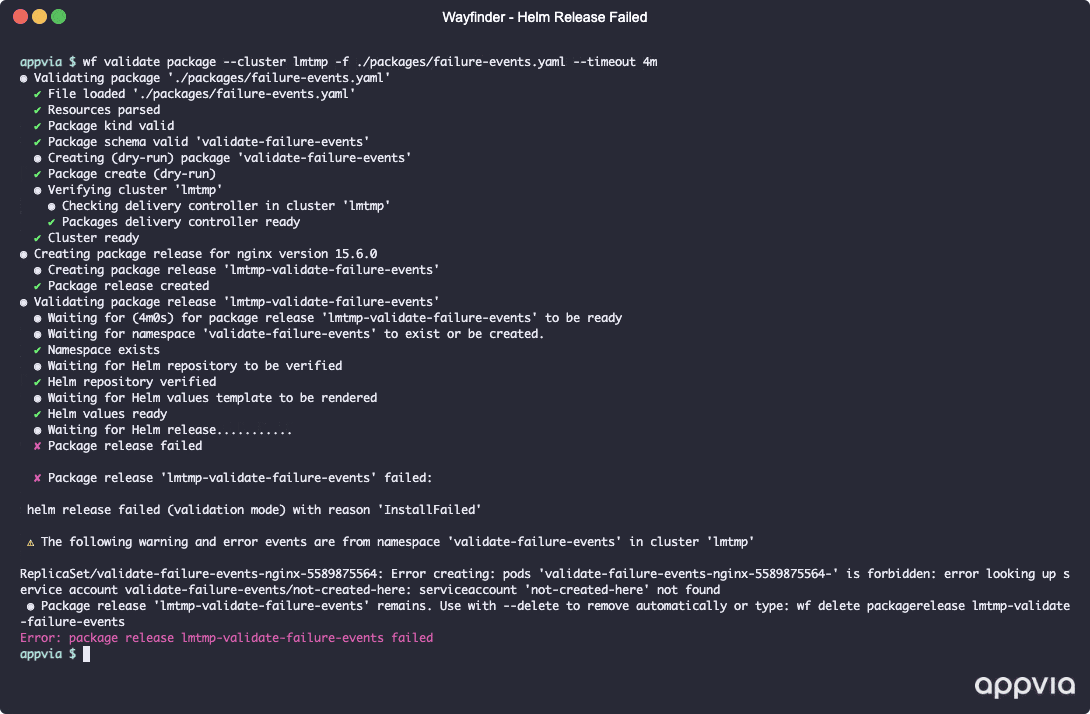
- [WFP-4142] ✨ CLI/API - Add
wf validate package -f ./package.yamlcommand and backend support - [WFP-4110] ✨ Restrict
wf validate packageto stages annotated for package validation - [WFP-4221] ✨ CLI - Add feedback to
wf validateoutput when template(s) are invalid - [WFP-4221] ✨ CLI/API - Add support for
wf validate package --allow-updateto test updates to existing packages - [WFP-4254, WFP-4256] ✨ CLI - Add support for
wf validate package --deleteto remove package release after test or timeout and wait for deletion - [WFP-4248] ✨ CLI - Ensure errors for missing clusters and clusters not being ready to accept packages are output on
wf validate package - [WFP-4457] ✨ CLI - Support
wf validate package --name PKG --version PKGVERto validate existing package versions already applied to WF
Versioned packages
Wayfinder now keeps all versions of a given package definition. As you create or amend packages, setting a different spec.version will ensure that both
the old and new version are preserved. This allows you to safely produce new package versions, test them, then update your cluster plans with the new
versions once ready.
In the next release (v2.8) this versioning will be extended to cluster plans themselves to enhance your control over upgrades for your teams' clusters.
- [WFP-4284, WFP-4285, WFP-4286, WFP-4345] ✨ Introduce resource versioning at the API layer for v2beta2 Package CRD
- [WFP-4344] ✨ Allow package versions to be updated if not referenced by cluster plans
- [WFP-4467, WFP-4463] ✨ CLI - Support versioned resources in
wf diff - [WFP-4341, WFP-4464] ✨ CLI - Support versioned resources in
wf applyincluding pruning versioned resources
Upcoming removal of 'label-selector' packages
After upgrading to v2.7, you should migrate any existing custom package definitions to new-style versioned packages referenced by cluster plans. If you have any questions about migration, contact Appvia Support for assistance.
The previous version of packages using label selector targeting is deprecated and will be removed in a future release.
Template variables
Wayfinder now provides a rich set of template variables you can use in your package configuration, along with a set of useful CLI and UI tools to understand those variables and check their values.
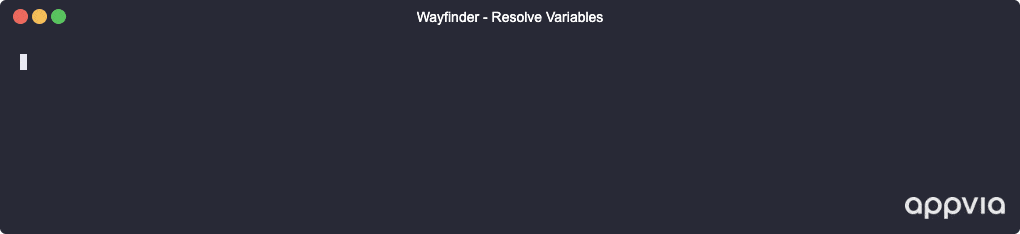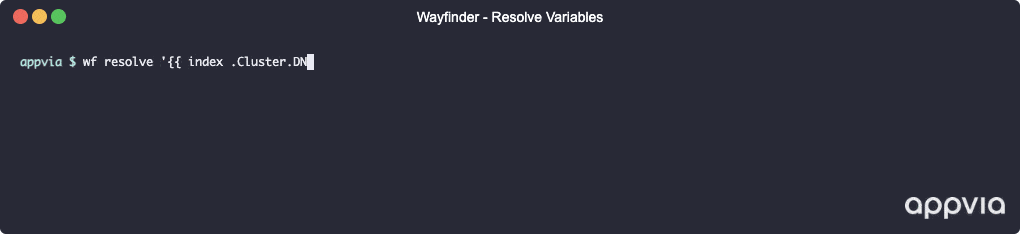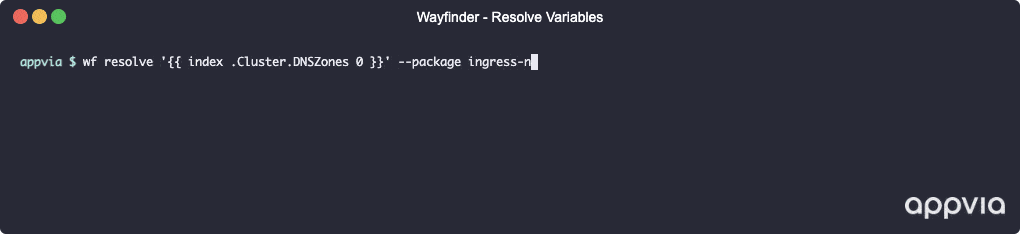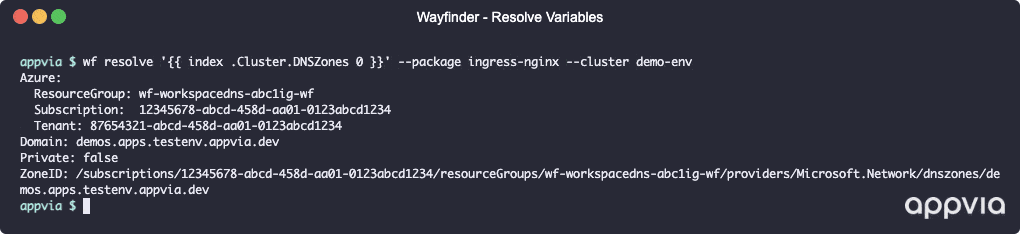
- [WFP-4034, WFP-4040] ✨ Implement initial templating library for package usage
- [WFP-4035] ✨ Add API for describing and resolving template variables
- [WFP-4037] ✨ CLI - Add
wf describe varscommand to list available variables for templates - [WFP-4041] ✨ CLI - Add
wf resolvecommand to resolve template variables - [WFP-4039] ✨ UI - Add variables page to see available variables for templates
- [WFP-4292] ✨ UI - Add resolve functionality to variables page
- [WFP-4339] ✨ UI - Add inline template variable widget to packages form
- [WFP-4084] ✨ Support
toYamlin templates - [WFP-4092] ✨ Review all text and add examples for template describe
- [WFP-4035] ✨ Support maps and lists in template variables
Platform Secrets
You can now manage platform-level secrets for packages, cloud identities, Terraform repositories and Helm repositories using the new Platform Secrets feature.
