Cluster Plans
Cluster plans function as templates for self-serve clusters, serving as guardrails that enable Wayfinder administrators to customise available options and configurations for developers (as workspace members) to independently provision their environments.
As a Wayfinder administrator, you hold the authority to define the workspaces where each cluster plan will be accessible. These plans are presented as Environment Plans within the respective workspaces. Wayfinder automatically sets up a developer's environment based on the settings specified in the corresponding cluster plan.
Cluster plans have a wide range of properties that you can define, such as:
- Cluster plan information: Properties that help users in workspaces select the right plan for the cluster they're provisioning (such as a meaningful plan name, description and which workspaces they apply to).
- Cluster settings: Properties that apply at the cluster level (such as cluster labels, region, kubernetes version and cluster lifetime).
- Nodes: Properties related to cluster node pool configuration (such as auto-scaling, node pool sizes, approximate pool costs, image types, machine types, modes, spot instances, disk size, labels and taints).
- Upgrades: Properties that affect how clusters are auto-upgraded (such as auto-upgrade start time and duration)
- Multi-tenancy: Properties that define templates for namespace quota limits.
- Cluster networking: Properties that allow you to specify which cluster network settings Wayfinder should use when auto-creating clusters (such as using fixed CIDR ranges or auto-allocating IP subnetworks from pre-defined CIDR ranges.)
- Profiles (AKS only): Profile properties that specify administrative access and authentication (such as admin username and password, SSH public keys and SKU Tiers)
- Pod Security Standards: Properties that determine the type of policy to enforce (such as privileged, baseline and restricted)
- Estimated costs: A summary of expected cost of clusters provisioned using the cluster plan
CLI Quick Reference
| Instruction | CLI Command |
|---|---|
| List cluster plans | wf get clusterplan |
| View cluster plan's manifest | wf get clusterplan PLAN-NAME -o yaml |
| Output cluster plan's manifest to file | wf get clusterplan PLAN-NAME -o yaml > MYPLAN.yaml |
| Apply a cluster plan's manifest from file | wf apply -f MYPLAN.yaml |
| Create an environment by specifying the cluster and cluster plan | wf create appenv --app APP-NAME --env ENV-NAME --cluster CLUSTER-NAME --plan CLUSTER-PLAN-NAME --stage STAGE --region REGION |
Advantages of Cluster Plans
- Offering sensible default settings that align with best practices for both production and non-production environments.
- Establishing guardrails for workspace members' environment choices to ensure infrastructure compliance with your organisation's standards.
- Enabling policies to dictate whether workspace members can modify different cluster settings within the allocated plan(s).
Enhancing Cluster Security
We adhere to guidelines published by cloud providers to configure clusters:
- We eliminate any loosely defined permission bindings.
- We remove prior pod security policies (PSP), applying a baseline (PSS) Pod Security Standard to all applications as a reasonable least privileged (default) setting.
- We enforce a default network policy denial rule for all newly created namespaces, ensuring explicit traffic permission rather than a blanket allowance.
Utilising Cluster Plans
After setting up cluster plans, workspace members have the option to choose them for environment creation. Subsequently, they can deploy their applications into these environments.
You can find examples demonstrating how to create environments using cluster plans here.
Properties of Cluster Plans
The following sections outline the properties that can be defined for cluster plans using Wayfinder's web interface. These properties are mirrored in the corresponding CRD manifests (in YAML format) generated by Wayfinder. CLI users can refer to the information in this section to understand how the settings from Wayfinder's web interface correlate with the respective YAML files.
To learn how to view and create cluster plans, you can skip this section and proceed directly to the respective sections in Wayfinder's web interface and CLI.
Please note that Wayfinder excludes default values from the manifests. Unspecified values will use the default that the cloud provider specifies.
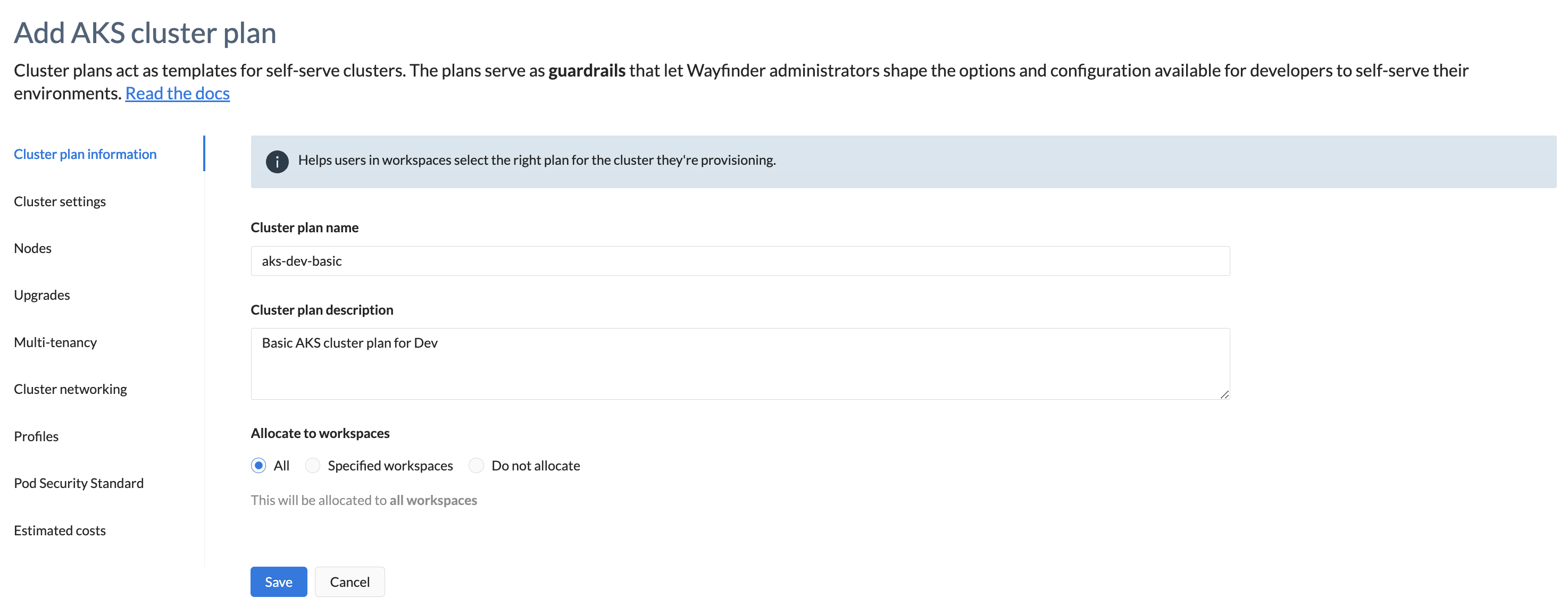
Cluster plan information
This section assists workspace members in choosing the appropriate plan for provisioning a cluster as an environment.
| Field | Description |
|---|---|
| Plan name & description | Give a suitable name and description to assist developers in selecting the correct plan when creating a cluster, for example eks-budget-plan. |
| Allocate to workspaces | Default is 'All workspaces'. Choose the workspaces in which this plan should be accessible. It can be applied to all workspaces, specific ones, or unallocated. |
YAML Example(s):
- Cluster plan is accessible in specific workspaces:
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
metadata:
name: aks-dev-basic
spec:
allocation:
type: workspaces
workspaces:
- sand
- ctest
summary: Basic AKS cluster plan for Dev
template:
providerDetails:
type: AKS
- Cluster plan is accessible in all workspaces.
spec:
allocation:
type: all
workspaces:
- '*'
- Cluster plan is unallocated to any workspace.
spec:
allocation:
type: none
To view a complete YAML example of a cluster plan, click here.
