Configure Workload Identities
Where needed, specify if the package's workload identity need access to an AWS Account, Azure Subscription or GCP Project. You have the option to configure one workload identity per cloud provider. If a package doesn't require cloud access then select the 'no' option when prompted.
If a workload identity is specified, the package will only be usable on clusters in the cloud provider(s) configured here. Wayfinder does not support cross-cloud workload identity for packages, so cloud access is limited to the provider that the cluster is running within.
CLI Instructions
Use the wf init package PACKAGE --helm-repo REPO command to create a package.
- Select 'yes' when prompted if you want to enable a workload identity.
wf init package pkg1 --helm-repo https://charts.bitnami.com/bitnami
? Chart: thanos
? Chart version: 15.4.2
? Enable WorkloadIdentity in package Yes # Make sure that you select 'yes'
? What cloud(s) do you want to enable? Use a comma separated list (aws,azure,gcp) aws,azure,gcp # Specify one or more clouds
- Wayfinder outputs the YAML to console for you to copy into a file and edit as needed.
ws,azure,gcp
apiVersion: package.appvia.io/v2beta2
kind: Package
metadata:
creationTimestamp: null
name: pkg2
spec:
description: Thanos is a highly available metrics system that can be added on top
of existing Prometheus deployments, providing a global query view across all Prometheus
installations.
helm:
chartName: thanos
chartVersion: 15.4.2
releaseName: thanos
repositoryURL: https://charts.bitnami.com/bitnami/thanos-15.4.2.tgz
values: null
valuesTemplate: |-
# Prepare this field with the values you wish to apply to the helm chart on deployment.
# To see the values available for this chart run:
# helm repo add charts.bitnami.com-bitnami https://charts.bitnami.com/bitnami
# helm show values charts.bitnami.com-bitnami/thanos --version 15.4.2
#
# Run 'wf describe vars' to understand the Wayfinder template variables you can use in this template
# Ensure you map the service account annotations here, like this:
# serviceAccountAnnotations:
# {{ .Package.WorkloadIdentity.ServiceAccountAnnotations | toYaml | indent 2 }}
# serviceAccountName: PROVIDE SERVICE ACCOUNT NAME
installNamespace: CHANGE TO A VALID NAMESPACE
selectors: {}
version: 1.0.0
workloadIdentity: # A section is included for each cloud provider that you've specified in the CLI command
role:
aws:
customIAMPolicyTemplate: |
# Enter your custom IAM policy here, like this:
# Version: "2012-10-17"
# Statement:
# - Sid: AllowListBucket
# Effect: Allow
# Action: s3:ListBucket
# Resource: arn:aws:s3:::{{ .Cluster.Name }}-workload-bucket*
azure:
roleAssignmentsTemplate: |
# Enter your RoleAssignmentsTemplate here, like this:
# - scope: /subscriptions/{{ .CloudAccessConfig.Azure.Subscription }}
# roleDefinitionName: Reader
gcp:
iamRoleBindingsTemplate: |
# Enter your IAMRoleBindingsTemplate here, like this:
# - role: roles/iam.workloadIdentityUser
# scopeType: Project
serviceAccountName: PROVIDE NAME OF SERVICE ACCOUNT IN INSTALL NAMESPACE THAT
THIS IDENTITY IS FOR
status:
ownedResources: {}
status: ""
- Include the
--non-interactiveflag - Specify the chart using the
--chart CHARTflag - Specify the chart version using the
--version MAJOR.MINOR.PATCHflag - Include the
--enable-workload-identityflag and specify the clouds that you require access for.
EXAMPLE:
wf init package pkg3 --helm-repo https://charts.bitnami.com/bitnami --non-interactive --chart thanos --version 15.4.3 --enable-workload-identity aws,azure,gcp
Above produces the same yaml output as show above when using Wayfinder's interactive prompts.
Web Interface Instructions
Steps
- If your package requires cloud access:
- Select the Yes option
- Fill in the details as outlined in the properties section.