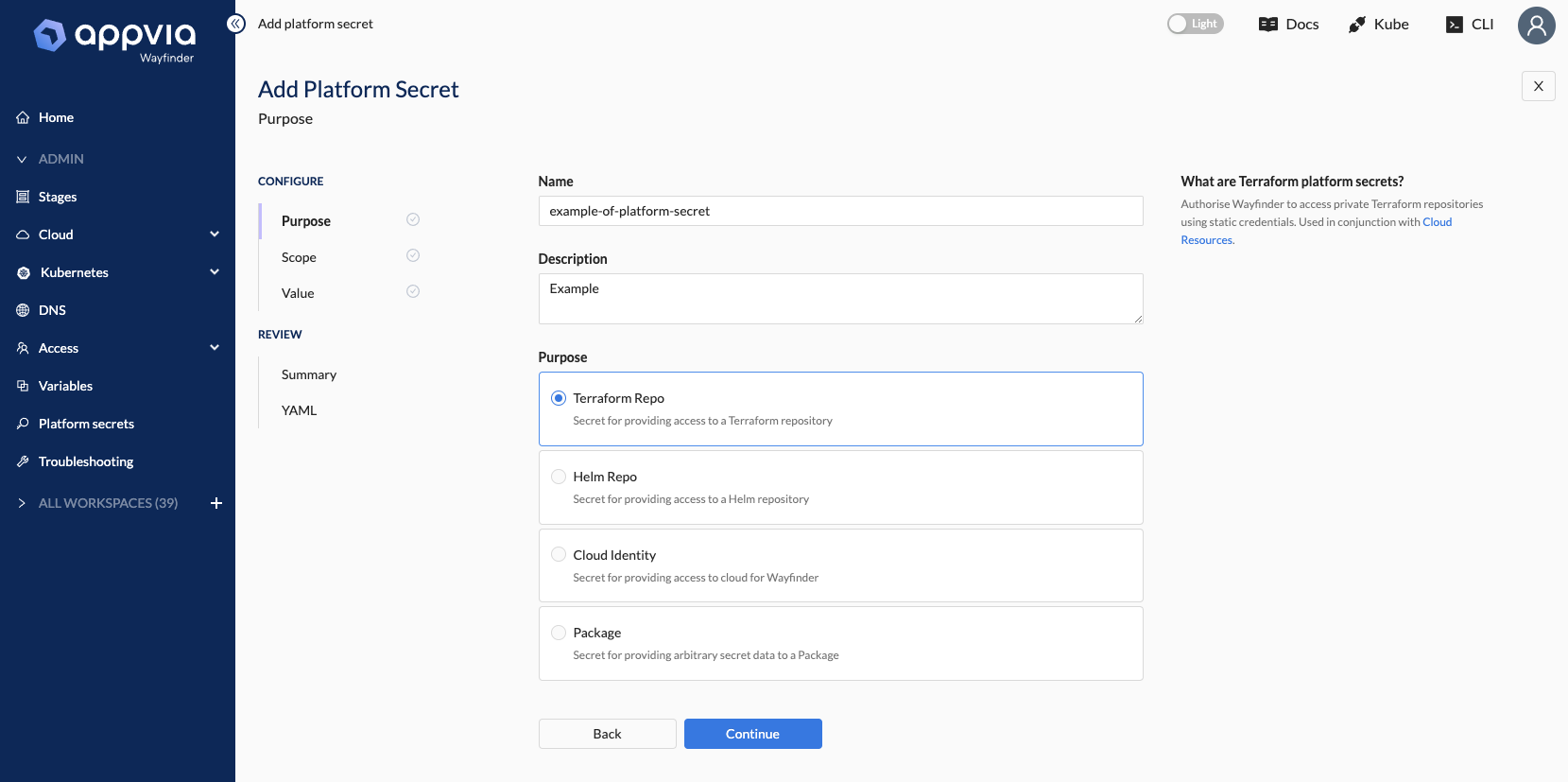
- [WFP-4232] ✨ Add API for structured platform secrets to be used from CLI and UI
- [WFP-4232] ✨ CLI - Add
wf create platformsecretcommands for supported secret purposes:helmrepo,package,terraformrepoandcloudidentity - [WFP-4303, WFP-4368, WFP-4304] ✨ UI - Add platform secret form and list
- [WFP-4298] ✨ Add new secret type for TLS certificates for Helm repository auth
- [WFP-4324] ✨ Add ability to use platform secrets for private terraform repos in Terranetes API
- [WFP-4234, WFP-4275] ✨ Distribute platform secrets for app cloud resources where the cloud resource plan references a private terraform repository
Other enhancements and new features
- [WFP-4418] ✨ Wait for network to delete if owned by the cluster, ensuring cluster doesn't disappear until network deletion completed
- [WFP-4291] ✨ Add
OwnedResourcesto the status of all resources to identify cloud resources and other Wayfinder resources owned by that resource - [WFP-4356] ✨ Handle unexpected errors in controllers gracefully
- [WFP-4153] ✨ Add basic support for patching env variables from AppEnv variables in deployment templates
- [WFP-4162] ✨ Improve error message from Kubernetes API proxy when access from your IP is forbidden
- [WFP-4294] ✨ UI - Add confirmation prompt on any navigation from a form if values have been edited
- [WFP-3980] ✨ UI - Add close/back buttons to forms, show prompt if form has been modified
- [WFP-4290] ✨ UI - Support ANSI colour display in logs
- [WFP-4247] ✨ UI - Tweaks/improvements to DNS zone form
- [WFP-4259] ✨ UI - Add option to view YAML in default table actions
- [WFP-4318] ✨ CLI - Improve SSO login splash-screen (try
wf loginif you use SSO, you won't be disappointed!) - [WFP-4350] ✨ CLI - Add generic
wf describe TYPE NAMEcommand to show the owned resources for a given resource recursively - [WFP-4291] ✨ CLI - Include number of child resources owned by PackageRelease and WorkloadIdentity in
wf get - [WFP-4218] ✨ CLI - Ensure validation warnings are shown generically, where not specifically processed by a handler
- [WFP-4181] ✨ CLI - Add generic filter support for
wf getcommands - [WFP-4012] ✨ CLI -
wf deploy --wait-for-readywill now wait for HTTP endpoint to be populated before returning if a component is exposed - [WFP-4220] ✨ CLI -
wf apply / wf diffnow show all validation errors, rather than just the first
Bug Fixes
- [WFP-4450] 🐛 Cluster network deletion not triggered unless cluster deleted with cascade
- [WFP-4447] 🐛 Correct NGINX ingress controller name in ingress-nginx-internal default package
- [WFP-4363, WFP-4190] 🐛 Ensure access role bindings (for assign/assume) have max 63 char names, improve
wf get accessrolebinding - [WFP-4353] 🐛 Ensure non-admins can't assign platform roles at workspace scope, make workspace.cloudaccessmanager platform scoped
- [WFP-4330] 🐛 Ensure all packages from deleting clusters are marked as deleted
- [WFP-4253] 🐛 Ensure ClusterNetworkPlan controller re-verifies plan when stages are changed
- [WFP-4302] 🐛 Fix excessive memory consumption on Azure instance type metadata refresh
- [WFP-4296] 🐛 Ensure AppEnv controller handles case when no ingress classes are available
- [WFP-4163] 🐛 Fix app DNS zone generation
- [WFP-4423] 🐛 Requeue on conflict in package release reconciliation
- [WFP-4222] 🐛 Ensure PackageReleases don't inherit OwnedBy labels from Packages
- [WFP-4468] 🐛 CLI -
wf applydoes not apply resources with the same name in different workspaces - [WFP-4134] 🐛 CLI - Fix
wf applywith prune attempting to delete workspaces in certain scenarios - [WFP-4164] 🐛 CLI -
wf create appenv- error if--clusterstage does not match--stageflag - [WFP-4170, WFP-4135] 🐛 CLI - Ensure client is initialised with the right profile / base URL before processing any flags
- [WFP-4325] 🐛 UI - DNS - Fix radio value for packages auto-provision option
- [WFP-4193] 🐛 UI - Improve generic error handling for form and API validation errors
- [WFP-4244] 🐛 UI - Ensure DNS zone Delegation step renders when no condition is met
- 🐛 UI - Fix cloud identity modal on cloud access config form not being re-initialised correctly on re-entry
Release v2.6.5
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.6.5/wayfinder.sha256sums
Improvements and Bug Fixes
- [WFP-4176] ✨ UI - Add "Name in [cloud]" text to cluster details page
- [WFP-3683] ✨ CLI - Add
--ownerand--prunetowf diff - [WFP-4165, WFP-4173] 🐛 UI - Fix a couple of broken URLs
- [WFP-4088] 🐛 Add read only annotation to RepositoryRelease objects as they are system-controlled
- [WFP-2587] 🐛 CLI -
wf applywith--dry-run serverdoes client side dry run with missing workspace - [WFP-4204] 🐛 UI - Stop workspace submenu from sticking in collapsed nav mode
- [WFP-4097] 🐛 UI - Fix cancel button URL on cluster network plan edit page
- [WFP-4215] 🐛 UI - Stop (cloud resource) component page from breaking if cloud resource component does not have variablesFrom defined on spec
Release v2.6.4
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.6.4/wayfinder.sha256sums
Private DNS support
This release introduces full support for Private DNS zones on AWS, Azure and GCP. This allows you to extend Wayfinder's auto-provisioning of DNS zones for your clusters and apps to fully-private DNS within your cloud environment.