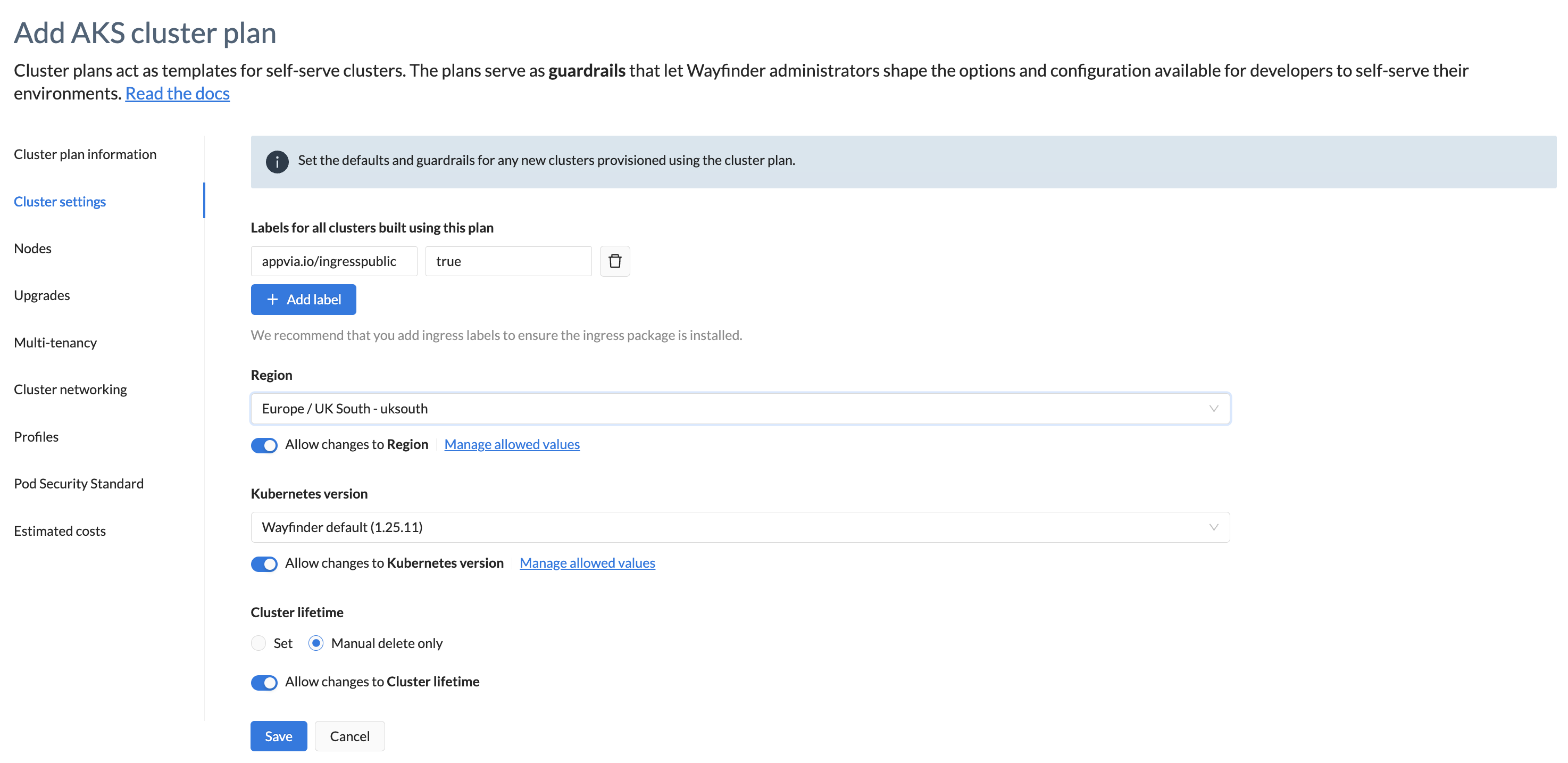
Cluster settings
This section establishes default settings and guardrails for all new clusters provisioned using the cluster plan.
- Common properties across all cloud providers:
| Field | Description |
|---|---|
| Labels | Include one or more labels. Wayfinder will automatically apply these labels to every cluster provisioned using this plan. By default, Wayfinder recommends an optional ingress label. This ensures the installation of ingress packages. |
| Region | Select a region. Every cluster provisioned using this plan will be assigned this selected region. |
| Allow changes to Region: Enabled by default allowing users the opportunity to select a region. Manage allowed values: Specify the regions that users can choose. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Kubernetes Version | Select a Kubernetes version. Every cluster provisioned using this plan will operate on the chosen Kubernetes version. The recommended default is Wayfinder's default option. |
| Allow changes to Kubernetes version: Enabled by default allowing users the opportunity to choose a Kubernetes version. Manage allowed values: Specify the Kubernetes versions that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Cluster Lifetime | Select the method for cluster deletion. The default option is manual deletion. Manual deletion: Cluster exists until you delete it manually. Set: Select this setting if you want the cluster to be automatically deleted after a specified expiration time [in hours/days/weeks]. The expiration time is displayed in the environment plans, providing developers with visibility into the duration of the cluster's availability. |
| Allow changes to Cluster lifetime: Enabled by default allowing users the opportunity to set their own cluster lifetime details. Disable: Toggle off this property if you only want your defined value(s) to apply. |
- EKS specific properties:
| Category | Field | Description |
|---|---|---|
| Cloud watch logs | Kubernetes API logs | Unspecified by default. Specified: Select the box to make use of Kubernetes API logs. |
| Allow changes to Kubernetes API logs: Enabled by default allowing users the opportunity to make use of Kubernetes API logs. Disable: Toggle off this property if you only want your defined value(s) to apply. | ||
| Kubernetes audit logs | Unspecified by default. Specified: Select the box to make use of Kubernetes audit logs. | |
| Allow changes to Kubernetes audit logs: Enabled by default allowing users the opportunity to make use of Kubernetes audit logs. Disable: Toggle off this property if you only want your defined value(s) to apply. | ||
| Kubernetes authentication logs | Unspecified by default. Specified: Select the box to make use of Kubernetes authentication logs. | |
| Allow changes to Kubernetes authentication logs: Enabled by default allowing users the opportunity to make use of Kubernetes authentication logs. Disable: Toggle off this property if you only want your defined value(s) to apply. | ||
| Kubernetes controller log | Unspecified by default. Specified: Select the box to make use of Kubernetes controller logs. | |
| Allow changes to Kubernetes controller logs: Enabled by default allowing users the opportunity to make use of Kubernetes controller logs. Disable: Toggle off this property if you only want your defined value(s) to apply. | ||
| Kubernetes scheduler component logs | Unspecified by default. Specified: Select the box to make use of Kubernetes scheduler component logs. | |
| Allow changes to Kubernetes scheduler component logs: Enabled by default allowing users the opportunity to make use of Kubernetes scheduler component logs. Disable: Toggle off this property if you only want your defined value(s) to apply. | ||
| EKS Encryption | Secrets Encryption | Unspecified by default. Specified: Selecting the box generates a new, dedicated Key Management Service (KMS) key and configures the cluster to use this for secrets encryption. WARNING - Once Secrets Encryption is enabled on a cluster, then you can't disable it on that cluster. - If you delete the cluster, then the dedicated KMS key that Wayfinder created, will also be deleted. - If you delete the KMS key, you permanently put the cluster in a degraded state. For more information see: - Amazon: Enable AWS KMS Keys - Amazon: Deleting AWS KMS Keys - Kubernetes: Encrypting Confidential Data at Rest |
| Allow changes to Secrets Encryption: Enabled by default allowing users the opportunity to select secrets encryption. Disable: Toggle off this property if you only want your defined value(s) to apply. |
- GKE specific properties:
| Category | Field | Description |
|---|---|---|
| Addons | Enable horizontal pod Autoscaler | Unspecified by default. Enabled: Select the box to enable horizontal pod Autoscaler. When enabled, the autoscaler will alter your Kubernetes workload's structure by automatically adjusting the number of Pods in response to CPU or memory consumption, or in reaction to custom metrics from within Kubernetes or external metrics from sources outside your cluster. |
| Allow changes to horizontal pod Autoscaler: Enabled by default allowing users the opportunity to make use of horizontal pod autoscaling. Disable: Toggle off this property if you only want your defined value(s) to apply. | ||
| Enable HTTP load balancer | Unspecified by default. Enabled: Select the box to enable the HTTP load balancer. When enabled, GKE will auto-discover your ingress resources and automatically provision load balancers on your behalf. | |
| Allow changes to Enable HTTP load balancer: Enabled by default allowing users the opportunity to make use of the HTTP load balancer . Disable: Toggle off this property if you only want your defined value(s) to apply. | ||
| Enable shielded nodes | Unspecified by default. Enabled: Select the box to enable shielded nodes. When enabled, this provides protection against a variety of attacks by hardening the underlying GKE node against rootkits and bootkits. | |
| Allow changes to Enable shielded nodes: Enabled by default allowing users the opportunity to make use of shielded nodes. Disable: Toggle off this property if you only want your defined value(s) to apply. | ||
| Enable Stackdriver logging | Unspecified by default. Enabled: Select the box to enable Stackdriver logging for the cluster. | |
| Allow changes to Enable Stackdriver logging: Enabled by default allowing users the opportunity to make use of Stackdriver logging. Disable: Toggle off this property if you only want your defined value(s) to apply. | ||
| Enable Stackdriver metrics | Unspecified by default. Enabled: Select the box to enable Enable Stackdriver metrics. When enabled, Stackdriver metrics are enabled for the cluster. | |
| Allow changes to Enable Stackdriver metrics: Enabled by default allowing users the opportunity to make use of Stackdriver metrics. Disable: Toggle off this property if you only want your defined value(s) to apply. |
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
metadata:
name: aks-dev-basic
spec:
policies:
- editable: true
enum:
- southindia
- australiaeast
- uksouth
path: spec.region
- editable: false
enum:
- latest
- 1.26.6
path: spec.version
- editable: false
path: spec.expires
template:
clusterLabels:
appvia.io/ingresspublic: "true"
expires: 24h0m0s
region: uksouth
version: 1.26.6
To view the complete YAML example of a cluster plan, click here.
