Specify Additional AWS Settings
< packages | cluster plan creation workflow


Overview
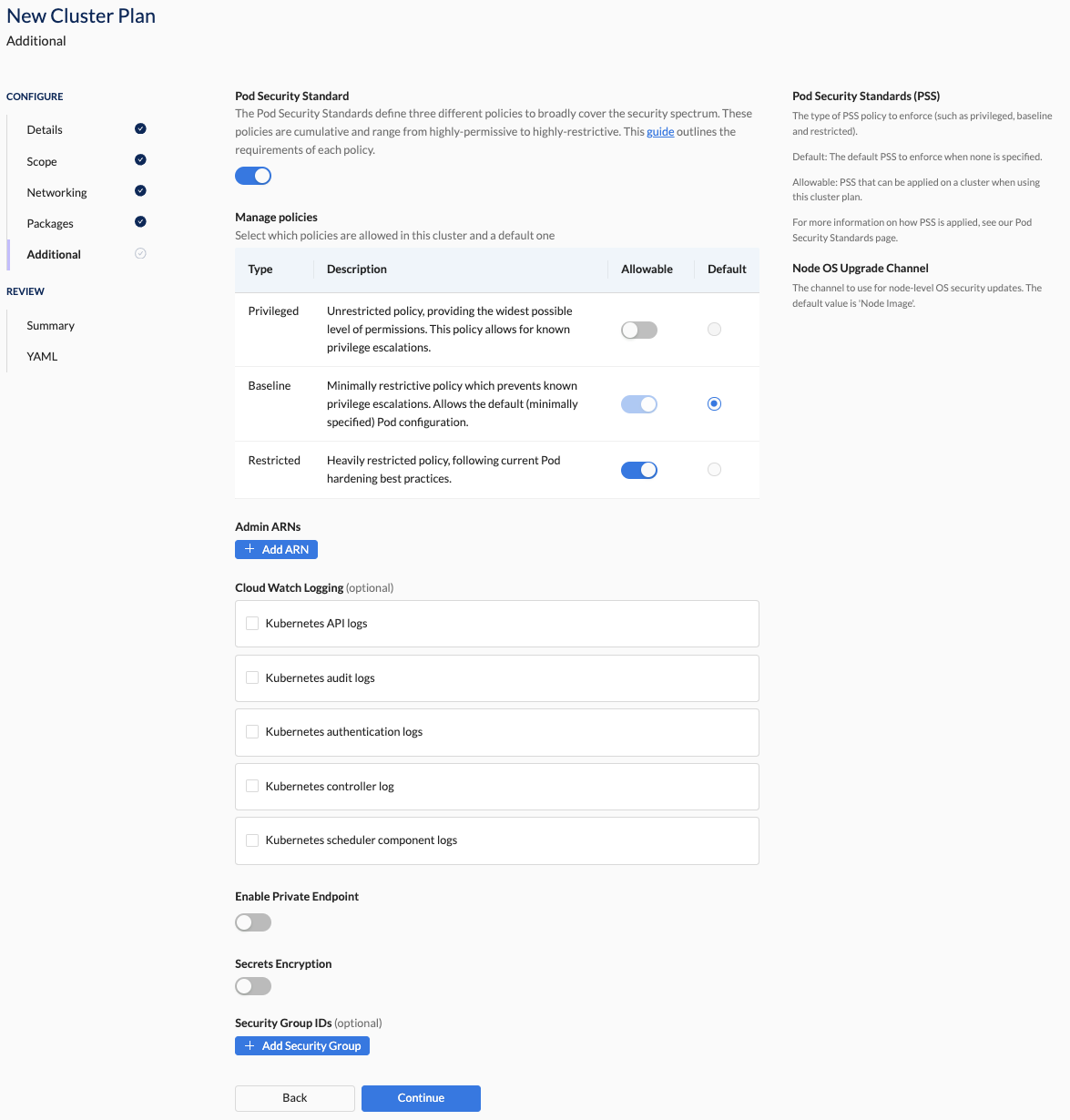
In this section, you specify the Pod Security Standards (PSS) to enforce, along with any optional AWS-specific settings.