With this change, a new version of the GlobalDNSZone and DNSZone resources has been introduced (v2beta2) and the existing version (v2beta1) is now deprecated and will be removed in v2.7. Please update any stored GlobalDNSZone or DNSZone resources in your repositories to the new API version after upgrading.
- [WFP-3897] ✨ Introduce DNSZone and GlobalDNSZone v2beta2 API versions with full support for private DNS zones
- [WFP-3843] ✨ Implement private DNS support for Azure Private DNS
- [WFP-3844] ✨ Implement private DNS support for AWS Route53 private zones
- [WFP-3846] ✨ Implement private DNS support for GCP Cloud DNS private zones
- [WFP-3860] ✨ Add secondary external DNS package for Azure to support Azure Private DNS
- [WFP-3900] ✨ UI - New DNS configuration form
- [WFP-3847] ✨ UI - Support private DNS configuration for all providers on new DNS form
- [WFP-3971] ✨ UI - New DNS zone list with more information
- [WFP-4081] ✨ Validate DNS domains are unique - prevent creation of multiple DNS zones with the same provider using the same domain
- [WFP-4013] ✨ Tighten reconciliation criteria on package releases / updates w.r.t. DNS zones
- [WFP-4054] 🐛 Ensure DNS zones fail validation where cloud access config required but not supplied
- [WFP-4053] 🐛 UI - Perform cascading delete of DNS zones when child zones exist
- [WFP-3862] ✨ Support Custom DNS resolvers for Azure vNets
- [WFP-3839, WFP-3978] ✨ Add route / next hop support for Azure cluster network plans
- [WFP-4005] ✨ Support privatelink DNS zone vNet links in AKS cluster plan (required only when using private clusters with custom DNS resolution)
wf apply / wf diff improvements
The validation performed by Wayfinder has been improved to return warnings for missing dependencies, allowing
wf apply and wf diff to intelligently re-order multiple resources as required so they apply successfully.
- [WFP-3986] ✨ Return 'dependency missing' warnings instead of validation errors on missing dependencies for:
- Apps: AppEnv to CloudAccessConfig, AppEnv to Application, AppComponent to Application, AppComponent to other AppComponents
- Cloud Access: CloudAccessConfig to Stage, CloudAccessConfig to CloudIdentity
- Clusters / Networks: Cluster to CloudAccessConfig, ClusterPlan to ClusterNetworkPlan, ClusterNetwork to CloudAccessConfig, ClusterNetworkPlan to AssignableNetwork
- DNS: DNSZone / GlobalDNSZone to CloudAccessConfig
- [WFP-3966] ✨ Handle warnings in
wf applyandwf diff:- Use returned warnings to re-order resources being applied, allowing (e.g.) an application and its components to be configured in the same pass
- Apply workspaces (and wait for ready) before workspace-dependent resources, allowing configuration of a workspace and its (e.g.) CloudAccessConfigs in the same pass
- These improvements resolve:
- [WFP-3962] 🐛 Dry run and apply of full application (with appenv and app component) may not work due to ordering
- [WFP-3497] 🐛
wf diffdoes not work with resource dependencies (such as ClusterNetworkPlan to AssignableNetwork) when both are being created - [WFP-3536] 🐛 Dry run and apply of container app components that depend on cloud resource app components may not work due to ordering
App environment variables
This release introduces variables on application environments. This allows container and cloud app components to use variables which vary across your environments.
- [WFP-4149] ✨ Support variables on App environments to use as inputs for cloud resource components and as container environment variables
- [WFP-4152] ✨ Add API support for AppEnv variables
- [WFP-4153] ✨ Add support for setting AppComponent container environment variables from AppEnv variables
- [WFP-4154] ✨ Add support for setting AppComponent cloud resource inputs from AppEnv variables
- [WFP-4160] ✨ Add validation error if variable required by AppComponent is not set on AppEnv when using
wf deploy - [WFP-4156] ✨ UI - Add support for setting variables on create/edit of AppEnv
- [WFP-4158] ✨ UI - Add support for "Add from App Env" on container and cloud resource component definition
- [WFP-4155] ✨ CLI - Add
--varflag towf create appenvto specify variables at AppEnv creation times - [WFP-4177] ✨ Add all user-defined appenv variables to wf-environment config map for OwnManifest components
wf access and wf kubeconfig improvements:
- [WFP-3974] ✨ wf access namespace / wf create token improvements
- Adds
--timeoutflag towf assumeandwf access cluster|namespace|envto control amount of time to wait for the access binding to be ready - Adds validation to
wf access cluster|namespace|envto error if a role is requested when authenticated as an access token (access tokens are not able to assume roles)
- Adds
- [WFP-3981] ✨ CLI - Re-use existing session if present (unless explicit
--expireor--force-newrequested) inwf access cluster|namespace|env - [WFP-3981] ✨ CLI - Make default expiry time 1hr in
wf access cluster|namespace|env - [WFP-3975] ✨ UI - Add example command to set kubeconfig in cluster access instructions
- [WFP-3981] 🐛 Fix
--no-context-changeinwf access cluster|namespace|env - [WFP-3047] 🐛 CLI - Don't prevent
wf accessif not a member of the workspace locally in CLI - defer to the access policy
Peering improvements
Validation and required fields have been improved on peering rules, and the error handling on the resulting peerings has been improved to better identify issues with peering set-up.
- [WFP-3987] ✨ Improve validation of peering rules, tidy required fields per provider
- ✨ Add clearer error reporting to Peering status on Azure
- [WFP-4082] 🐛 Ensure peering rules have a status so
wf apply --wait-for-readyworks with peering rules - [WFP-3979] 🐛 UI - Improve Peering rule form
- [WFP-3998] 🐛 UI - Prevent Peering Rule form from refreshing on edit
Other enhancements and new features
- [WFP-4096] ✨ Support Azure Virtual Network Service Endpoints in networks/plans
- [WFP-3966] ✨ Ensure CloudAccessConfig dependencies are checked on delete:
- Clusters
- ClusterNetworks
- AppEnvs
- DNSZones / GlobalDNSZones
- PeeringRules
- [WFP-4003] ✨ Add unique reqID to troubleshooting logs for each reconcile & API/webhook request
- [WFP-4032] ✨ Update Kyverno policy to support internal-ingress network policy objects for cert-manager challenges
- [WFP-3959] ✨ CLI - Add error if attempting to delete non-existent member with
wf delete member - [WFP-4151] ✨ UI - Add table refresh button for our common tables
- Refresh button now available on most tables in UI
- Improved efficiency on refreshing to load table instead of individual rows when rows are in progress
- ✨ Update default Terranetes version to v0.7.8
Bug Fixes
- [WFP-4055] 🐛 Validate that spec.key is set equal to metadata.name on a workspace
- [WFP-4001] 🐛 Fail early for app with name 'wf-' so it doesn't break at deployment time
- [WFP-3956] 🐛 Fix user invites (to workspaces) and invite generation
- [WFP-4054] 🐛 Don't create appdns zones if no cloud access config available
- [WFP-3960] 🐛 CLI - Make
wf get memberswork correctly for non-admins - [WFP-4065] 🐛 CLI - Improve
wf create cloudaccessconfigoutput formatting; fix--role-name - [WFP-4019] 🐛 UI - Fix users link on workspace overview page
- [WFP-4002] 🐛 UI - Prevent 'Access' item in 'Cloud access' section from losing highlight when 'Cloud Identites' tab selected
- [WFP-3958] 🐛 UI - Render correct fields in Cloud Access configuration permissions step when authentication type is changed for existing cloud access
- [WFP-4090] 🐛 UI - Update doc URLs on access token usage modal
- [WFP-4145] 🐛 UI - Fix redirect on creating or saving a Cloud Resource Plan
Release v2.5.1
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.5.1/wayfinder.sha256sums
New UI navigation structure
This release introduces new, clearer navigation to the UI. Clusters can now be found in both workspace and administrative sections, allowing workspace members to see their own clusters.