Nodes
This section establishes the default cluster node pools. You must define at least one node pool.
- Common properties across all cloud providers:
| Field | Description |
|---|---|
| Name | Give a suitable name for the node pool or use the auto-generated name. |
| Allow changes to Name: Enabled by default allowing users the opportunity to provide their own pool name. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Description | Give a suitable description for this node pool. |
| Allow changes to Description: Enabled by default allowing users the opportunity to provide their own description. Manage allowed values: Specify the descriptions that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Auto-Scaling | Select a value for auto-scaling. Default is "yes". "Yes": Allow automatic adjustment of the number of running instances (replicas). "No": Running instances are not scaled automatically. |
| Allow changes to Auto-Scaling: Enabled by default allowing users the opportunity to use auto-scaling. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Node pool size > Minimum size | Provide the minimum number of worker nodes for this node pool. Requires Auto-scaling to be set to "yes". Default value is 1. |
| Allow changes to Minimum size: Enabled by default allowing users the opportunity to set their own minimum size. Configure Range: Specify the range that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Node pool size > Initial size | Provide the number of worker nodes that are provisioned when the node pool is created or scaled up for the first time. Default value is 1. EKS default value is 2. |
| Allow changes to Initial size: Enabled by default allowing users the opportunity to set their own initial size. Configure Range: Specify the range that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Node pool size > Maximum size | Provide the maximum number of worker nodes that the node pool can scale up to. Requires Auto-scaling to be set to "yes". Default value is 10. |
| Allow changes to Maximum size: Enabled by default allowing users the opportunity to set their own maximum size. Configure Range: Specify the range that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Maximum pods per node | Provide a value to control the density of pods running on each worker node. Default value is 110. EKS default is unspecified. |
| Allow changes to Maximum pods per node: Enabled by default allowing users the opportunity to set their own value. Configure Range: Specify the range that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Approximate pool cost | Wayfinder displays an estimated cost for running the node pool based on your node pool configuration. |
| Image type | Provide the underlying operating system that will be used for the worker nodes. The options available depend on your cloud provider. |
| Allow changes to Image type: Enabled by default allowing users the opportunity to select their own image type. Manage allowed values: Specify the values that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Machine type | Provide the virtual machine configuration that is to be used for each worker node in the cluster. The options available depend on your cloud provider. |
| Allow changes to Machine type: Enabled by default allowing users the opportunity to select their own machine type. Manage allowed values: Specify the values that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Use spot instances | Disabled by default. Enable: Spot instances can deliver significant cost savings but can be destroyed at any time. When Auto-scale is enabled, it will attempt to replace any instances that have been destroyed, but capacity to create new spot instances is never guaranteed, thus your node pool may be smaller than your specified minimum size at times. Ensure you understand the impact of this on your workloads before enabling. |
| Allow changes to Use spot instances: Enabled by default allowing users the opportunity to make use of spot instances. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Disk size | Provide the storage capacity to reserve. Units are usually in gigabytes, but check your cloud provider's documentation. Default value is 30. |
| Allow changes to Disk size: Enabled by default allowing users the opportunity to specify their own disk size. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Labels | Unspecified by default. Add label: Provide the labels you want to attach to the node pools. |
| Allow changes to Lables: Enabled by default allowing users the opportunity to specify their own lables. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Taints | Unspecified by default. Add taints: Provide one or more taints. The key and value define the characteristic that the taint represents. The effect specifies how pods without matching tolerations should be treated. The effect can be one of three options: - NoSchedule: Indicates that pods without matching tolerations will not be scheduled on that node. - PreferNoSchedule: Indicates a preference against scheduling pods without matching tolerations on nodes with the taint. - NoExecute: Prevents pods without matching tolerations from being scheduled on nodes and evicts existing pods that no longer tolerate the taint. |
| Allow changes to Taints: Enabled by default allowing users the opportunity to specify their own taints. Disable: Toggle off this property if you only want your defined value(s) to apply. |
- AKS specific properties:
| Field | Description |
|---|---|
| Mode | Provide a mode. Default is system. System: Allocated resources to be dedicated to system processes User: Allocated resources to be dedicated to user workloads such as their applications. |
| Allow changes to Mode: Enabled by default allowing users the opportunity to specify their own mode. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Max spot price | Requires 'Use spot instances' to be set to "yes". Default value is "unlimited". Unlimited: There is no maximum. Limit spot price: Provide the maximum currency amount for the spot price. |
| Allow changes to Max spot price: Enabled by default allowing users the opportunity to specify their own maximum spot price. Disable: Toggle off this property if you only want your defined value(s) to apply. |
- EKS specific properties:
| Field | Description |
|---|---|
| Additional instance types | Requires 'spot instances' to be set to "yes". Unsepecified by default. Add additional instance types: Provide additonal instances to use. |
| Allow changes to Additional instance types: Enabled by default allowing users the opportunity to make use of additional instance types. Disable: Toggle off this property if you only want your defined value(s) to apply. |
- GKE specific properties:
| Field | Description |
|---|---|
| Enable auto-repair | Unspecified by default. Enabled: Choose "yes" to enable auto-repair. When enabled, the node pool automatically repairs failed nodes. |
| Allow changes to Enable auto-repair: Enabled by default allowing users the opportunity to make use of auto-repair. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Enable auto-upgrade | Unspecified by default. Enabled: Choose "yes" to enable auto-upgrade. When enabled, the node group is configured with auto-upgrading enabled. Required to be set to enabled when the cluster version is set to any "Release channel" or "Latest", instead of a specific Kubernetes version. |
| Allow changes to Enable auto-upgrade: Enabled by default allowing users the opportunity to make use of auto-upgrade. Disable: Toggle off this property if you only want your defined value(s) to apply. |

apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
metadata:
name: aks-dev-basic
spec:
policies:
- editable: true
enum:
- dev nodepool
- sand nodepool
- test nodepool
path: spec.nodePools.0.description
- editable: true
max: 100
min: 0
path: spec.nodePools.0.autoscaling.minSize
- editable: true
max: 9
min: 0
path: spec.nodePools.0.size
- editable: true
max: 3
min: 0
path: spec.nodePools.0.autoscaling.maxSize
- editable: true
max: 50
min: 0
path: spec.nodePools.0.maxPodsPerNode
- editable: true
max: 40
min: 20
path: spec.nodePools.0.diskSize
template:
nodePools:
- autoscaling:
enabled: true
maxSize: 1
minSize: 1
description: sand nodepool
diskSize: 30
image: Windows
labels:
performance: "true"
logicalName: devpl
machine: Standard_D2_v5
maxPodsPerNode: 30
providerDetails:
aks:
mode: system
type: AKS
size: 1
spot:
aks:
maxSpotPrice: "100"
enabled: true
taints:
- effect: NoSchedule
key: performance
value: high
provider: AKS
providerDetails:
aks:
linuxProfile: {}
windowsProfile: {}
type: AKS
To view the complete YAML example of a cluster plan, click here.
