Management Network
This topic provides an example of how to peer back to the Wayfinder management cluster.
In the peering rule definition, if no external network is defined in spec.connection.peering.network, Wayfinder automatically peers back to the management network. See this example, which has a definition for this field.
Requirements for this example
Let's assume you have these requirements:
-
Provision private clusters for all production workloads.
-
Switch EKS clusters to private. This removes access to the clusters' public Kubernetes API endpoint, so only internal traffic is permitted access to it.
-
To talk to private clusters, Wayfinder needs access to their Kubernetes API endpoint. So create a peering connection between the Wayfinder management cluster and private clusters' control plane.
-
You are not using a hub and spoke network, so you must peer back to the management network.
-
Use a dedicated network for remote access, and users will use VPN.
Network topology
This diagram depicts the topology we want to achieve.
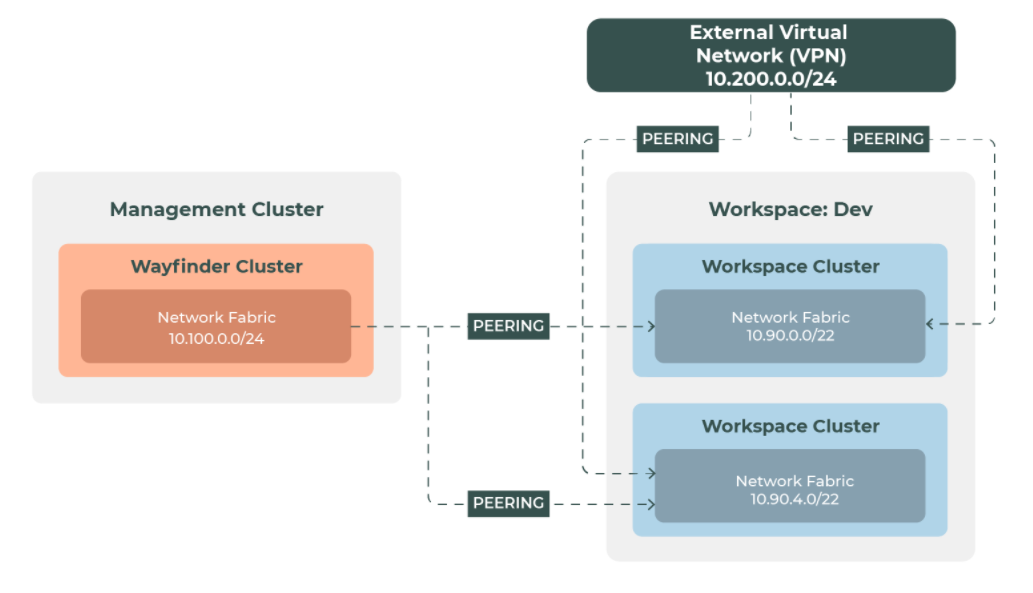
Peering definitions
You can also define and manage peering rules in Wayfinder's web interface.
You can achieve the above topology using two rules that implement the following:
- Peer all private clusters in the production (prod) [stage]/wayfinder/admin/stages/stages-overview back to the Wayfinder management cluster network.
- Create the peering connections to the network you are using for remote access.
Connection back to Wayfinder's management network
The first peering rule creates a connection from all private clusters in the prod stage back to Wayfinder's management network:
---
apiVersion: networking.appvia.io/v1alpha1
kind: PeeringRule
metadata:
name: management
spec:
filters:
allocation:
type: all
selectors:
matchExpressions:
- key: appvia.io/stage
operator: In
values: [prod]
- key: networking.appvia.io/peering
operator: In
values: ["true"]
connection:
type: peering
peering:
enableAutoApproval: true
Connection to the remote access network
The second peering rule wires up all the clusters designated as private to the
network running out a remote access appliance (for VPN). For private clusters, Wayfinder automatically adds the label networking.appvia.io/peering to the network fabric.
See the Private Clusters for details on how to provision the cloud accounts required.
---
apiVersion: networking.appvia.io/v1alpha1
kind: PeeringRule
metadata:
name: vpn
spec:
filters:
allocation:
type: all
selectors:
matchExpressions:
- key: appvia.io/stage
operator: In
values: [prod]
- key: networking.appvia.io/peering
operator: In
values: ["true"]
# Cloud account which has the permissions to accept peering
cloudAccount:
name: vpn
namespace: ws-admin
connection:
type: peering
peering:
enableAutoApproval: true
network:
# the aws account which
account: 909724866242
# the vpc identifier
identifier: vpc-11111111
# the aws region of the network
location: eu-west-2
# the region the virtual
routes:
- 10.200.0.0/24
# a collection of tags used to identify the
# routing table
routeTableSelectors:
tag:Name: main