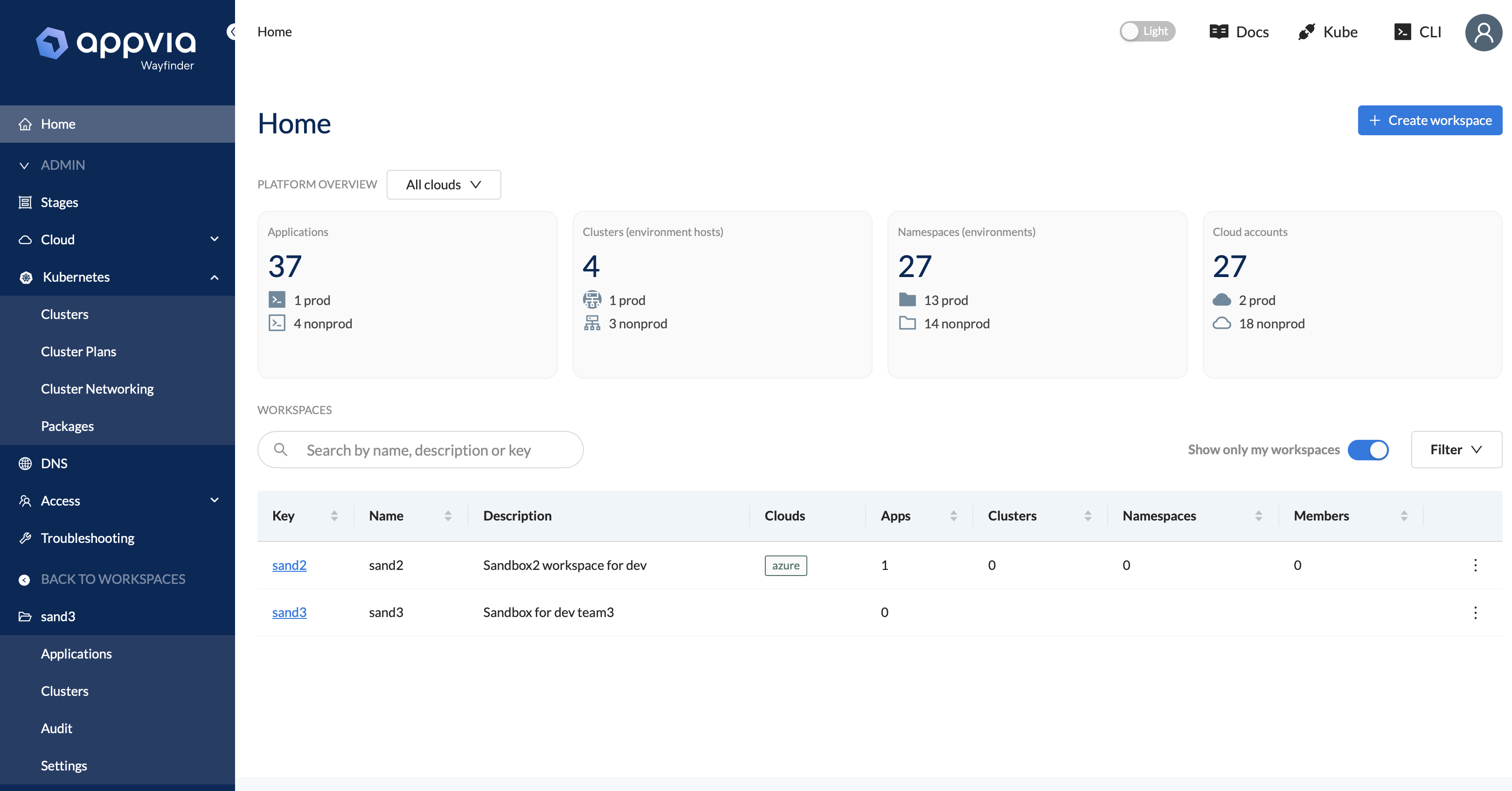
Other enhancements and new features
- [WF-3838] ✨ Support for 'user defined routing' outbound type on Azure AKS clusters
- [WF-3929] ✨ Add estimated cost for control plane cost for Azure 'paid' SKU clusters
- [WF-3855 / WF-3856] ✨ Provide a set of environment variables to deployed apps describing the runtime environment provided by Wayfinder
- [WF-3890] ✨ Allow AppEnvs to specify a reference to a CloudAccessConfig (needed where more than one cloud access configuration is provided to a workspace for a given stage)
- [WF-3540] ✨ Narrow the permissions required for GCP roles
- [WF-3947] ✨ Remove support for legacy auth proxy (this was replaced by our new kube proxy component in v2.4)
- [WF-3896] ✨ Add validation to Peering resources if directly applied
- [WF-3970] ✨ Improve validation of cloudaccessconfig types
Bug Fixes
- [WF-3943] 🐛 UI - Show dependency errors consistently on delete
- [WF-3945] 🐛 Ensure app components are successfully deleted if their owning app is deleted
- [WF-3949] 🐛 Ensure workspace owners can delete their own workspaces
Release v2.4.6
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.4.6/wayfinder.sha256sums
Enhancements / New features
- [WF-3792] ✨ CLI - Add
wf logscommand to follow and view Wayfinder logs - [WF-3969] ✨ UI - Remove the downloaded wf.tgz in the CLI download tip
- [WF-3944] ✨ Restrict cloud access configuration in workspaces to Wayfinder admins
Bug Fixes
- [WF-3990] 🐛 Fix AKS node pool OS type handling
- [WF-3977] 🐛 UI - Fix incorrect cluster in access cluster modal
- [WF-3968] 🐛 UI - Show correct value for number of clusters using a clusternetworkplan
- [WF-3950] 🐛 Allow non-admins to perform cost estimates and retrieve metadata for building clusters
- [WF-3926] 🐛 Enforce correctly against deployments when preventing use of cert-manager labels
Release v2.4.5
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.4.5/wayfinder.sha256sums
Enhancements / New features
- [WF-3928] ✨ Update terranetes (to v0.7.5) to support Azure Workload Identity auth
- [WF-3926] ✨ Add default policy to allow cert-manager to perform HTTP01 challenges
- [WF-3888] ✨ Add Azure AKS services network range to cluster spec
- We recommend updating your existing AKS cluster plans to specify a fixed range to use to assign Kubernetes service IP addresses from.
- It is safe to use the same range on all your clusters, thus specifying an allocated IP range of type 'Services' is now deprecated on Azure and will be removed in a future release.
- [WF-3925] ✨ Stop reserving half of the allocated IP range on AKS
- Previously, the subnet created for an AKS cluster was half the size of the allocated network, with the rest reserved for future use.
- This is no longer the case, so any new AKS clusters will use the whole allocated range for their subnet.
- This will not affect any existing clusters.
Bug Fixes
- 🐛 UI - Address "All" cluster list tab not showing resources on initial navigation
- [WF-3822 fixup] 🐛 Use workspace list API on users page, fixes invalid context error
Release v2.4.4
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.4.4/wayfinder.sha256sums
Enhancements / New features
- [WF-3915] ✨ Add support for configuring AWS Transit Gateway routing when peering
- [WF-3751] ✨ Add PeeringAcceptor permission to cloud access configuration for all clouds
- [WF-3882] ✨ Ensure cached kubeproxy connections are expired before they time out (prevents occasional 401 errors accessing clusters)
- [WF-3921] ✨ CLI - Make CLI HTTP client timeout overridable via
WAYFINDER_HTTP_CLIENT_TIMEOUTenvironment variable (set to e.g. 30s)
Bug Fixes
- [WF-3895] 🐛 Correct handling of 'Not Found' errors in Azure peering provider
- [WF-3920] 🐛 CLI - Handle resources with a 'nil' common status in
wf apply --wait-for-ready - [WF-3803] 🐛 Fix over-zealous validation for overlapping peering address ranges
- [WF-3822] 🐌 Improve performance of workspace overview APIs used by the UI
Release v2.4.3
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.4.3/wayfinder.sha256sums
Cross-cloud Web Identity support
- With credential-free access to AWS, Azure and GCP, you can now use Wayfinder's web identity to authenticate Wayfinder into your entire cloud estate, regardless of the cloud in which Wayfinder is hosted (installed)
- Benefits of credential-free access:
- When hosted in AWS use an AWS IAM role for Service Account (IRSA) identity to give Wayfinder access to AWS accounts, Azure subscriptions and GCP projects
- When hosted in Azure use Entra (formerly Azure AD) Workload Identity to give Wayfinder access to Azure subscriptions, AWS accounts and GCP projects
- When hosted in GCP use GCP Workload Identity to give Wayfinder access to GCP projects, AWS accounts and Azure subscriptions
- Reference public Terraform modules to install Wayfinder with the above identities configured on each cloud (AWS, Azure, GCP)
- Reference public Terraform modules to provision the required access for Wayfinder to each AWS account, Azure subscription or GCP project
- Complete overhaul of UI to guide and validate the configuration of cloud access and generate the YAML for your CI process
- New, simplified version of the CloudIdentity and CloudAccessConfig resources to make the configuration clearer and more readable
Includes the following new features and improvements:
- [WF-3552] ✨ Add CloudAccessCheck resource to perform a validation flow for cloud identities and permissions
- [WF-3685] ✨ Validate AWS permissions using SimulatePolicyPrincipal API
- [WF-3687] ✨ Validate Azure permissions by parsing applied policies
- [WF-3826] ✨ List missing permissions when permission checks fail on all three clouds
- [WF-3901] ✨ Ignore AWS organisation 'Service Control Policy' permission failures when assessing role validity on AWS
- [WF-3769] ✨ Auto-cleanup of old CloudAccessCheck resources once the check is complete
- Remove dependency on specific naming convetions for:
- [WF-3783] ✨ CloudAccessConfig resource names
- [WF-2491] ✨ CloudAccessConfig permission AWS role names
- ✨ CloudIdentity resource names
- [WF-3840] ✨ Improved validation of all cloud access properties
- [WF-3834] ✨ Don't block reconciliation of clusters, networks, DNS zones if cloud access permissions out of date, only if inaccessible
- [WF-3737] ✨ Add cloud permissions API
- [WF-3724] ✨ CLI - Add
wf describe cloudpermission
- [WF-3724] ✨ CLI - Add
- ✨ Provide reference cloud access Terraform modules that can set up the required access for Wayfinder in your AWS/GCP/Azure accounts:
- [WF-3714] ✨ Terraform to set up cloudaccess on AWS
- [WF-3715] ✨ Terraform to set up cloudaccess on Azure
- [WF-3716] ✨ Terraform to set up cloudaccess on GCP
- [WF-3828, WF-3832] ✨ Add API to produce values to use for cloud access Terraform inputs
- [WF-3818] ✨ UI - Display terraform inputs when preparing or amending cloud access configuration
- ✨ CLI - Add
wf describe cloudaccesscommand to describe the required inputs for cloud access Terraform, with-o tfvarsto output directly for use with Terraform
- [WF-3746] ✨ CLI - Implement improved
wf create cloudidentityandwf create cloudaccessconfigcommands- ✨ CLI - Add
--for-workload-identityflag towf create cloudidentityto create a cloud identity for the workload identity provided to Wayfinder at install
- ✨ CLI - Add
- Migrate from deprecated Azure AD Pod Identity to supported Entra (formerly Azure AD) Workload Identity:
- [WF-3659] ✨ Migrate AKS cluster provider to use new Azure SDK with Azure AD Workload Identity support
- [WF-3703] ✨ Migrate Azure authentication to use new Azure SDK with Azure AD Workload Identity support
- [WF-3662] ✨ Migrate Azure DNS provider to use new Azure SDK with Azure AD Workload Identity support
- [WF-3663] ✨ Migrate WorkloadIdentity controller to provision Entra / Azure AD Workload Identities instead of AzureAD Pod Identities
- ✨ Migrate Azure network provider to use the new Azure SDK
- [WF-3664] ✨ Remove AAD Pod Identity package from default packages and install
- [WF-3674] Removed cloud organisation / cloud account factory support
- [WF-3550] Removed
wf setup cloudaccessconfigandwf setup cloudidentitycommands (replaced by the reference Terraform modules andwf create cloudaccesscconfig/wf create cloudidentity)
New Kubernetes API proxy for managed clusters
- Provides a consistent API to access clusters managed by Wayfinder without needing direct network connectivity
- Allows full access to API of managed clusters via UI, subject to your configured access policies:
- UI now uses same RBAC as
wf access cluster- request access to clusters as you need them right from UI, subject to the same policies that govern all cluster access - Much improved pod log support with dynamic filtering and following
- Shell support to exec into pods for debugging, provided user has an access policy permitting this
- UI now uses same RBAC as
- [WF-3721] ✨ Full TLS verification when accessing clusters via
kubectl - Removes need for an authentication load balancer for each cluster, reducing cluster costs
- Provides same IP address filtering as existing auth proxy
- As all access is made via Wayfinder's API, cluster access is audited as per all other Wayfinder operations
- Existing auth proxy deprecated and disabled by default in new installs, support for it for existing installs will be removed in an upcoming release
New troubleshooting section
- Provides access to Wayfinder's own controller, API, kube proxy and webhook logs from UI
- Tail and filter logs to debug isuses with your configuration
Improvements and other new features
- [WF-3901] ✨ Ignore regions which are denied by AWS service control policies in metadata
- ✨ Add Azure DevOps-compatible WF toolbox image - quay.io/appvia-wayfinder/wftoolboxazdo:v2.4.3
- [WF-3869] ✨ Allow additional node pools to be specified with zero minimum size
- [WF-3881] ✨ Support --ca-file on
wf login, improve API client logging when used with--verbose - [WF-3848] UI - Show message when no IP ranges exist in network range table
- ✨ Remove persistence of asset identifiers into database (was no longer used/required)
- [WF-3719] ✨ Support Azure AKS node image security update option
- [WF-3284] ✨ Remove unused windowduration property from cluster plan
- [WF-3749] ✨ Show clusters using a given ClusterNetworkPlan in UI
- [WF-3427] ✨ Allow binding of the same role multiple times to an access token, introduce new assume/assign/kubesessions subresources for consistent web interface and CLI behaviour
- ✨ CLI - Use new 'assume' subresource in
wf access cluster - [WF-3793] ✨ Helm chart improvements:
- Option to generate a single cert
- Add default CA if secret not provided
- Remove some unused options
- [WF-3720] ✨ Allow local logins to be completely disabled
- [WF-2912, WF-2891] ✨ Use secure, HTTPS-only cookies instead of bearer tokens for UI authentication - allows opening new tabs without re-authenticating and improves security
- [WF-3717] ✨ Respect upstream IDP refresh tokens if provided - ensures users removed from IDP are blocked as soon as their upstream token indicates expiry
- ✨ Replace hard-coded default deny network policy with kyverno policy doing the same
Bug Fixes
- [WF-3904] 🐛 Ensure we only trigger reconciliation of cloudmeta when relevant condition of cloud access changes, not on any update
- [WF-3612] 🐛 Validate name of environment variables on app components are populated
- [WF-3493] 🐛 Fix issue handling empty Linux/Windows profile on AKS cluster build (prevented copying default AKS cluster plans)
- 🐛 Prevent package releases showing 'Success' when required DNS zone dependencies are unmet
- [WF-3734] 🐛 Ensure cluster exists before pre-cluster deletion logic
- [WF-3642] 🐛 Cannot edit ClusterPlan if ClusterNetworkPlan disabled
- [WF-3892] 🐛 CLI - Fix
wf create memberfor usernames containing '@' characters - [WF-2560] 🐛 CLI - Set namespace correctly when using
wf access namespace - 🐛 CLI - Don't refresh tokens if there's no refresh tokens (prevents edge case where lack of refresh token blocks CLI indefinitely)
- [WF-3564] 🐛 UI - Highlight validation error by navigating to correct pane or scrolling to issue
- [WF-3680] 🐛 UI - Fix app component list occasionally showing components from other app
Release v2.3.3
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.3.3/wayfinder.sha256sums
Enhancements / New features
- [WF-3690] ✨ Add namespaceType label to all namespaces managed by Wayfinder in child clusters
Bug Fixes
- [WF-3691] 🐛 Fix EKS KMS key alias deletion when alias not created
- [WF-3689] 🐛 Check if assignablenetwork spec has changed when checking for dependencies
Release v2.3.2
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.3.2/wayfinder.sha256sums
Bug Fixes
- [WF-3682] 🐛 Allow access token network manager roles to manage ClusterNetworks and ClusterNetworkPlans
Release v2.3.1
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.3.1/wayfinder.sha256sums
Notice
Wayfinder now includes a cluster's network configuration within the cluster plan's setup. This streamlines the creation and definition of cluster plans while providing greater transparency regarding the anticipated cluster network assignments when utilising a specific cluster plan. Please be aware that this modification introduces breaking changes, as detailed in the sections below.
Breaking changes
- NetworkFabricPlan renamed to ClusterNetworkPlan - update your CI definitions, existing ones will be migrated.
- NetworkFabric renamed to ClusterNetwork
- AssignableNetwork 'Stages' property deprecated in favour of a single 'Stage' - update your CI definitions, existing ones will be migrated.
Action required
-
If you have any existing NetworkFabricPlan resources stored in a repository, you must migrate those to use the new API type. To do this:
- Change the kind from NetworkFabricPlan to ClusterNetworkPlan
- Remove any 'spec.allocation' - cluster network plans are now implicitly available via the allocation of cluster plans.
- If using assignable networks, specify which assignable networks to use by populating spec.assignableNetworks (previously this implicitly used all configured ranges)
- Post upgrade, ensure that you update Wayfinder CLI to v2.3.1 locally and in CI
-
To use EKS secrets encryption, the following additional IAM permissions are required for Wayfinder's ClusterManager role to manage KMS keys for EKS:
- kms:CreateKey
- kms:ScheduleKeyDeletion
- kms:TagResource
- kms:CreateAlias
- kms:DeleteAlias
- kms:UpdateAlias
- kms:ListKeys
- kms:ListAliases
- kms:DescribeKey
- kms:ListResourceTags
Alterations to existing CLI behaviour
wf apply --diffno longer supported. Usewf diffcommand instead.- If differences are found with
wf diffcommand, then it will now exit with 0, unless you run it with--fail-on-diffflag.