Pod Security Standards (PSS):
This setting enforces security policies for Kubernetes clusters. You define default and allowable standards for flexibility and compliance.
AWS-specific settings:
- Admin ARNs: Provides the specified IAM role ARNs with administrative access to the cluster in AWS directly.
- CloudWatch Logging: Route cluster control plane logs to AWS' CloudWatch service. Note that this can have significant cost implications on busier clusters.
- Private Endpoint: By configuring a Private Endpoint, cluster access is restricted to internal networks, minimising exposure to the public internet. This setup enhances security by reducing potential attack vectors and safeguarding sensitive data against unauthorised access.
- Secrets Encryption: Leveraging AWS Key Management Service (KMS), this feature ensures robust data security by encrypting sensitive information at rest within the cluster. This cryptographic protection mechanism helps adhere to compliance requirements and mitigates data breach risks.
- Security Group IDs: Provide specific additional security group IDs to provide to EKS when provisioning the cluster. This will be in addition to those generated automatically by Wayfinder for the network defined in the cluster network plan.
📚 For more details on key points, refer to the overview section.
📚 Explore the properties section for additional information on each UI property.
CLI Instructions
Create a new cluster plan
Follow the instructions in the details section.
Web Interface Instructions
Steps
- Fill in the scope details as outlined in the properties section.
- Click Continue to proceed
Screenshot(s)

Properties
| Field | Description |
|---|---|
| Enable Pod Security Standards | Choose if you want to allow privileged, baseline and restricted policies. You must select one of those policies to be the default. |
| Admin ARNs | Administrator Access ARNs. Admin ARNs uniquely identify AWS users or roles with administrative privileges to manage and access the cluster's resources and services. Add as many as you need. |
| Cloud Watch Logging | Optionally select which logs should be forwarded to the AWS Cloud Watch Logging service for clusters created with this plan. Refer to AWS CloudWatch Logs documentation for more details. |
| - Kubernetes API Logs | Option(s): - Unspecified (default) - Specified: Select the box to send Kubernetes API logs to CloudWatch. |
| - Kubernetes audit logs | Option(s): - Unspecified (default) - Specified: Select the box to send Kubernetes audit logs to CloudWatch.. |
| - Kubernetes authentication logs | Option(s): - Unspecified (default) - Specified: Select the box to send Kubernetes authentication logs to CloudWatch. |
| - Kubernetes controller log | Option(s): - Unspecified (default) - Specified: Select the box to send Kubernetes controller logs to CloudWatch. |
| - Kubernetes scheduler component logs | Option(s): - Unspecified (default) - Specified: Select the box to send Kubernetes scheduler component logs to CloudWatch. |
| Enable Private Endpoint | Options(s): - Disabled (default) - Enabled: The Kubernetes API endpoint will only be privately accessible and not connected to the public internet. |
| Secrets Encryption | EKS Encryption. Option(s): - Disabled (default) - Enabled: Generates a new, dedicated Key Management Service (KMS) key and configures the cluster to use this for secrets encryption. WARNING - Once Secrets Encryption is enabled on a cluster, then you can't disable it on that cluster. - If you delete the cluster, then the dedicated KMS key that Wayfinder created, will also be deleted. - If you delete the KMS key, you permanently put the cluster in a degraded state. For more information see: - Amazon: Enable AWS KMS Keys - Kubernetes: Encrypting Confidential Data at Rest |
| Security Group IDs | Provide specific additional security group IDs to provide to EKS when provisioning the cluster. This will be in addition to those generated automatically by Wayfinder for the network defined in the cluster network plan. Refer to AWS documentation for more details. Specify as many as you need. |