- Click the Continue button
- If your package doesn't require any cloud access:
- Select the No option
- Click the Continue button
Screenshot(s)
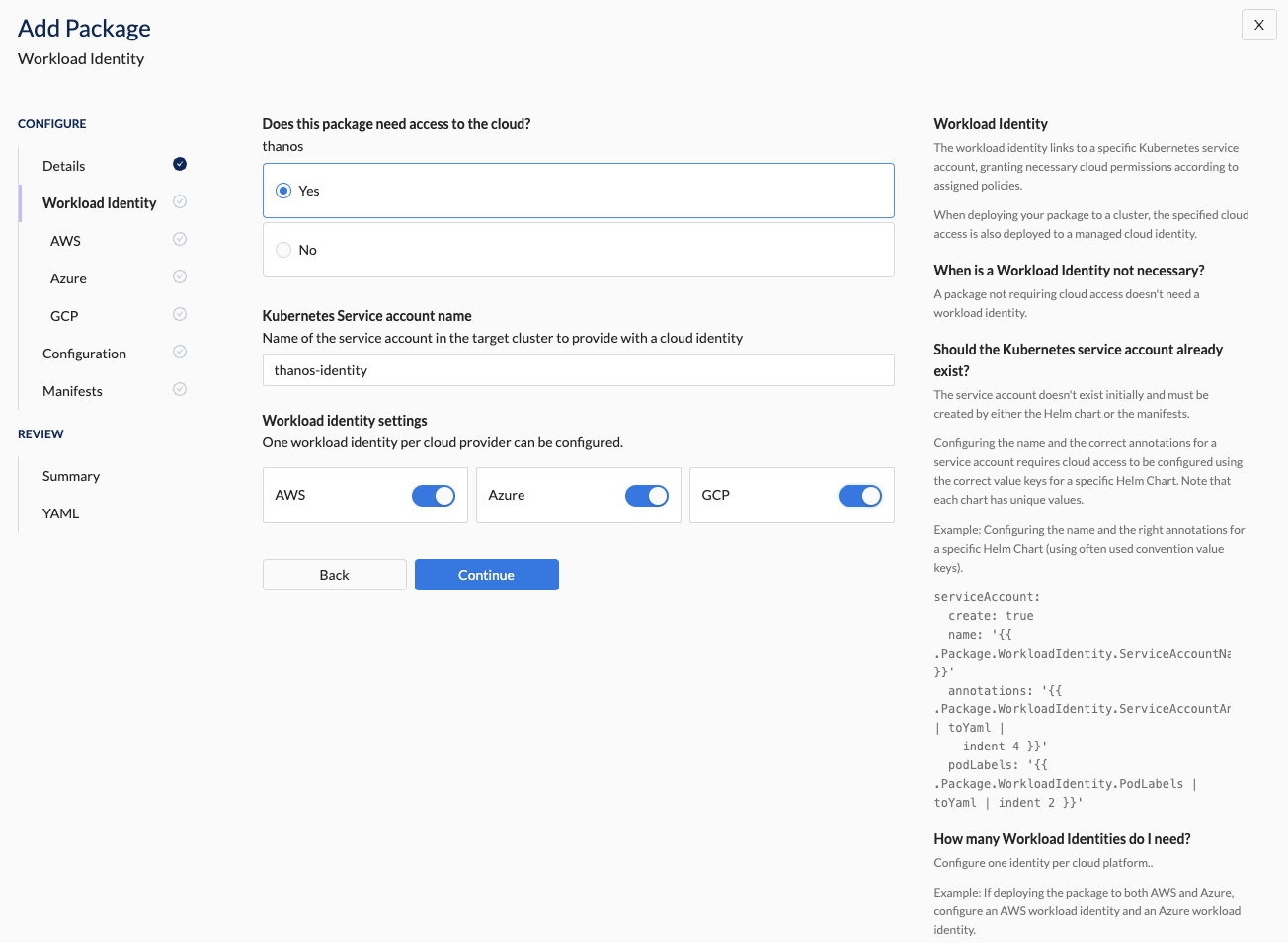
- Cloud access required
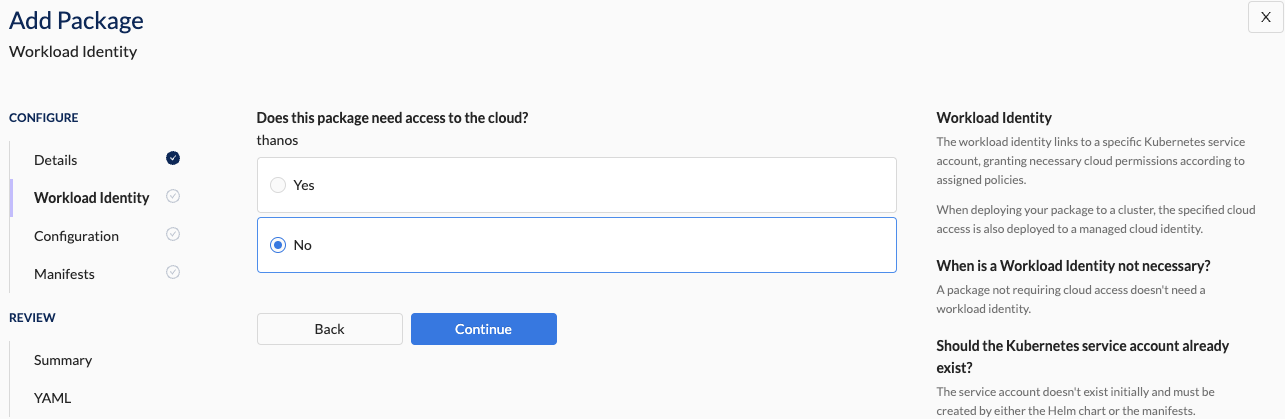
- Cloud access not required
Properties
| Field | Description |
|---|---|
| Does this package need access to the cloud? | Indicates if the package requires cloud access. Option(s): - No (default): The package doesn't require cloud access. - Yes: The package requires cloud access. |
The following properties are applicable if the package requires cloud access:
| Field | Description |
|---|---|
| Kubernetes Service account name | Name of the Kubernetes service account in the target cluster that will be provided with a cloud identity. The service account must already exist or be created. See example: YAML for creating a service account. |
| Workload identity settings | The Provider for which the workload identity is to be configured. Option(s): Specify at least one. - AWS: AWS Account - Azure: Azure Subscription - GCP: GCP Project |
What comes next?
If the package requires cloud access, then you need to configure the corresponding Policy Definition(s):
If your package doesn't require cloud access:
Related Reading
Examples
YAML for creating a service account
The service account doesn't exist initially and must be created by either the Helm chart or the manifests. Configuring the name and the correct annotations for a service account requires cloud access to be configured using the correct value keys for a specific Helm Chart. Note that each chart has unique values.
serviceAccount:
create: true
name: '{{ .Package.WorkloadIdentity.ServiceAccountName }}'
annotations:
{{ .Package.WorkloadIdentity.ServiceAccountAnnotations | toYaml | indent 4 }}
podLabels:
{{ .Package.WorkloadIdentity.PodLabels | toYaml | indent 2 }}