Cluster networking (Bug Fixes / New Features)
- [WF-3250] ✨ Rename NetworkFabric and NetworkFabricPlan to ClusterNetwork and ClusterNetworkPlan in API
- [WF-3250] ✨ Deprecate 'Stages' on an AssignableNetwork, only support a single 'Stage' (existing AssignableNetworks will be migrated)
- [WF-3524] ✨ Migrate existing NetworkFabrics and NetworkFabricPlans to ClusterNetworks and ClusterNetworkPlans
- [WF-3397] ✨ Add NetworkAllocations and status to ClusterNetworkPlan API object
- [WF-3411] ✨ Remove allocations from ClusterNetworkPlan spec
- [WF-3410] ✨ Improve Assignable Network validation
- [WF-3414] ✨ Check for collisions when creating assignable networks
- 🐛 Fix incorrect validation error index on overlapping assignable network ranges
- [WF-3383, WF-3418, WF-3419] ✨ Provide networking details, capacity information and validation on the status of ClusterNetworkPlans
- ✨ Make cluster network plan controller less stateful and more deterministic
- [WF-3416] ✨ Validate ClusterNetworkPlans for assigned ranges and fixed IPs
- [WF-3412, WF-3415] ✨ Validate that network ranges removed from plans are not in use
- [WF-3580] 🐛 Perform network ranges size validation per provider and range type
- [WF-3581] ✨ Correct array notation on invalid CIDR block size validation message
- [WF-3582] 🐛 Don't continue with range validation if invalid CIDRs are specified
- [WF-3567] ✨ Block deletion of ClusterNetworkPlan if cluster networks referencing it exist
- [WF-3383] ✨ Add API endpoint to describe a network from a proposed spec
- [WF-3621] ✨ Don't allow a cluster network plan to be deleted if cluster networks reference it
- [WF-3421, WF-3467] ✨ Use only the AssignableNetworks specified on a ClusterNetworkPlan when allocating IPs to new networks
- [WF-3660] ✨ Remove default assignable networks and make default plans editable (our default plans will no longer be provided in v2.4, in favour of example plans)
- [WF-3608] ✨ UI - Tweaks to cluster network table
- [WF-3611] ✨ UI - conditionally display network details
- ✨ UI - Update cluster network plan view mode from old style
- [WF-3577] ✨ UI - Cluster networking - remove VPC & subnets radio + copy change
- [WF-3381] ✨ UI - Add cluster network list to cluster networking page
- [WF-3578] 🐛 UI - Fix for incorrect error message toast displaying when saving a cluster plan
- [WF-3210] ✨ UI - show network description when creating a ClusterNetworkPlan
- [WF-3572] 🐛 UI - Show service field for azure on assignable network form
- [WF-3576] ✨ UI - After adding a new cluster network plan, make it the selected one by default
- [WF-3579] 🐛 UI - Fix breadcrumb on cluster network plan page
- [WF-3565] ✨ UI - Move IP address ranges (and the management of) to updated Cluster networking page
- [WF-3538] ✨ UI - Update cluster networking page to use update cluster network plan form
- [WF-3517] ✨ UI - Implement cluster network plan form (via cluster plan)
- [WF-3210] ✨ UI - Implement updated networking tab on cluster plan form
- [WF-3522] 🐛 UI - Update Network assignments page to use stage property (rather than stages)
EKS Encryption (New Feature)
EKS clusters now support enabling AWS's EKS secrets encryption. This can be enabled in cluster settings and cluster plans for EKS. Enabling it will cause a new KMS key to be created for a new cluster, and that cluster configured to use it for envelope encryption of Kubernetes secrets. This can only be enabled on new clusters at this time.
- [WF-3503] ✨ Implement optional secrets envelope encryption for EKS
- [WF-3502] ✨ Add API support for EKS secrets encryption
- [WF-3508] ✨ Validate EKS encryption settings as immutable
- [WF-3504] ✨ UI - Add configuration of EKS encryption
- [WF-3505, WF-3507] ✨ Populate EKS encryption status and show on UI
- [WF-3506] ✨ Turn on EKS secrets encryption by default in the eks-hardened plan
Misc (Bug Fixes / New Features)
- [WF-3463] ✨ Validate stage deletion - block if cloud access configs, global DNS zones or clusters exist in the stage
- [WF-3596] ✨ Update auth proxy HorizontalPodAutoscaler to API version v2 (required for K8S v1.26)
- [WF-3598] ✨ Allow --force to override delete dependency checks
- [WF-3599] ✨ Add 'localadmin' user management to helm chart values
- [WF-3568] 🐛 Fix workspace occasionally going to 'Success' status before all elements are ready
- [WF-3485] 🐛 Use high (but not system) priority level for Kyverno package (allows install on GCP)
- [WF-3494] 🐛 Reconcile app DNS zones when the status of a global DNS zone changes (addresses race condition causing delayed DNS configuration where global DNS zone added and applications already exist)
- [WF-3571] 🐛 Ensure 'create' API operations cannot overwrite existing resources
- [WF-3566] 🐛 Fix regression in GCP service account handling for Workload Identity
- [WF-3147] 🐛 Update the ingress-nginx package to apply the correct flags
- ✨ UI - Display dependency errors on deletion
- ✨ UI - Attempt to display underlying error messages from API where structured error handling fails
- [WF-3280] 🐛 / ✨ UI - Hide delete action when resource is already deleting
- [WF-3518] 🐛 UI - Fix error deleting cluster created from app env which no longer exists
- [WF-3633] 🐛 UI - Fix error creating a new, blank GKE cluster plan
- [WF-3498] ✨ CLI - Remove
wf apply --diffoption (usewf diffinstead) - [WF-3499] ✨ CLI - Make
wf diffexit 0 if differences found unless run with--fail-on-diff - [WF-3535] 🐛 CLI - Validate workspace/name on get cloudaccessconfigdependents
- [WF-3495] 🐛 CLI - Make deploy
--wait-for-readyonly wait for the components being deployed - [WF-3516] 🐛 CLI - Correct ClusterNetworkPlan and KubernetesUpdate CLI resource types
- [WF-3279] 🐛 CLI - Improve error message for
wf deletewith a non-existent object - [WF-3466] 🐛 CLI - Add missing
--force,--owner,--dry-runand--no-waitflags towf delete clustercommand
Release v2.2.1
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.2.1/wayfinder.sha256sums
Enhancements / New features
- [WF-3405] ✨ Verify referenced container secrets and component image pull secrets are present when using
wf deploy - [WF-3511] ✨ Update wftoolbox docker image - add 'bash', update kubectl to v1.25.12 and kustomise to v5.1.1
Bug Fixes
- [WF-3516] 🐛 Correct client-side validation of NetworkFabricPlan and KubernetesUpdate resources with
wf apply - [WF-3501] 🐛 CLI - Correct name column and add username column for
wf get users - [WF-3520] 🐛 CLI - Support
--planinwf create appcomponent - [WF-3514] 🐛 UI - Allow editing of quota limits for multi-tenant namespaces
- [WF-3519] 🐛 UI - show the replicas value correctly on existing application components
Release v2.2.0
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.2.0/wayfinder.sha256sums
-
The 'components' field of the Application CRD has been deprecated in favour of a dedicated new AppComponent resource. All existing Applications will be migrated on upgrade with AppComponents created automatically. If you are managing your Applications from an external source via
wf apply, you should update these definitions. -
Kubernetes v1.24 has reached the end of its support window, so in Wayfinder v2.2 new clusters must use (at minimum) v1.25. Please review any existing cluster plans which specify v1.24 and update to v1.25 or later before upgrading.
Application Component enhancements
With this release, we have enhanced the configurability of application components to allow many more use cases to be served. Retaining the simplicity of the defaults, you can optionally now provide more advanced configuration:
- Specify multiple containers
- Specify specific user and group IDs to execute as
- Provide environment variables and image pull secrets from existing secrets
- Override entry point and arguments for the containers
- Specify multiple ports to expose on a service, and choose which one to expose externally
- Specify custom labels to be applied to all deployed resources
Underlying this change, we have introduced a new AppComponent resource. The container definition uses the same fields and values as Kubernetes' own container definition, meaning if you graduate to managing your own manifests, the definition should be immediately familiar.
Enhancements / New features
- [WF-3271 / WF-3202] ✨ Add dedicated resource for AppComponent and migrate components from existing Applications
- [WF-3392] ✨ Update Kyverno scheduling priority to avoid risk of it being pre-empted in a cluster
- [WF-3058] ✨ CLI - Add delete confirmation for clusters, namespaces and applications with components
- [WF-2507] ✨ CLI - Enhance
wf help getandwf help deleteto list all resource types - [WF-3056] ✨ CLI - Validate field keys in
wf applyso it errors if unknown/invalid fields are included in an applied file - [WF-3017] ✨ CLI - Make
wf create user --dry-runconsistent with other create commands - [WF-3015] ✨ CLI - Make
wf create namespace --dry-runconsistent with other create commands - [WF-3238] ✨ UI - Show warning prompt when attempting to delete a global DNS zone
- [WF-3292] ✨ UI - Update admin side menu so plans are all in one place
- [WF-3257] ✨ UI - Give a useful error message when trying to enable/disable plans
- [WF-3205] ✨ UI - Update cluster plan form to use vertical tabs for sections
Bug Fixes
- [WF-3386] 🐛 Wait 5 minutes for packages in deleting clusters to be deleted, then continue with cluster deletion
- [WF-3212] 🐛 Use correct release name when removing helm release from the cluster
- [WF-3138] 🐛 Fix DNS zone tags
- [WF-3236] 🐛 Ensure cluster status correctly reflects cluster updates
- [WF-3293] 🐛 CLI - Fix no
--outputflag causing validate error onwf create namespace - [WF-3232] 🐛 CLI - Set export and eject directory and file perms
- [WF-3171] 🐛 UI - Make Package / Cluster update button clearer, don't show on superceded updates
- [WF-3363] 🐛 UI - Fix channel/version issue when saving a copied cluster plan
- [WF-3240] 🐛 UI - Cluster deletion message shows
undefined - [WF-3367] 🐛 UI - Make Workspace table text visible in dark mode if not a member of any workspaces
- [WF-3364] 🐛 UI - Ensure CIDR length is a number before posting
- [WF-3197] 🐛 UI - Make sure admins can access users page of workspaces they don't own
Release v2.1.2
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.1.2/wayfinder.sha256sums
Enhancements / New features
- [WF-3196] ✨ Implement app DNS for app-envs on multi-tenant clusters
Bug fixes
- [WF-3230] 🐛 Allow creation of an app if you have a multi-tenant cluster shared with your workspace, even if no cloud access configured
- [WF-3226] 🐛 Mutate on an empty values object when no package values supplied by user
- [WF-3219] 🐛 Allow Wayfinder itself to make changes to clusters when a plan-policy prevents users from making those changes, allowing it to manage versions
- [WF-3200] 🐛 UI - Make labels editable/uneditable correctly on cluster plan/settings form
- [WF-3186] 🐛 UI - Allow user to navigate directly to a namespace resource tab
- [WF-3215] 🐛 Create and manage package updates respecting the package selectors, clear defunct updates on package delete, and fix CLI cluster column on package updates
- [WF-3187] 🐛 Correctly remove detargeted clusters and namespaces when updating global cluster policies
- [WF-3199] 🐛 UI - Remove erroneous uniqueness validation on workspace key when updating a workspace
- [WF-3170] 🐛 CLI - Don’t update object if unchanged in
wf edit - [WF-3172] 🐛 Fix for custom package Repositories
- [WF-2862] 🐛 CLI - Allow cascading deletion of Global DNS Zones
Release v2.1.1
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.1.1/wayfinder.sha256sums
With this release, we have aligned the 'version' property of clusters and cluster plans with the values supported natively by the cloud providers. On AWS, this means that the version property must now be set to a Kubernetes major.minor (such as 1.24), as EKS does not support setting a full patch version (such as 1.24.11).