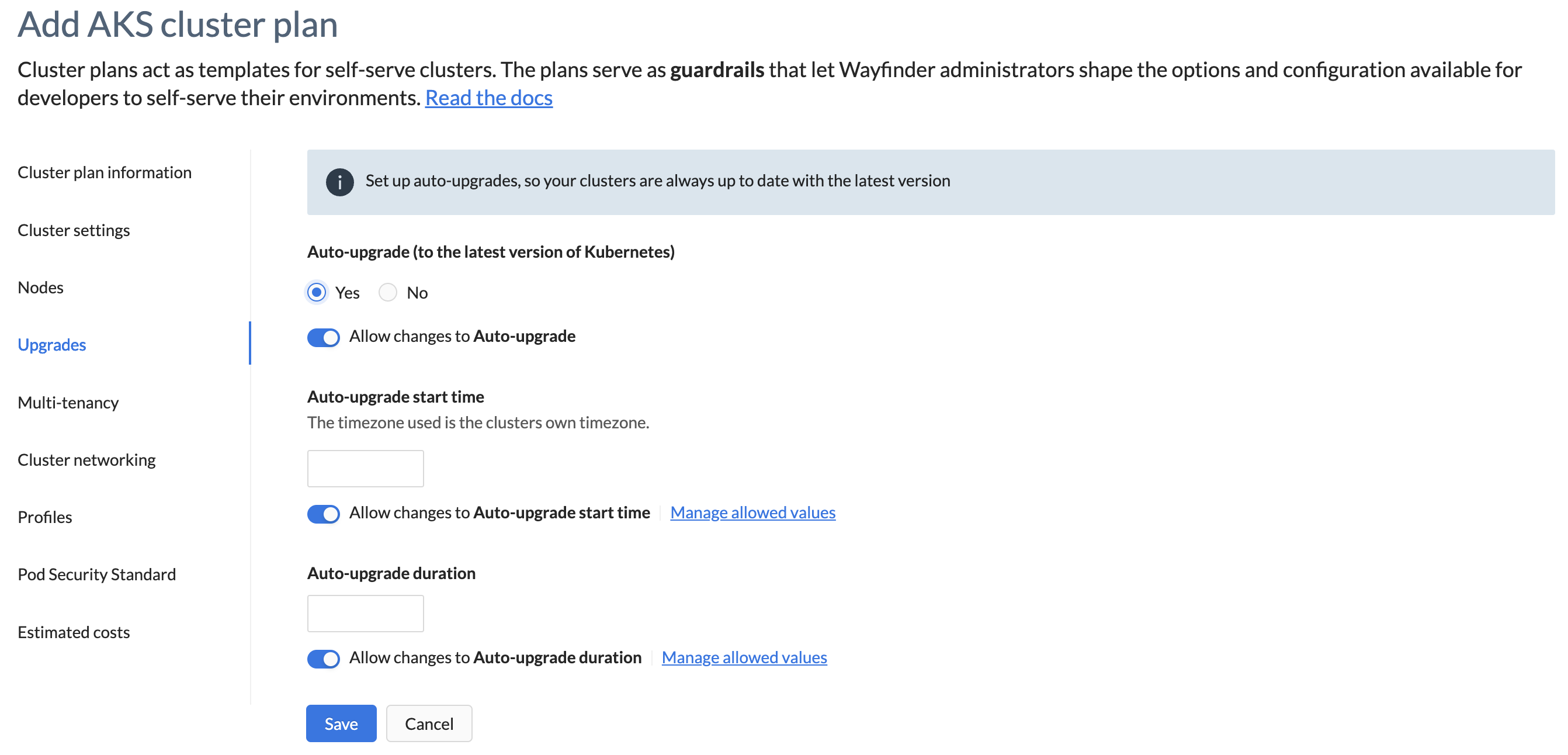
Upgrades
This section defines if clusters should be automatically upgraded to the latest Kubernetes version.
| Field | Description |
|---|---|
| Auto-upgrade | Set to "No" by default. Choose "yes" if you want all clusters created under this plan, to be automatically upgraded to the latest Kubernetes version. |
| Allow changes to Enable auto-upgrade: Enabled by default allowing users the opportunity to make use of auto-upgrade. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Auto-upgrade start time | Requires Auto-upgrade to be set to "yes". Specifies the earliest time that auto-upgrades can commence. Example: 03:00 |
| Allow changes to Auto-upgrade start time: Enabled by default allowing users the opportunity to specify their own auto-upgrade start time. Manage allowed values: Specify the range that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Auto-upgrade duration | Requires Auto-upgrade to be set to "yes". Specifies the auto-upgrade maintenance window duration. Example: 2hr |
| Allow changes to Auto-upgrade duration: Enabled by default allowing users the opportunity to specify their own auto-upgrade duration. Manage allowed values: Specify the range that users can choose from. Disable: Toggle off this property if you only want your defined value(s) to apply. |
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
metadata:
name: aks-dev-basic
spec:
template:
enableAutoUpgrade: true
expires: 24h0m0s
maintenance:
windowDuration: 4hr
windowStart: "01:00"
To view the complete YAML example of a cluster plan, click here.
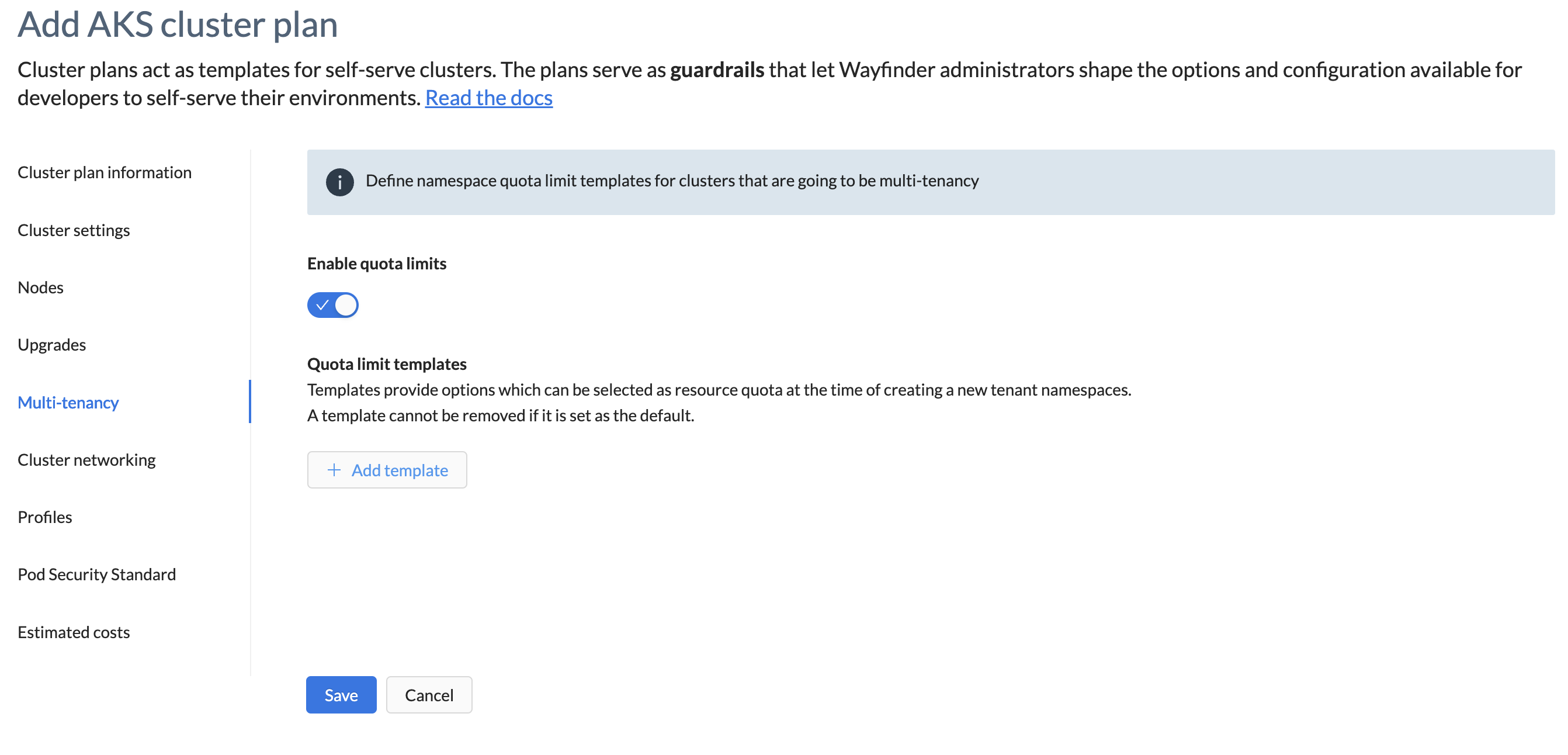
Multi-tenancy
This section defines the namespace quota limit templates for multi-tenancy clusters.
When enabled, a cluster can be shared by other workspaces and used for new application environments. The following settings define how the cluster can be used across 'tenants' of the cluster.
