Azure Policy Definition
The policy definition outlines the actions that the Kubernetes service account is allowed to undertake in Azure when running on an Azure AKS cluster, such as interacting with cloud services like DNS zones or cloud storage.
Add your policy in the YAML generated by wf init package or prepare it using the Web Interface. See the CLI instructions section for details where you selected 'yes' when asked if your workload identity required cloud access.
Web Interface Instructions
Steps
- Use the text editor to define a policy. See example: Azure Workload Identity Assignment Template
- Use Wayfinder's Templating Language to make the policy specific for different environments or resources.
- Click the Continue button
Screenshot(s):
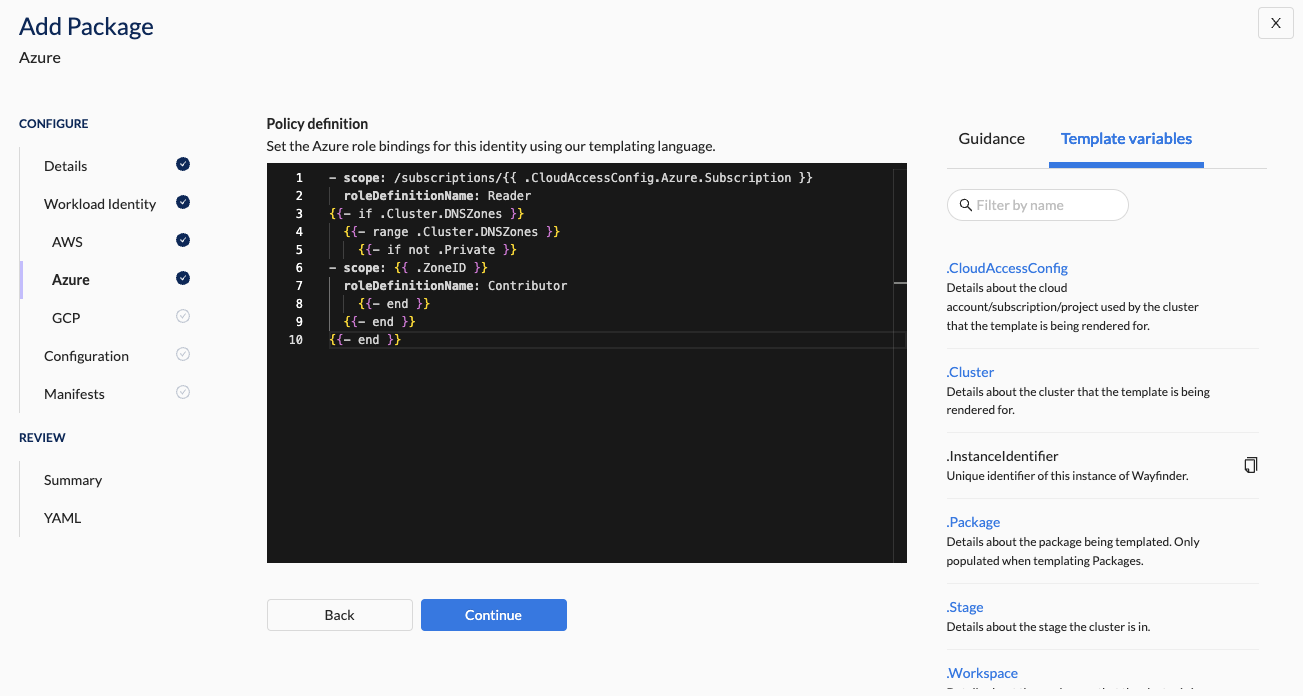
Properties
| Field | Description |
|---|---|
| Policy Definition | The YAML of the custom policy definition. - roleDefinitionName: Name of an Azure built-in role definition to use. - scope: Azure scope to assign the role definition to. This allows you to limit the scope of the permissions to specific resources, a resource group, or subscription-wide for the cluster's subscription. See example template for reference. |
What comes next?
If the package requires cloud access to other Providers, then you need to configure the corresponding Policy Definition(s):
If your package doesn't require further cloud access configuration:
Related Reading
Examples
Azure Workload Identity Assignment Template
- scope: /subscriptions/{{ .CloudAccessConfig.Azure.Subscription }}
roleDefinitionName: Reader
{{- if .Cluster.DNSZones }}
{{- range .Cluster.DNSZones }}
{{- if not .Private }}
- scope: {{ .ZoneID }}
roleDefinitionName: Contributor
{{- end }}
{{- end }}
{{- end }}