Any existing AWS EKS clusters will have their spec automatically migrated to the correct major.minor after Wayfinder is upgraded (this will not cause any changes to the cluster in AWS).
Any custom EKS cluster plans which specify a version must be updated to the desired major.minor version after Wayfinder is upgraded. If this action is not completed, the plan will not be usable for new clusters.
Support for Kubernetes v1.25
Wayfinder 2.1 introduces support for Kubernetes v1.25 on all three cloud providers.
- [WF-3133] ✨ Update default Kubernetes version on all three clouds to v1.25 for new clusters
- [WF-3191] ✨ Align Kubernetes version handling with the cloud-provider supported syntax for all three clouds:
- AWS: Only major.minor (e.g. 1.25) now supported - previously the patch version was allowed to be specified, but would be ignored
- Any existing clusters which specify a full version on their spec will be migrated to major.minor.
- See action required above - any existing cluster plans which specify major.minor.patch (e.g. 1.25.1) must be updated to a major.minor (e.g. 1.25) after upgrading to v2.1.
- Azure: Only major.minor.patch (e.g. 1.25.1) supported (no change)
- GCP: major.minor (e.g. 1.25), major.minor.patch (e.g. 1.25.1), and major.minor.patch-gkepatch (e.g. 1.25.1-gke.1500) supported
- Cluster plans and clusters are now validated against these syntaxes and against supported versions
- AWS: Only major.minor (e.g. 1.25) now supported - previously the patch version was allowed to be specified, but would be ignored
- [WF-2843, WF-2771] ✨ Update dependencies to support K8S v1.25:
- Cert Manager (v1.9.1 to v1.12.0)
- External DNS (v6.2.4 to v6.20.3)
- Ingress-NGINX (v4.2.0 to v4.6.1)
- Kyverno (v2.6.5 to v2.7.3)
- Terranetes Controller (v0.4.2 to v0.6.8 - including setting MSI details when deploying on Azure)
- Amazon EKS: Tigera Operator (v3.23.2 to v3.25.1)
- Amazon EKS: Metrics Server (v3.8.2 to v3.10.0)
- Amazon EKS: Cluster Autoscaler (v9.21.0 to v9.29.0)
- Amazon EKS: EBS CSI Driver (v2.18.0 to v2.19.0)
- Azure AKS: AAD Pod Identity (v4.1.12 to v4.1.17)
Enhancements / New features
- [WF-3069] ✨ Add
wf diffcommand, align behaviour with kubectl diff - [WF-2946] ✨ Add EKS image field to node pool, allowing selection of any supported EKS image type
- [WF-2921] ✨ Reduce scope of AWS security group ports for private clusters to the minimum required
- [WF-3145] ✨ Show package release in action required, rather than pending, state if cluster in error state
- [WF-3073] ✨ Remove overbearing client-side finalizer validation from
wf apply(allowswf get -o yamlto be piped towf apply -f -) - [WF-2825] ✨ Ensure updates to container registry secrets are distributed when the secret itself is updated
- [WF-3080] ✨ Add more useful messages to package validation indicating how to set version correctly
- [WF-3090] ✨ Improve
wf exportto only export configmaps and secrets for workspace namespaces - [WF-3081] ✨ Exclude AuditEvents from
wf export(these are not resources so cannot be exported in this manner) - [WF-3037] ✨ Improve headers for
wf get nodepooloutput - [WF-2635] ✨ Display multiple server-side errors nicely in a single toast
- [WF-3190] ✨ Add requests for Wayfinder resources to the helm chart
- [WF-3048, WF-3049] ✨ Add support for reconciliation pausing, add pause/resume reconciliation CLI commands
App, component and app environment improvements:
- [WF-3030] ✨ Add available ingress classes to appenv status and use in manifest generation
- This allows custom ingress controller deployments to be detected and used when generating manifests for app components
- [WF-2982] ✨ Improve example deploy commands in "How to deploy" modal
- [WF-2557, WF-2672] ✨ Block cluster deletion if there are existing appenvs, unless delete cascaded
- This prevents appenvs causing clusters to be re-created after deletion
- [WF-3074, WF-2908] ✨ Improve
wf deploy/wf deploy componenthelp text
Bug fixes
- [WF-3071] 🐛 Ensure Node Pool updates are only generated for immutable changes to the node pool definition
- This unblocks making non-immutable changes to node pools, which could become stuck previously
- [WF-3079] 🐛 Correct generated secret name for helm releases that use custom secrets
- [WF-2893] 🐛 Remove owner (if applicable) when a member is removed from workspace
- [WF-2893] 🐛 Fix various quirks with workspace users page
- [WF-3094] 🐛 Ensure cluster plan labels are saved correctly
- [WF-2999] 🐛 Clean up form errors (duplicate toasts etc.)
- [WF-3067] 🐛 Fix application component key validation/generation with max-length keys
- [WF-3063] 🐛 Use appenv metadata.name when looking up the env - addresses not being able to deploy to an env if it had the same name as the app
- [WF-2937] 🐛 Show access rather than deploy command for components of type OwnManifest
- [WF-2931] 🐛 Fix deploy --eject for apps with ownmanifests components
- [WF-3036] 🐛 Fix app list empty row in dark mode
- [WF-2671] 🐛 Improve default input variable handling on cloud resource plans
- [WF-3077] 🐛 Ensure empty-both-sides pass plan validation on cloud resource component updates in apps
- [WF-3107] 🐛 Support valuesFrom prefix and suffix on all package values and perform deep JSON merges on the values to allow configuration of complex structures
- [WF-3125] 🐛 Add permissions allowing Azure clusters to use internal load balancers
- [WF-3211] 🐛 Ensure app environments don't block deletion of clusters on cluster expiry
- [WF-2751] 🐛 / ✨ Ensure defaults passed to CloudResourcePlan on creation
Release v2.0.5
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.0.5/wayfinder.sha256sums
Enhancements / New features
- [WF-3020] ✨ Make --dry-run on wf create workspace consistent with other commands
- [WF-2772] ✨ Remove superseded un-applied package updates when newer updates are generated
- [WF-2434] ✨ Add Application/Cloud Resource Plan policy validation
- [WF-2844] ✨ Improve generic error handling across UI
- [WF-2996] ✨ Allow admins to use
wf exportto export secret data for backup purposes - [WF-2892] ✨ Ensure disabled/deleted users are immediately blocked
- [WF-2949] ✨ Add --diff flag to wf apply to show changes that will be applied
- ✨ Improve description of network plan AWS specific fields
Bug fixes
- [WF-3042] 🐛 Ensure deleted namespace claims are reconciled by container registry controller
- [WF-2968] 🐛 Ensure cluster list is using unique key + tests
- [WF-2939] 🐛 Ensure quotes in environment variables are handled correctly when generating app manifests
- [WF-2966] 🐛 Ensure node pool fields are editable when editing from cluster plan / creating a cluster
- [WF-2964] 🐛 Allow creation of clusters without a channel and validate channels are valid when specified
- [WF-3004] 🐛 Ensure underlying namespace is deleted cleanly before removing namespace claim, and show meaningful error when the deletion is blocked
- [WF-3007] 🐛 Fix specifying multiple node pool instances types in EKS
- [WF-2989] 🐛 UI - Fix navigation into workspaces as admin when not a member of any workspaces
- [WF-2993/2952] 🐛 Cluster page package list errors when the cluster has no channel
Release v2.0.4
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.0.4/wayfinder.sha256sums
Bug fixes
[WF-2988] 🐛 Fix nodepool panic if cluster deleted rapidly after creation
Release v2.0.3
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.0.3/wayfinder.sha256sums
In this release, we have introduced separate packages for public and private ingress which target different labels. In order to ensure existing clusters keep their public ingress,
before upgrading, edit any existing clusters that you wish to keep public ingress controller in and add the label appvia.io/ingresspublic: "true". This is added by default in our
standard plans so any new clusters will have that by default. If you have any custom plans, ensure those have the label added as follow:
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
spec:
template:
clusterLabels:
appvia.io/ingresspublic: "true"
You can enable private/internal ingress in a similar manner in a plan or on a cluster with the label appvia.io/ingressinternal: "true"
New features
- [WF-2905] ✨ Use metadata.name for application name in side nav and application list
- [WF-2866] ✨ Add internal ingress controller for private clusters
- [WF-2762] ✨ Use availability zones to set subnets and NAT gateways (AWS)
- [WF-2797] ✨ Show the user that something is happening when they decide to delete their application
- [WF-2819] ✨ Do not create cloud access configurations as part of install
- [WF-2735] ✨ Add owner flag to delete and edit commands
- [WF-2851] ✨ Show Wayfinder instance identifier with wf serverinfo
- [WF-2717] ✨ Only show enabled clouds on cloud access screen
- [WF-2828] ✨ Ignore unparseable files and don't get secrets in wf apply
- [WF-2827] ✨ Implement 'wf dump' command to output Wayfinder configuration to disk
- [WF-2796] ✨ Hide internal implicit groups
- [WF-2279] ✨ Add UI for network plans
- [WF-2791] ✨ Use user's group memberships in UI to display/hide sections
- [WF-2812] ✨ Add region label to network fabric
- [WF-2812] ✨ Add region label to Cluster
- [WF-2756] ✨ Cluster plan UI - make network fabric plan configurable
- [WF-2779] ✨ Make wf apply --dry-run consistent with kubectl apply --dry-run
- [WF-2760] ✨ Add fields for network understanding
- [WF-2764] ✨ Upgrade flux helm machinery, and make configurable
- [WF-2577] ✨ Add wf follow command to watch resources to success/completion
- [WF-2753] ✨ Show more useful details for own-manifest components
- [WF-2632] ✨ Improve messaging when trying to create an application with no clouds enabled
- [WF-2615] ✨ Allow app environments to be re-ordered (UI)
- [WF-2701] ✨ Implement initial deployment dashboard
- [WF-2594] ✨ Improve copy in cloud identity UI
- [WF-2829] ✨ Add network policies for component-to-component dependencies in generated app manifests
- [WF-2954] ✨ Freeze opinion-default packages and cluster policies if updated
- [WF-2660] ✨ Implement whitelist annotation to ingress in generated app manifests
- [WF-2521] ✨ Add validation for whitelist field on component form
- [WF-2874] ✨ Strip dashes from AWS account ID on cloud configuration UI
- [WF-2929] ✨ UI: remove strange transition on TLS/expose switches in app
- [WF-2944] ✨ Don't block cloud access if role hash is out of date
- [WF-2899] ✨ Add availability zone ID support to AWS VPCs / network plans
- [WF-2733] ✨ UI - Move networking stuff into developer self service menu
- [WF-2718/WF-1603] ✨ Validate cluster versions against what we support
- [WF-2637/WF-2763/WF-2759] ✨ Improvements to networkfabrics and assignablenetworks
- [WF-2875/WF-2894/WF-2895] ✨ Support internal and external ingress on the same cluster
- ✨ Re-reconcile action required cloud access configs every 30s
- ✨ Enable container registy controller
Bug fixes
- [WF-2896] 🐛 Dark mode obscures workspace selection
- [WF-2879] 🐛 Fix merge order for cluster/network plan to spec, preventing plan overriding cluster spec
- [WF-2901] 🐛 Cluster Creation, Cloudwatch logs not labelled correctly
- [WF-2903] 🐛 Corrected small and large QuotaLimits for all EKS plans
- [WF-2880] 🐛 Remove mask columns from UI (no longer on the spec)
- [WF-2846] 🐛 Validate disabled network plans
- [WF-2741] 🐛 Some routes break the back button (UI)
- [WF-2719] 🐛 Correct user and admin counts in platform setup
- [WF-2827] 🐛 UI doesn't handle nil value of TLS field in container component
- [WF-2766] 🐛 Fix for users not showing in user search filter on audit page
- [WF-2857] 🐛 Don't expose disabled network fabric plans to the cluster plan form
- [WF-2863] 🐛 Add missing validation for workspace key
- [WF-2742] 🐛 Remove old robot illustrations
- [WF-2861] 🐛 Helm versions like
3.0.0-alpha.2-1throw a validation error - [WF-2833] 🐛 Pods ready show undefined when ready replicas is nil
- [WF-2757] 🐛 Show error and message from status (not just from conditions) on Cluster status page
- [WF-2822] 🐛 Fix Cluster Plan enable and disable
- [WF-2727] 🐛 Correct prompt for create admin cloudaccessconfig
- [WF-2815] 🐛 Improve error messaging in the case of network fabric failures
- [WF-2785] 🐛 Don't error if AWS IAM policy in use when removing IAM roles
- [WF-2813] 🐛 Fix installer and AWS network validation
- [WF-2810] 🐛 Do not overwrite default assignable networks if updated by users
- [WF-2813] 🐛 Improve validation of network subnets for AWS
- [WF-2809] 🐛 Fix AWS Transit Gateway attachments
- [WF-2138] 🐛 Report on failed networks in cluster status
- [WF-2788] 🐛 Can't deploy app if image tag is a number
- [WF-2755] 🐛 Version unset when editing cluster plan
- [WF-2807] 🐛 Allow users with viewall or workspace viewer groups to see apps and enabled clouds in workspaces
- [WF-2783] 🐛 Show dependency deletion errors for workspace delete (UI)
- [WF-2734] 🐛 Ensure modals do not get overlapped by any other element
- [WF-2538] 🐛 Allow user to edit workspace once selected when creating a cluster
- [WF-2750] 🐛 Return an understandable error if the component doesn't exist on a deploy
- [WF-2740] 🐛 Ensure user can see what the current status of the Workspace is (e.g. if it's currently being deleted)
- [WF-2558] 🐛 Unable to add new owners to workspaces
- [WF-2782] 🐛 Ensure all non-success roles requeue the cloud access config
- [WF-2730] 🐛 Show correct name for node pools in CLI
- [WF-2745] 🐛 Fix viewing Users in access policies
- [WF-2754] 🐛 Allow setup cloudidentity to be re-run, improve error messages
- [WF-2725] 🐛 Improve validation in setup cloudaccess to prevent errors
- [WF-1609] 🐛 Improve retry logic in install flow to prevent retryable errors failing the install
- [WF-2728] 🐛 Correct stage on aws-prod assignable network
- [WF-2578] 🐛 Fix user count on Wayfinder groups page
- [WF-2681] 🐛 Omit applying org bindings when preparing GCP service accounts in setup identity/cloudaccessconfig unless required
- [WF-2703] 🐛 Correct cloudaccessmanager IAM role
- [WF-2468] 🐛 Display quota limit management tab correctly on cluster screens
- [WF-2945] 🐛 Unable to set machine type on new node pools
- [WF-2948] 🐛 Ensure node pools are deleted in cloud when removed from cluster spec
- [WF-2944] 🐛 Add describe keys permission to EKS cluster manager role
- [WF-2821] 🐛 Only users with correct access policies should see create access token button
- [WF-2956] 🐛 Node pool form - fix AMI config visibility in dark mode
- [WF-2907] 🐛 Heading colour fix in dark mode
- [WF-2942] 🐛 Fix/improve package updates
- [WF-2950] 🐛 UI - Ensure version mapping happens correctly on cluster update
- [WF-2832] 🐛
wf get appenvshould return the spec.name of the env not metadata.name - [WF-2878] 🐛 UI - TLS value should be based on both container expose and TLS values
- [WF-2978] 🐛 Fix role binding names for non-lower-case usernames
- [WF-2979] 🐛 Fix appenv de-referencing in wf deploy app
- [WF-2957] 🐛 UI - Workspace selector CSS fixes
- [WF-2535] 🐛 Delete accessrolebindings when associated accessrole is deleted
- [WF-2732/WF-2731] 🐛 UI - Add default network config and copying plan button
- [WF-2743/WF-2744] 🐛 Fix broken access policy links
- 🐛 Ensure deepcopys are performed correctly in cluster operators
- 🐛 Log as progress, not warning, when endpoint not ready in auth proxy (expected situation)
- 🐛 Allow workspace viewers to list members
- 🐛 Remove incorrect Network Fabric CLI resource column
- 🐛 Correct Peering Rule CLI columns
- 🐛 Fix AWS Network Manager role typo
Release v2.0.2
Downloads
See Get the CLI for instructions.
- CLI (Mac - AMD64): Binary | Compressed (.tar.gz)
- CLI (Mac - M1/M2): Binary | Compressed (.tar.gz)
- CLI (Linux): Binary | Compressed (.tar.gz)
- CLI (Windows): Binary | Compressed (.tar.gz)
- CLI Checksums: https://storage.googleapis.com/wayfinder-releases/v2.0.2/wayfinder.sha256sums