| Field | Description |
|---|---|
| Enable quota limits | Default is disabled. Switch the toggle on if you want to enable quota limits. |
| Template Values: | |
| - Name | Provide a meaningful name for the template |
| Allow changes to Name: Enabled by default allowing users the opportunity to specify their own template name. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| - Resource quotas | You can configure quotas for resource requests for a namespace. These limit the sum total of requests allowed for all containers in the namespace. Default value for "requests.cpu" is 1. Default value for "requests.memory" is 3.5Gi. |
| Allow changes to Resource quotas: Enabled by default allowing users the opportunity to specify their own resource quotas. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| - Limit ranges | You can configure maximum values that can be used by any pod and/or any container in a namespace. Default "type" is container. Default "cpu" value is 256m. Default "memory" is 896Mi. Default "ephemeral-storage" is 2.175Gi. |
| Allow changes to Limit ranges: Enabled by default allowing users the opportunity to specify their own limit ranges. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| - Resource defaults for a container | You can set resource defaults for containers. These are used when deployed containers don't specify their own default requests and limits. |
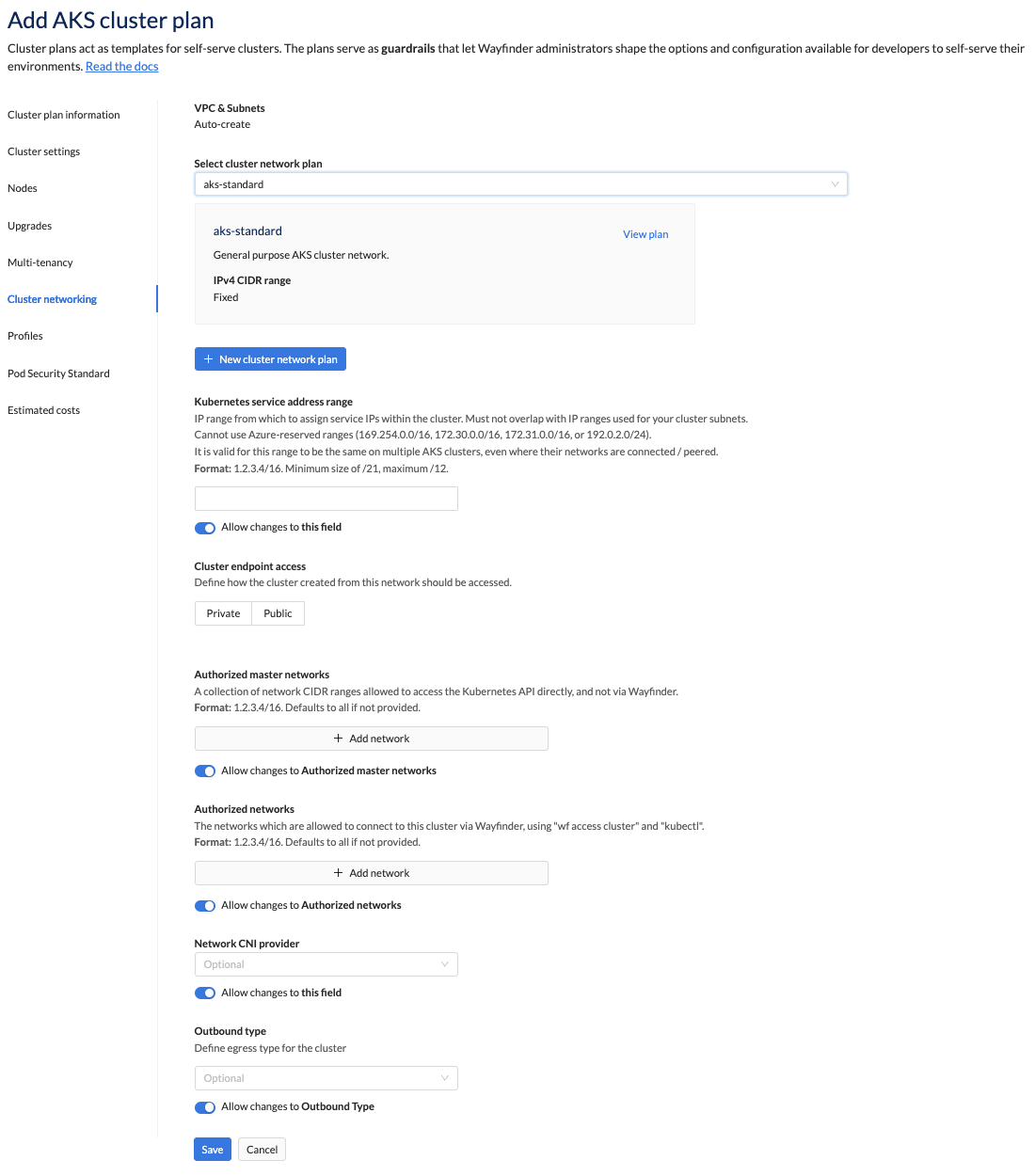
Cluster networking
This section defines networking for clusters using this plan. You must select an existing cluster network plan. If an existing one doesn't meet your needs, then you can create one on the fly.
| Field | Description |
|---|---|
| VPC & Subnets | Auto Create signifies the cluster's network that Wayfinder creates when creating a cluster with this plan. |
| Select cluster network plan | Select an existing cluster network plan from the drop-down list. A summary of the selected cluster network plan's properties is displayed. |
| New Cluster Network Plan | If you do not have an existing cluster network plan or if none of the existing ones meet your needs, then you can create one on the fly. See Create Cluster Network Plan |
| Cluster endpoint access | Unspecified by default. Define how the cluster created from this network should be accessed. You can choose between private and public. |
| Authorised master network | One entry required. This signifies a collection of network CIDR ranges allowed to access the Kubernetes API directly, and not via Wayfinder. It defaults to all if not provided. |
| Allow changes to Authorised master network: Switch the toggle on if you want to give users the ability to specify their own authorised master networks. Switch the toggle off if you only want your values to apply. | |
| Authorised networks | One entry required. This signifies the networks which are allowed to connect to this cluster via Wayfinder, using "wf access cluster" and "kubectl" commands. It defaults to all if not provided. |
| Allow changes to Authorised networks: Switch the toggle on if you want to give users the ability to specify their own authorised networks. Switch the toggle off if you only want your values to apply. | |
| Network CNI provider | Defaults to Unspecified. Only applicable to AKS and GKE. Select a Network Container Network Interface (CNI) provider. Selecting CNI signifies to use a generic CNI plugin based on the CNI specification. You can also select a speicif CNI provider from the list such as Calico. |
| Allow changes to Network CNI provider: Switch the toggle on if you want to give users the ability to specify their own network CNI provider. Switch the toggle off if you only want your values to apply. |
- Azure specific properties:
| Field | Description |
|---|---|
| Kubernetes service address range | Unspecified by default. IP range from which to assign service IPs within the cluster. - Must not overlap with IP ranges used for your cluster subnets. - Cannot use Azure-reserved ranges: -- 169.254.0.0/16 -- 172.30.0.0/16 -- 172.31.0.0/16 -- 192.0.2.0/24 - It is valid for this range to be the same on multiple AKS clusters, even where their networks are connected / peered. - Format: 1.2.3.4/16 -- Minimum size of /21 allowed -- Maximum size of /12 allowed |
| Allow changes to Kubernetes service address range: Switch the toggle on if you want to give users the ability to specify their own Kubernetes service address range. Switch the toggle off if you only want your values to apply. | |
| Outbound Type | Defines the egress type for the cluster. Default value is "Load Balancer". Option(s): - User Defined Routing - Load Balancer |
| Allow changes to Outbound Type: Switch the toggle on if you want to give users the ability to specify their own Outbound Type. Switch the toggle off if you only want your values to apply. |
- GKE specific properties:
| Field | Description |
|---|---|
| Master IPv4 CIDR | Provide the CIDR range that will be reserved for the GKE control plane components. |
| Allow changes to Master IPv4 CIDR: Switch the toggle on if you want to give users the ability to specify their own master IPv4 CIDR range. Switch the toggle off if you only want your values to apply. |
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
metadata:
name: aks-dev-basic
spec:
template:
enablePrivateCluster: false
networking:
authorizedMasterNetworks:
- cidr: 10.0.8.0/20
name: master
authorizedNetworks:
- cidr: 10.0.8.0/20
name: network
networkPlan: aks-fixed-high-performance-dev
networkProvider: cni
To view the complete YAML example of a cluster plan, click here.
Create Cluster Network Plan
This section describes the properties you need to specify when creating a new cluster network plan.
