Azure Hub and Spoke
A common pattern within Azure networking is a hub and spoke topology, where a central backbone enables transitive routing, allowing for centrally managed access controls, egress, and so forth.
We offer more than just VPC peering support; we provide the capability to utilise the hub network as a gateway for all traffic. This empowers users to take control of their egress (outbound) traffic, such as through a virtual appliance.
Centrally managed Hub network
Example requirements
- We want to hook up our networks into a centrally managed hub network in a specific workspace.
- We want all traffic regardless of whether it's private or public via the transit network in the workspace.
- We want the management network to be isolated from the rest of the hub network and connect only to private clusters.
- We want to scope the connection to a single workspace.
Network Topology
The following depicts the intended network topology we aim to achieve.
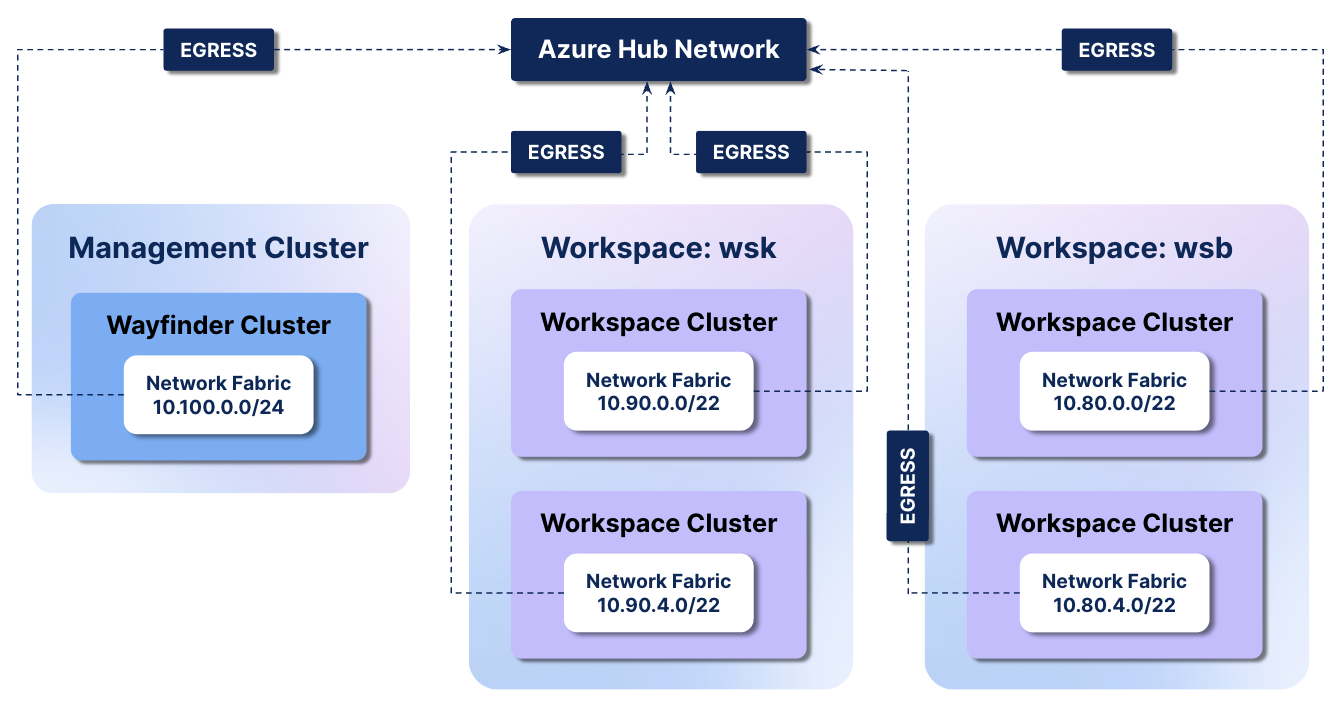
Peering Definition
In this example, you define two peering rules to:
- Connect the Wayfinder management network to all private clusters.
- For workspace
wsk, connect the private cluster networks into the hub.
First you must define the rule that connects the management network to all private clusters.
The example below is to demonstrate the flexibility of the definition. A more likely situation would be to route all traffic via the hub network and forgo any direct peering between the management and workspace networks.
1 - Create an admin cloud access configuration for the subscription that hosts the hub VNet you wish to peer with
- Use the
wf create cloudaccessconfigcommand with the--adminand--feature Provisioningflag to set up the configuration for the peering rule. - Apply the configuration with the
wf setup cloudaccessconfigcommand with the--applyand--adminflags to create the link.
Example:
wf create cloudaccessconfig --admin --name azure-vnet-hub -c azure -i abcdefgh-1234-5678-910-ij123456789k --default-region uksouth --org-id 12345678-1234-5678-1234-ab123456789c --feature Provisioning
wf setup cloudaccessconfig --apply --admin --name azure-nonprod-provisioning
Please observe the usage of the --name and -i values in the YAML examples that follow below.
2 - Connect the Wayfinder management network to all private clusters
---
apiVersion: networking.appvia.io/v2beta1
kind: PeeringRule
metadata:
name: management
spec:
filters:
allocation:
type: all
selectors:
matchExpressions:
- key: appvia.io/stage
operator: Exists
- key: networking.appvia.io/peering # only private clusters
operator: In
values: ["true"]
connection:
type: peering
peering:
enableAutoApproval: true
3 - Connect the private cluster networks into the hub for workspace wsk
apiVersion: networking.appvia.io/v2beta1
kind: PeeringRule
metadata:
name: hub
spec:
filters:
allocation:
type: workspace
workspaces:
- wsk
selectors:
matchExpressions:
- key: appvia.io/stage
operator: Exists
# Cloud account which has the permissions to accept peering
cloudAccount:
name: azure-vnet-hub <-- This value is from Step 1 above
namespace: ws-admin
connection:
type: peering
peering:
enableAutoApproval: true
network:
# the vpc identifier
identifier: <RESOURCE_GROUP/VNET_ID>
# the aws region of the network
location: eu-west-2
You can also define and manage peering rules in Wayfinder's web interface.
Route all traffic via the Hub
In the following yaml example:
- We want to hook up our networks into a centrally managed hub network.
- We want all traffic egress traffic via the hub network.
apiVersion: networking.appvia.io/v2beta1
kind: PeeringRule
metadata:
name: hub
spec:
filters:
allocation:
type: all
selectors:
matchExpressions:
- key: appvia.io/stage
operator: Exists
# Cloud account which has the permissions to accept peering
cloudAccount:
name: azure-vnet-hub <-- This value is from Step 1 above
namespace: ws-admin
connection:
type: peering
peering:
enableAutoApproval: true
network:
# is the subscription
account: abcdefgh-1234-5678-910-ij123456789k <-- This value is from Step 1 above
# the virtual network identifier
identifier: <AZURE_PEERING_DESTINATION_VNET_RESOURCE_ID>
providerDetails:
azure:
# indicates we want to use the hub as a gateway for all egress traffic
enableUseRemoteGateway: true