Properties common to all providers
| Field | Description |
|---|---|
| Name | Provide a meaningful name for your cluster network plan. It will help others to understand what your plan entails. |
| Description | Provide a meaningful description for your plan. |
| IPv4 CIDR range | Fixed signifies that you are using a fixed range of IP addresses. You will have a fixed number of IP addresses available across all clusters that use this plan. Therefore, clusters using this plan can't be peered together or join a corporate network. Allocated signifies that you have one or more IP address ranges available to clusters using this plan. You specify the CIDR ranges and Wayfinder will use different chunks from those ranges you specified. |
| IPv4 CIDR range > Fixed | AKS: Specify the fixed CIDR IP address range that the Node and Service should use EKS: Select the number of availability zones for the cluster. Specify the fixed CIDR IP address range that the Node should use. GKE: Specify the fixed CIDR IP address range that the Node, Service and Pod should use |
| IPv4 CIDR range > Auto-allocated | AKS: Specify the auto-allocated range size for the Node and Service. Select the CIDR range to allocate from. EKS: Select the number of availability zones for the cluster. Specify the auto-allocated range size for the Node. Select the CIDR range to allocate from. GKE: Specify the auto-allocated range size for the Node, Service and Pod. Select the CIDR range to allocate from. Note regarding the auto-allocated range table: If the table is empty, or you do not see the range you want, then you need to define a range. |
| Summary | A summary of the network ranges that Wayfinder will create and consume from. |
Azure specific properties
| Field | Description |
|---|---|
| Custom DNS Resolvers | IP addresses of custom DNS resolvers to use in the created vNet. Leave blank to use Azure's default DNS resolution |
| Routes | Specifies how traffic should be routed out of this vNet, including to other vNets, on-premises, and to the Internet. |
| - Name | The name of this route. |
| - CIDR Block | The address prefix (CIDR Block). When traffic leaves a subnet and is directed towards an IP address within the address prefix of a route, Azure uses the route containing the prefix. |
| - Next hop type | Represents how Azure routes traffic that are destined for the address prefix. Option(s): - Virtual Appliance (A virtual machine that typically runs a network application such as a firewall.) - Virtual Network Gateway (Specify when you want traffic destined for specific address prefixes routed to a virtual network gateway.) |
| - Next hop IP | When you create a route with the virtual appliance hop type, you also specify a next hop IP address. The IP address can be: - a private IP address of a network interface attached to a virtual machine - a private IP address of an Azure internal load balancer. For more information see Azure's Virtual network traffic routing. |
| Service Endpoints | The Azure Virtual Network Service Endpoints to make available in the cluster's subnet. You can specify multiple service endpoints. Option(s): - See Azure's service endpoint documentation for available options. |
AWS specific properties
| Field | Description |
|---|---|
| Availability Zones | The number of availability zones for the cluster. Option(s): - 2 - 3 |
Profiles (Azure only)
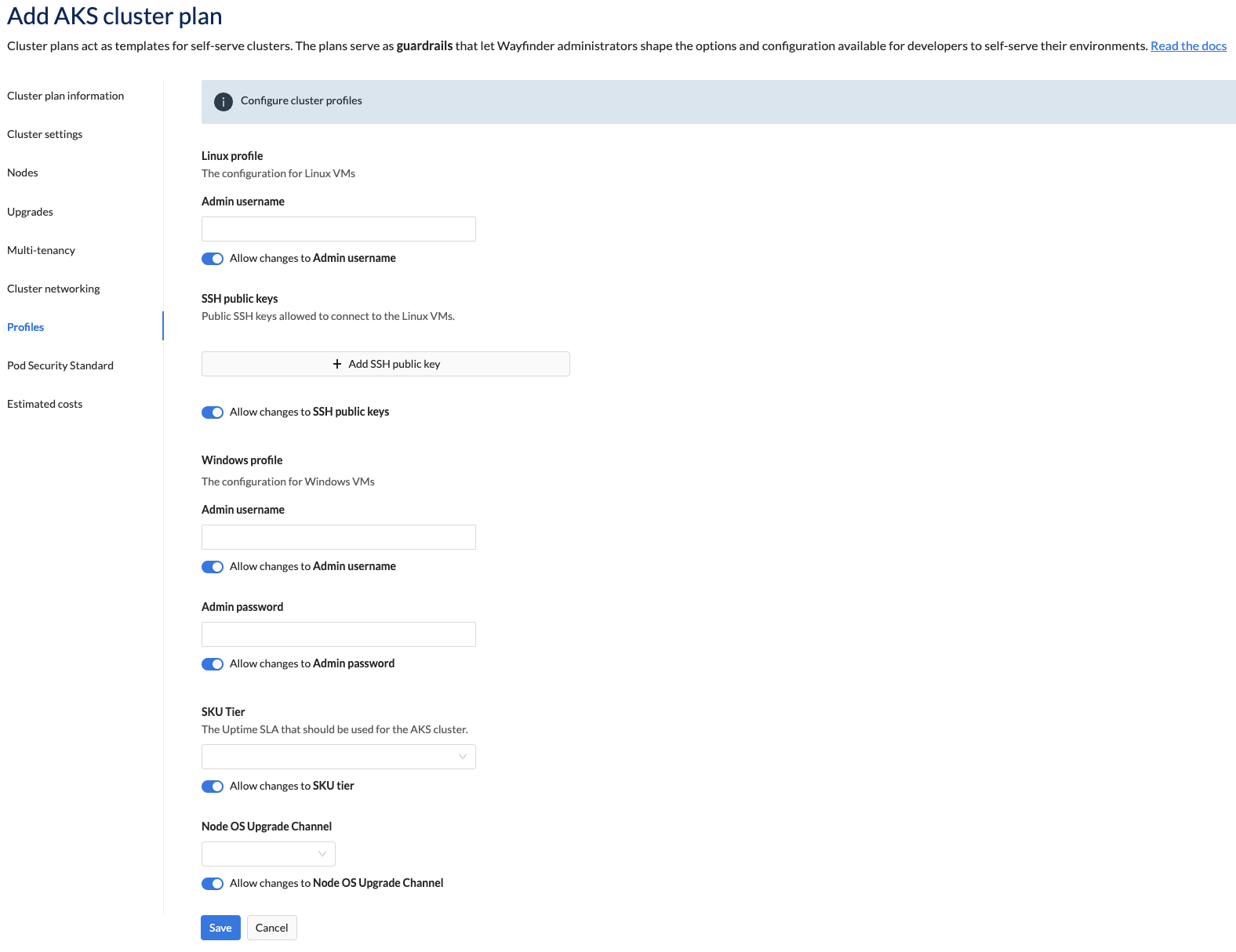
This section describes the cluster profile properties that specify administrative access and authentication for AKS clusters.
Configuration for Linux VMs or Windows VMs
| Field | Description |
|---|---|
| Admin user | Unspecified by default. Provide the administrative username. |
| Allow changes to Admin user: Enabled by default allowing users the opportunity to specify their own admin username. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| SSH public keys | Unspecified by default. Provide one or more SSH public keys. |
| Allow changes to SSH public keys: Enabled by default allowing users the opportunity to specify their own SSH public keys. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Stock Keeping Unit (SKU) Tier | Unspecified by default. Select the Uptime SLA that should be used for the AKS cluster. |
| Allow changes to SKU Tier: Enabled by default allowing users the opportunity to specify their own SKU Tier. Disable: Toggle off this property if you only want your defined value(s) to apply. | |
| Node OS Upgrade Channel | The channel to use for node-level OS security updates. The default value is "Node Image". Option(s): - None - Unmanaged - Security Patch - Node Image |
Pod Security Standards
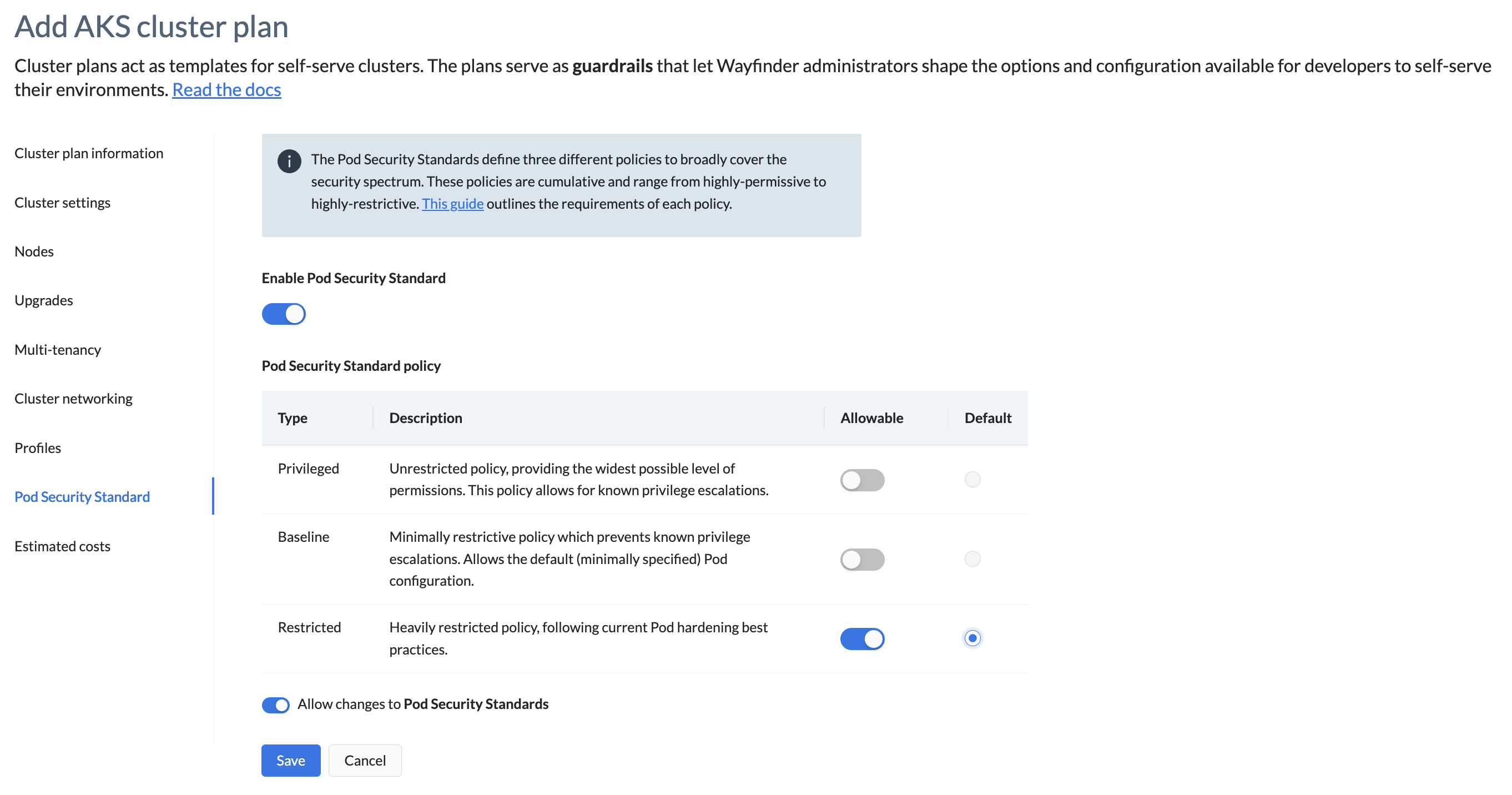
This section describes the properties that determine the type of PSS policy to enforce (such as privileged, baseline and restricted). For more information on how PSS is applied, see our Pod Security Standards page.
| Field | Description |
|---|---|
| Enable Pod Security Standards | Default is disabled. Switch the toggle on to enable. Choose if you want to allow privileged, baseline and restricted policies. You must select one of those policies to be the default. |
| Allow changes to Pod Security Standards: Enabled by default allowing users the opportunity to specify Pod Security Standards. Disable: Toggle off this property if you only want your defined value(s) to apply. |
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
metadata:
name: aks-dev-basic
spec:
security:
podSecurityStandard:
allowed:
- privileged
- baseline
- restricted
defaultProfile: baseline
enabled: true
To view the complete YAML example of a cluster plan, click here.
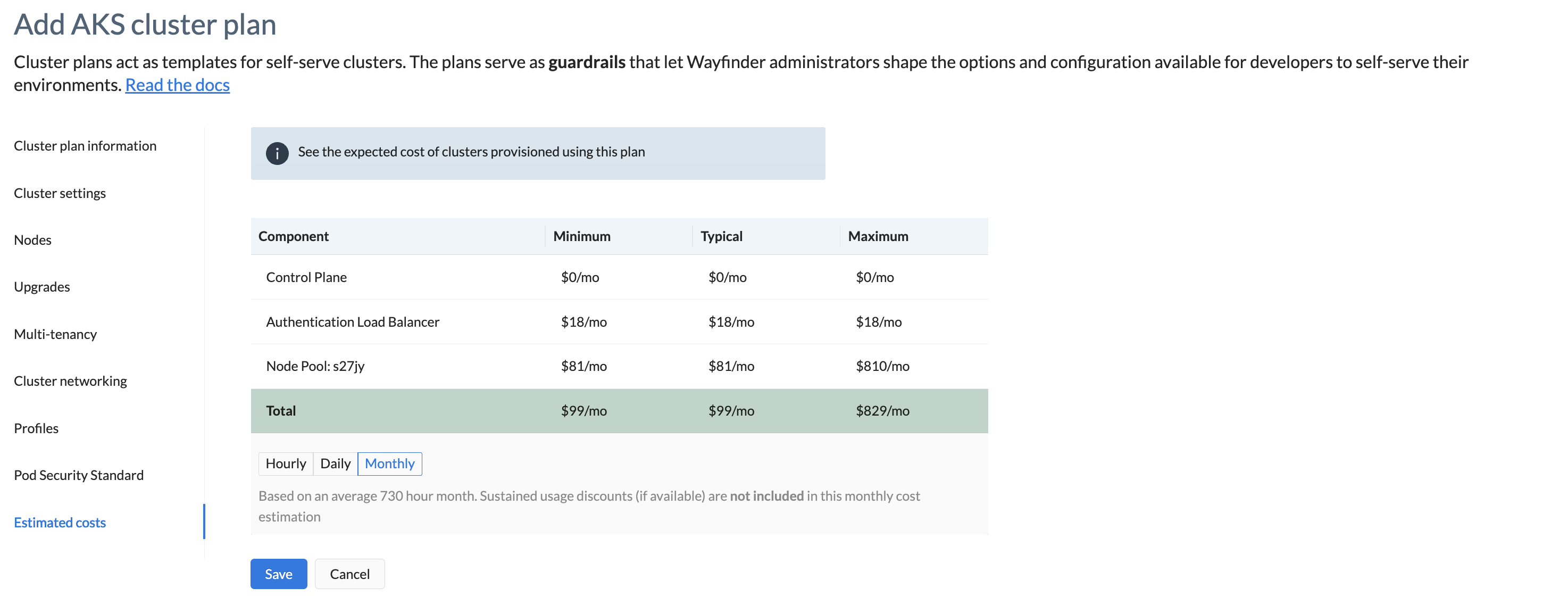
Estimated Costs
This section provides you with a summary of the likely costs your cluster will incur when you provision it using this cluster plan.
Using cluster plans with YAML
When developers (as workspace members) create an environment, they can choose to use existing infrastructure (Wayfinder creates a new namespace on an existing cluster) or choose to provision new infrastructure (Wayfinder provisions a new cluster and a namespace in accordance to the cluster plan).
When provisioning an environment using new infrastructure, either using the CLI or Wayfinder's web interface, the cluster plan is used as a boilerplate of defaults for the cluster's specifications. This cluster definition is submitted to the API and verified against the cluster plan's policy, ensuring the cluster definition does not violate any restrictions in the cluster plan.
The developer is in full control of the application's configuration and selecting an environment with a cluster configuration that suits their needs. Clusters are represented
to developers as environments, so the underlying application's environment YAML definition must have a reference spec.plan (cluster plan). Developers can only specify
cluster plans that are available to them in their workspace. By default, workspace members can't create any new cluster plans or edit existing ones. Upon creating or updating
the application environment's YAML definition, the cluster definition is verified against the cluster plan's policy.
Below is an example of the developer's application environment YAML manifest: Wayfinder provisions the cluster according to the specification outlined in the aks-playground cluster plan. For more YAML examples, please see the Application Environment section of the documentation.
➜ ~ wf create appenv --app myapp --env dev3 --cluster devhost --plan aks-playground --stage nonprod --region uksouth
kind: AppEnv
spec:
application: myapp
cloud: azure
clusterRef:
group: compute.appvia.io
kind: Cluster
name: devhost
namespace: ws-dmo
version: v2beta1
key: dev3
name: dev3
namespace: myapp-dev3
plan: aks-playground <-- This is the cluster plan
region: uksouth
stage: nonprod
Wayfinder's administrators have permissions to create new cluster plans and to edit existing ones. The exception to the rule is that Wayfinder's default cluster plans are read-only, but you can create a copy and update the settings as per your requirements. Please see the sections below for examples.
View cluster plans
By default, the cluster plans provided by Wayfinder for each cloud provider are available in all workspaces. Wayfinder administrators can choose if new cluster plans should be available in all workspaces or only some workspaces.
To view cluster plans in the CLI:
- Run
wf get clusterplan.
Cluster plans for all cloud providers are displayed:
wf get clusterplan
NAME SUMMARY CLOUD AGE
aks-hardened Hardened AKS cluster with a default "restricted" PSS Policy, recommended for Production workloads. AKS 51d
aks-playground Low cost cluster configuration for testing purposes, default expiry TTL set to 7 days. AKS 51d
aks-standard General purpose AKS cluster. AKS 51d
eks-gpu Cluster plans which contains GPU enabled nodepools EKS 30h
eks-hardened Hardened EKS cluster with a default "restricted" PSS Policy, recommended for Production workloads. EKS 51d
eks-playground Low cost cluster configuration for testing purposes, default expiry TTL set to 7 days. EKS 51d
eks-standard General purpose EKS cluster. EKS 51d
gke-hardened Hardened GKE cluster with a default "restricted" PSS Policy, recommended for Production workloads. GKE 51d
gke-playground Low cost cluster configuration for testing purposes, default expiry TTL set to 7 days. GKE 51d
gke-standard General purpose GKE cluster. GKE 51d
To view cluster plans using Wayfinder's web interface:
- Select Admin, then navigate to Kubernetes > Cluster Plans.
- Click the cloud provider that you want to see plans for, for example, Google Cloud Platform.
The plans are displayed.
Add a new cluster plan
Wayfinder's default cluster plans for each cloud provider cannot be edited. But you can add your own plans. A convenient way to add a cluster plan is to copy one, and then customise it. You can also start from scratch. Once you've added a new plan for a cloud provider and specified which workspaces the plan should be available in, workspace members in that workspace and cloud can select that plan when creating an environment.
In the cluster plan configuration, you can enforce which cluster settings can be changed by workspace owners, for example, if clusters should auto-upgrade or not.
The plan properties, and whether they are permitted to be changed, applies to any workspace you allocate this plan to. If you want to set different permissions for specific workspaces, you must create a new plan.
If you change a plan to modify the cluster configuration, this does not modify the clusters that were built from it, but applies to new clusters using that plan. However, if you update policies in the plan, the new policies are enforced for all clusters using the plan, meaning any changes to the configuration of those clusters must match the updated policies on the plan.
Services included in each cluster
Clusters created in Wayfinder come with the following pre-provisioned services:
- NGINX ingress (optional)
- Flux Helm Controller
- ExternalDNS
- cert-manager
- Auto-scalers: Installed for EKS, and enabled in GKE and AKS
- AKS: AAD Pod Identity
- EKS: Kubernetes metrics-server (available by default in GKE and AKS)
- EKS: Calico networking
Add a cluster plan in Wayfinder's web interface
To add a cluster plan:
- Click on Admin, then navigate to Kubernetes > Cluster Plans.
- Click the tab for the cloud provider that you want to add a plan for, and then click the Create [AKS/EKS/GCP] cluster plan button.
- Enter the details as described in the Properties of cluster plans section.
- Click the Save button.
Alternatively,
- If you want to copy an existing plan, then select your desired plan and then click on the Copy button.
- Enter the details as described in the tables below.
- Click Save.
For most plan properties, you can set whether to allow changes. When you allow changes, then workspace owners and members will be able to edit those parameters.
Add a cluster using the CLI
You can also create your own plan by writing a .yaml file specifying the plan properties, and then applying it to Wayfinder using the
CLI. We recommend you start with an out-of-the-box plan and edit it to suit your needs.
To create a new cluster plan from an existing one:
- Get the yaml from an existing plan:
wf get clusterplan gke-playground -o yaml > MYPLAN.yaml
This copies the the gke-playground cluster plan and places it in a file MYPLAN.yaml.
- Edit the plan file as needed, being sure to change the metadata name to a new name to indicate that you wish to make a new plan. Thereafter, apply the file:
wf apply -f MYPLAN.yaml
You can prevent workspaces from editing a parameter when creating a cluster by setting editable to false for that parameter. In below example
the cluster's region, version and upgrade method is locked (set to false) from being edited. The cluster's lifetime is editable (set to true).
policies:
- editable: false
path: spec.region
- editable: false
path: spec.version
- editable: true
path: spec.expires
- editable: false
path: spec.enableAutoUpgrade
Associate a plan to a workspace
Cluster plans can be allocated to one or more workspaces using the spec.allocation field in the resource definition.
For the full plan specification, see PlanSpec.
The YAML example below specifies that the cluster plan is available in all workspaces.
spec:
allocation:
type: all
workspaces:
- '*'
The YAML example below specifies that the cluster plan is only available in the 'sandbox' workspace.
spec:
allocation:
type: workspaces
workspaces:
- sandbox
Network capacity and availability
Wayfinder inlcudes the clusterNetwork and networkCapacity details under status.
clusterNetwork > exampleNetworkdemonstrates the next network range that Wayfinder will create from this plan, when a Cluster Network is created.networkCapacityindicates that the network ranges have capacity and can be used for at least one more network.
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
name: eks-test1
spec:
status:
clusterNetwork:
exampleNetwork:
awsVPC:
cidr: 10.0.0.0/24
subnets:
- availabilityZone: az-1
cidr: 10.0.0.64/26
natGateway: true
type: EKSPrivate
- availabilityZone: az-2
cidr: 10.0.0.128/26
natGateway: true
type: EKSPrivate
- availabilityZone: az-3
cidr: 10.0.0.192/26
natGateway: true
type: EKSPrivate
- availabilityZone: az-1
cidr: 10.0.0.0/28
type: EKSPublic
- availabilityZone: az-2
cidr: 10.0.0.16/28
type: EKSPublic
- availabilityZone: az-3
cidr: 10.0.0.32/28
type: EKSPublic
networkCapacity:
- hasCapacity: true
stage: nonprod
- hasCapacity: true
stage: prod
Define the management peering rule
This is only required for private clusters. Skip this if your plan does not enable a private cluster.
Wayfinder requires direct connectivity to the public kubernetes API. This is the cloud managed Kubernetes API, not the authentication module.
Setting a cluster to private (enablePrivateCluster: true in the above cluster plan) removes all public access to the API endpoint, so you must create a peering back to the
management network.
To define the management peering rule:
- Create a resource file and apply it using the CLI:
wf apply -f FILENAME
Here's a sample peering rule definition:
---
apiVersion: networking.appvia.io/v1alpha1
kind: PeeringRule
metadata:
name: management
spec:
filters:
allocation:
type: all
selectors:
matchExpressions:
- key: networking.appvia.io/peering
operator: In
values: ["true"]
- key: appvia.io/provider
operator: In
values: ["aws"]
connection:
type: peering
peering:
enableAutoApproval: true
YAML Examples
AKS yaml example
~ wf get clusterplan aks-dev-basic -o yaml
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
name: aks-dev-basic
spec:
allocation:
type: workspaces
workspaces:
- sand
- ctest
policies:
- editable: true
enum:
- southindia
- australiaeast
- uksouth
path: spec.region
- editable: true
enum:
- dev nodepool
- sand nodepool
- test nodepool
path: spec.nodePools.0.description
- editable: true
max: 100
min: 0
path: spec.nodePools.0.autoscaling.minSize
- editable: true
max: 9
min: 0
path: spec.nodePools.0.size
- editable: true
max: 3
min: 0
path: spec.nodePools.0.autoscaling.maxSize
- editable: true
max: 50
min: 0
path: spec.nodePools.0.maxPodsPerNode
- editable: true
max: 40
min: 20
path: spec.nodePools.0.diskSize
- editable: false
enum:
- latest
- 1.26.6
path: spec.version
- editable: false
path: spec.expires
summary: Basic AKS cluster plan for Dev
template:
clusterLabels:
appvia.io/ingresspublic: "true"
enableAutoUpgrade: true
enablePrivateCluster: false
expires: 24h0m0s
maintenance:
windowDuration: 4hr
windowStart: "01:00"
networking:
aksServicesNetwork: 10.0.0.0/21
authorizedMasterNetworks:
- cidr: 10.0.8.0/20
name: master
authorizedNetworks:
- cidr: 10.0.8.0/20
name: network
networkPlan: aks-fixed-high-performance-dev
networkProvider: cni
nodePools:
- autoscaling:
enabled: true
maxSize: 1
minSize: 1
description: sand nodepool
diskSize: 30
image: Windows
labels:
performance: "true"
logicalName: devpl
machine: Standard_D2_v5
maxPodsPerNode: 30
providerDetails:
aks:
mode: system
type: AKS
size: 1
spot:
aks:
maxSpotPrice: "100"
enabled: true
taints:
- effect: NoSchedule
key: performance
value: high
provider: AKS
providerDetails:
aks:
linuxProfile: {}
nodeOSUpgradeChannel: SecurityPatch
outboundType: userDefinedRouting
windowsProfile: {}
type: AKS
region: uksouth
security:
podSecurityStandard:
allowed:
- privileged
- baseline
- restricted
defaultProfile: baseline
enabled: true
version: 1.26.6
EKS yaml example
wf get clusterplans eks-test1 -o yaml
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
metadata:
name: eks-test1
spec:
allocation:
type: all
summary: eks-test1-desc
template:
channel: default
clusterLabels:
appvia.io/ingresspublic: "true"
enableAutoUpgrade: false
enablePrivateCluster: true
networking:
authorizedMasterNetworks:
- cidr: 10.0.8.0/24
name: master
authorizedNetworks:
- cidr: 10.0.8.0/25
name: network
networkPlan: eks-standard
nodePools:
- autoscaling:
enabled: true
maxSize: 10
minSize: 1
description: syak8-desc
diskSize: 30
image: AL2_x86_64
logicalName: syak8
machine: t3.large
size: 2
spot:
eks: {}
provider: EKS
providerDetails:
eks:
cloudWatchLogging:
api: true
audit: true
authenticator: true
controllerManager: true
scheduler: true
encryption:
secretsEncryptionEnabled: true
type: EKS
region: eu-west-2
security:
podSecurityStandard: {}
GKE yaml example
wf get clusterplans gke-test1 -o yaml
apiVersion: compute.appvia.io/v2beta1
kind: ClusterPlan
name: gke-test1
spec:
allocation:
type: all
summary: gke-test1-desc
template:
channel: default
clusterLabels:
appvia.io/ingresspublic: "true"
enablePrivateCluster: false
networking:
authorizedMasterNetworks:
- cidr: 10.0.8.0/24
name: master1
authorizedNetworks:
- cidr: 10.0.8.0/25
name: network1
networkPlan: gke-standard
networkProvider: calico
nodePools:
- autoscaling:
enabled: true
maxSize: 10
minSize: 1
description: znqfp-desc
diskSize: 30
image: COS_CONTAINERD
logicalName: znqfp
machine: n2-standard-2
maxPodsPerNode: 110
providerDetails:
gke:
enableAutorepair: true
enableAutoupgrade: true
type: GKE
size: 1
spot: {}
provider: GKE
providerDetails:
gke:
enableHTTPLoadBalancer: true
enableHorizontalPodAutoscaler: true
enableShieldedNodes: true
enableStackDriverLogging: true
enableStackDriverMetrics: true
masterIPV4Cidr: 10.0.8.0/24
type: GKE
region: europe-west2
security: {}